Starting with a physical crime scene – a fire – Manon Fischer describes how IoT devices such as “smart” plugs and thermostats store “distant traces” remotely, and could be used to help reconstruct a fire’s origin, cause, and timeline.
Session Chair: So, after some intense network analysis, we all know it, we’re very hungry, we are starving, so we prepared ourselves some lunch. But our mind is still racing about all those IP addresses and domains and whatsoever, so that when we leave the building, we simply forget to turn off the oven.
And before we know it, the whole building’s on fire and destroys all digital evidence on site and to solve problems like these, Manon Fischer from the University of Lausanne is going to talk about distant traces and their use in crime scene investigations.
Manon: So hello, everyone. As he said, I’m Manon Fischer from the University of Lausanne in Switzerland. And today will be the first time I present this research in front of a lot of people. So I’m really happy to be here to share with you the first results I get.
Today, I would like to talk with you about a field that I think it’s quite interesting, complex, but also so prevailing. Every day we use our smartphone to send some messages on WhatsApp, to take pictures and put them on Instagram, or to just start the cleaning cycle of our robot vacuum cleaner, if you have one.
And all these events will generate some choices and these choices can be stored on their own servers, the remote servers. And so, I talk about distant or remote traces in this case.
But the main question is, can these traces can be useful for criminal investigation? And I decided to start my PhD a year and half ago to start to answer these questions and to know if these distant choices can be useful and or they can be used for criminal investigation.
I think the best way to start is just to show you a little example. And I think I would like to convince you that these choices can be just crucial for an investigation. And for this investigation, we start in this apartment, but a fire happens and so, there are not a lot of things that are still in the apartment.
And you are called as an investigator to just investigate the place. You can see that all of the apartment is burned and it’s difficult, near impossible to know what happened and to answer the two main questions you can have in a fire investigation. The first one, it’s about the origin and the cause of the fire, and the second one, it’s about the chronology of the fire. So you want to know how the fire develops in order to better understand the event.
But you are in this place, but a few weeks ago, you heard about the choices that can be generated by smart devices, and you think that in this case, it can be very helpful if you found some info. So you decided to interview the owner of the apartment to find out if some smart devices were present in the apartment during the fire.
And he told you that a smart weather station was in the main room where the fire happened. So now you know that you probably have some traces on this device. But also when you search the remains, you find this thing, it’s a little motherboard that is linked to a plug, so maybe it could be a smart plug. So now you have two devices to investigate and to find out if there are some traces on.
For those who participated in the poster session yesterday, it’s not the same case as he showed you, but it’s another one because we also set fire to another apartment to try to generate some traces. So it’s another type of trace, it’s not the same smart object as you can see.
But the main question now is, where is the digital evidence? Where do I have to look? You have three main places where you can find some digital evidence from the smart devices. You will find some information in the memory, also in the application on the smartphone that is linked to the smart devices, and mainly you will find some traces on remote servers because the IoT has a small amount of storage so they will send a lot of data outside on remote servers. So it’s quite important to study this part and it’s the aim of my presentation.
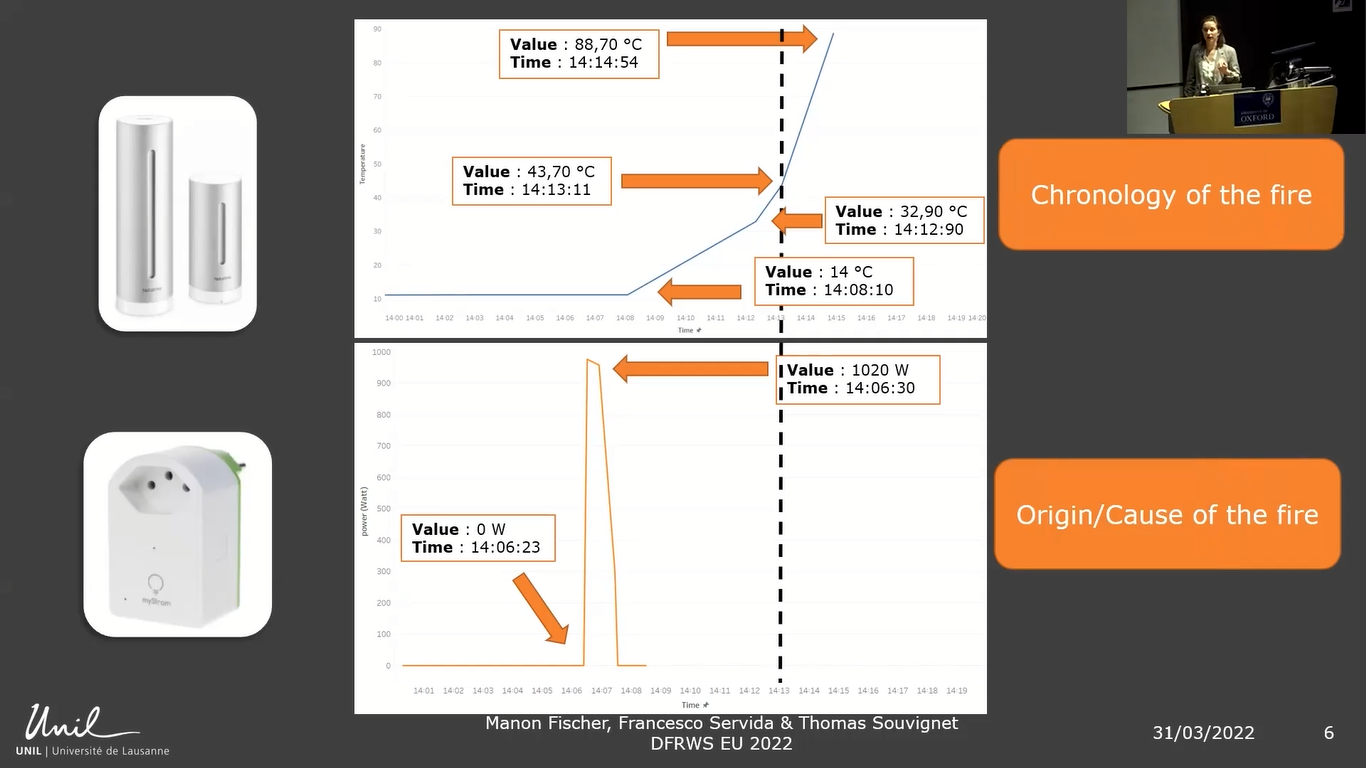
And to get these choices, we sent some legal requests to get them. And I will explain just after that how to do that. First, from the smart weather station, we obtain this data. It’s the temperature, the measure of temperature versus time. And you can see that the temperature increased from 14°C to almost 90°C in only six minutes. So with this observation, you can think that the fire started during this period of time. So now you have an idea of when the fire starts.
