Author: Tom Garrison, VP & GM Client Security Strategy & Initiatives, Intel
Over the last four years, the industry has taken important steps to better protect components, servers, PCs, and IoT devices from cyberattacks. Top cloud service providers (CSPs) and OEM partners — including Lenovo, Dell, HPI, and Supermicro — as well as Chief Information Security Officers (CISOs) have embraced Intel’s Transparent Supply Chain (TSC) product. Their common goal: help ensure the integrity of platforms throughout their entire lifecycle, from manufacture to operation to retirement.
Today, security challenges have become more sophisticated and dangerous. So, it’s crucial to keep evolving how we view and strengthen these key industry supply chains. Spoiler: The key is to augment physical supply chain security with expanded digital supply chain security. Only then can we create Compute Lifecycle Assurance that is more resilient to attacks. For more on why and how, including an exciting new Intel initiative on vulnerability disclosure that we have just started talking about publicly, read on.
Evolution Of Complex Problems – And Solutions
Today’s cybersecurity landscape is all about evolution. Use cases and complexity have evolved. So has the sophistication of attackers. More bad actors are employing “adversarial AI” to maximize damage. (To learn more, check out our Cybersecurity Inside podcast with Dr. Diane Janosek of the National Security Agency, Abhilasha Bhargav-Spantzel, and Aanchal Gupta from Microsoft). And that is on top of the built-in complexity of modern device supply chains, where multiple parties can have vastly different security processes, tools, and abilities. All this greatly exacerbates and creates challenges. Topping the list: tamper-resistance, patching, asset tracking, and establishing provenance.
This new environment demands a new kind of protection. As always, it starts with physical supply chain security. The focus here is on securing facilities, employees, and trusted vendors. But that is only the start. That foundation is augmented with digital supply chain security. Here, digital transparency, traceability, trust, and resilience are key. These new capabilities expand supply chain protections to recording and tracking key device information, including manufacturing data and subsequent modifications across its lifecycle. Expanding the definition of security is crucial to assuring the security along the entire supply chain.
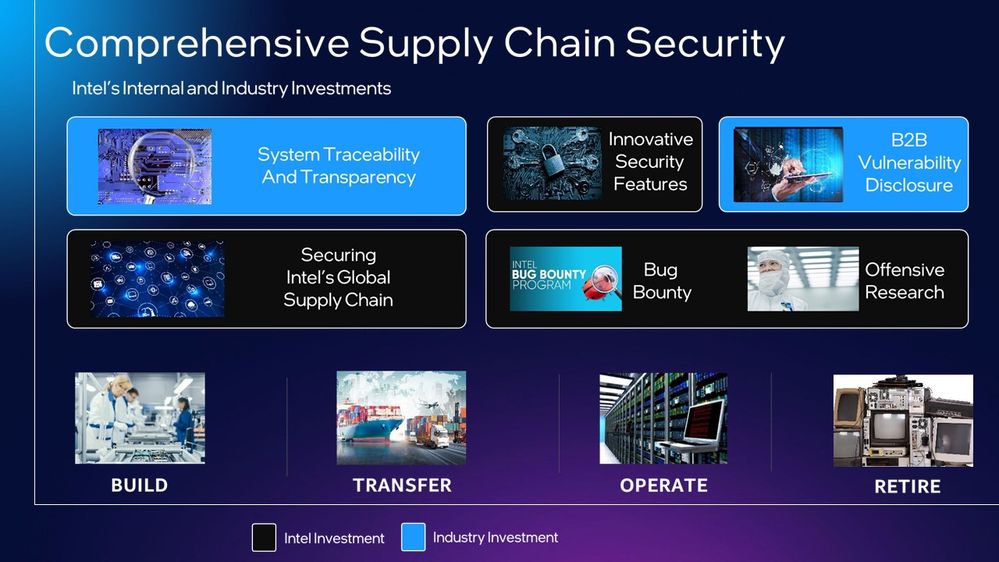
Intel’s supply chain security strategy has several elements. We will focus on the two that have the highest current importance. The first is system traceability and digital transparency. The second is B2B vulnerability disclosure. Let’s take a brief look at each.
System Traceability And Transparency
The goal here is to help ensure device and platform integrity through the build, transfer, operate, and retirement phases. Traceability and transparency help answer critical questions: What components were used to build my device? Can they be traced from the moment they were developed? Have all the patches and firmware updates been applied? In today’s world, if you can’t answer these key questions, you’re not as safe as you could and should be.
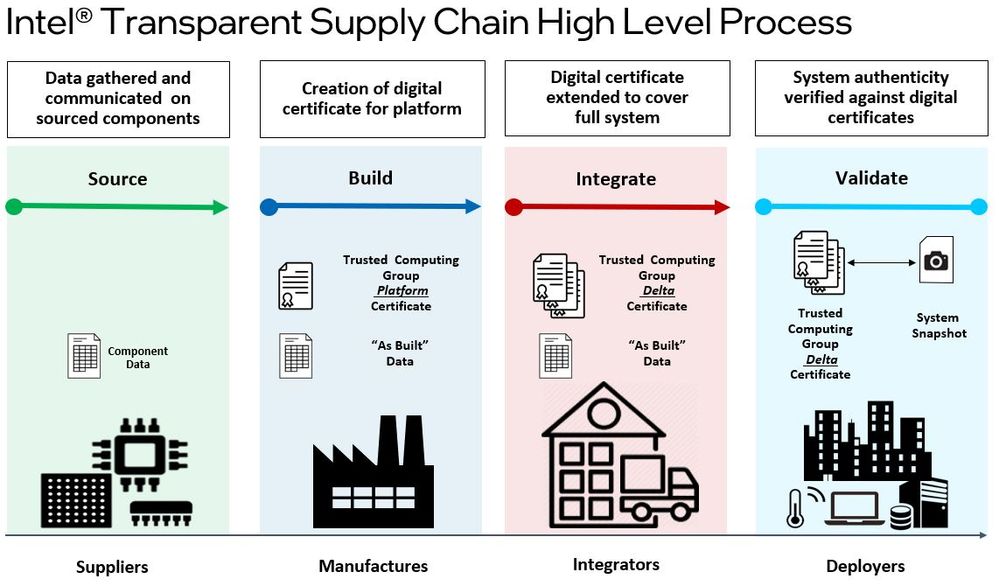
Intel has spent 50+ years creating the most complex things ever made by humans and supplying them to the industry every year in the millions. In the process, we have developed very strong competency in managing every dimension of supply chains. We introduced Transparent Supply Chain (TSC) in 2018. It includes the tools, policies, and procedures that give you visibility and traceability of hardware components, firmware, and systems.
TSC captures all the components used to build the device, whether it is a PC, server, or IoT device. Country codes, date codes, light codes, specific time of manufacture, you name it. An endorsement key from a Trusted Platform Module (TPM) on the machine lets you sign that data. We provide a capability for that specific machine’s data stored in a cloud. When the machine finally shows up, a user can run a check on their local machine and compare the results to what was stored at the time of manufacture. Has anything changed?
Today, TSC has been adopted by numerous leading industry partners. Dell is a great example. The company is working with Intel to leverage a suite of tools, ingredients, industry standards, and enterprise solutions to deliver even greater security. Its Secured Component Verification (SCV) is a fully compatible version of the Intel TSC. It is based on the same ability to know your platform, the same platform certificates, the same industry-standard base. The solution is commercially available, bringing customers strong capabilities today, especially in highly regulated markets like financial institutions, government, and healthcare.
B2B Vulnerabilities
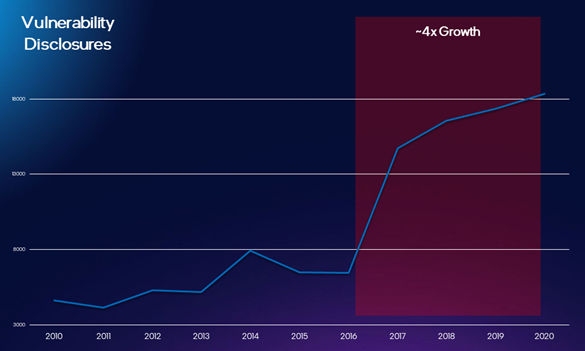
This is the second key element of digital protection. If you look back historically, the number of vulnerabilities found in the industry was relatively low and flat. Around 2017, a lot more appeared, roughly 4X. Some are a new class of side channel attacks. For its part, Intel made a huge investment internally to do security research. We publish a yearly Product Security Report. We are very transparent and public about everything we find. Whether it’s us, a partner, or somebody else, we will provide a mitigation, and publish it on Intel’s Security Center with information on the characteristics.
Source: https://www.cvedetails.com/browse-by-date.php
We want to make the consumption of these mitigations easier. Some people call that the “last mile” problem. We need to make it easier for people to say, “does this affect me?” Can the machine itself tell you if it is okay? These are the kind of environments we want to move towards, more like a B2B community communication. We are making significant progress.
We are making a substantial investment in this and partnering with key people in the industry. In the future, you will see announcements by Intel, just like when we were talking to the industry about transparent supply chain and how important it was before anyone was really talking about supply chain. This is the future: automation of manual tasks such as vulnerability awareness, and opportunities to remediate.
A Vision Of Digital DNA
Ultimately, we are building towards “Digital DNA” – a platform that at any point knows the key information you need to know. It is like what a human DNA test can reveal about ourselves. Why can’t we have the same kind of important information available about our servers, our PCs, our IoT devices?
Digital DNA would include things like authenticity, country of origin, current state of the device, and much more. If you can't answer those questions right away, ask yourself, “why not?” That information exists today; the tools largely exist today. We need to make them better. And that is what Intel is driving towards.
There is no way around it: We must adapt our supply chain strategies. We live in a different world today. We need to move to digital supply chains. We need to think about the device lifecycle, not just when it is first built, but over its life. And we need to make sure that we deploy the solutions that are available today. These are not all pie in the sky, “in the future” offerings. They are things that can be deployed, starting now, even as exciting new digital extensions are developed. The task now is moving from understanding to practice.
--
Notes & Disclaimers:
Intel technologies may require enabled hardware, software, or service activation.
No product or component can be absolutely secure.
Statements in this document that refer to future plans or expectations are forward-looking statements. These statements are based on current expectations and involve many risks and uncertainties that could cause actual results to differ materially from those expressed or implied in such statements. For more information on the factors that could cause actual results to differ materially, see our most recent earnings release and SEC filings at www.intc.com.
 Tom Garrison, VP & GM Client Security Strategy & Initiatives at Intel Corporation
An experienced executive leading Intel’s corporate-wide cyber security strategy and initiatives. Leads efforts to help customers and manufacturers deploy tooling and processes for greater security assurance, supply chain transparency and cyber security innovation roadmap. Launches industry-wide initiatives and research with ecosystem partners and academia to accelerate cyber security product assurance.
Tom Garrison, VP & GM Client Security Strategy & Initiatives at Intel Corporation
An experienced executive leading Intel’s corporate-wide cyber security strategy and initiatives. Leads efforts to help customers and manufacturers deploy tooling and processes for greater security assurance, supply chain transparency and cyber security innovation roadmap. Launches industry-wide initiatives and research with ecosystem partners and academia to accelerate cyber security product assurance.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.