But now we will look at the smart plug data we get. In this case, we obtained the measure of the power versus time. And you can see that there is a sudden increase of the power from 0W to 1020W in only seven seconds. You can think that something was plugged into, and just consumed some electricity.
So you have these two bits of information and you can see that this increase of power is just a few minutes before the start of the fire. So now with these two elements, you can make the hypothesis that the fire started because of this increase in power.
So now you can just answer the two main questions asked before for fire investigation. The first one of the chronology of the fire, because you have an idea when it started, and after, you can have an idea of the cause that it’s probably electrical, and about the origin that it’s in the area of the plug or on the smart plug, or maybe the thing that was plugged into.
With this result, you can see that if you don’t think about the distant traces, you will miss something, and you can’t answer the two main questions. So it’s important to think about it when you are at a crime scene to consider them as part of the crime scene.
But I think now you want to know, oh, we collect the data in this case, because it’s what you want to know. The first step to do that is to know if some devices generate traces and can be collected. It’s what we do in this case, because we see that there are some smart devices at the crime scene.
And so you know that there are probably distant traces. After that you need to get some identifying information in order to do the legal request afterwards. The identifying information can be the identifier, like the email address or some information about the account, it can be information also for smart devices about the brand and model, and also of the serial number that identifies the object.
So it’s important to get these things also, and it’s important also to ask quickly for this data because this data can sometimes disappear. And so it’s important to just ask very quickly for this data to integrate them very quickly in the procedure.
And finally, about the legal request, in this case, we get the traces under the GDPR request because it’s our account so we can have access to our data, and it’s why we use that. I used that for this research because it’s easier to have an idea of the traces that can be generated. But you cannot use it for investigation purposes. So it’s only for the moment for research to have easy access to the data and to have a better idea of the choices you can find on this account.
For the law enforcement request, you have two ways to do it, but I will only talk about what is happening in Switzerland, because I don’t know yet everything that happened in the other country. And in Switzerland, it depends on where the data is stored and where the servers are. You will not do the same request.
So if the data is stored on servers in Switzerland you will do a Swiss request to be simple, and if it’s not, you have to do your request under the international mutual legal assistance to get the data.
But there are some limitations to this work. Something that is more complex is that as I told you, the regulation will depend on the country where you are. So for the moment, I can’t explain to you all this work for the other country, but maybe in the continuing of my work, I will just go deeper in that.
And when you obtain the data, you will receive the data in multiple file formats. So you will have some CSV, JSON, TML, not complicated file formats because all of us can read them, but it’s sometimes difficult to put all this data together to have unique information.
To continue my work, I would like to also consider the social media data that can also generate some distant traces. And that can be also very useful, it depends on the investigation where you are. Also, the smart devices, I think I will continue to study more for this type of object, because as you see, it’s quite important.
And there are a lot of things to do. I don’t know if we plan to burn another apartment, but yes, we will see. And also, I would like to combine my work, the content I get from the law enforcement request, and from my personal data request to see if there are some differences between the two of them. And so I work with the police now to do that to have a better understanding of that.
And finally, I would like to implement something about the visualization to give to the investigator. For example, adjust a graph that it’s simple to read, to understand because they don’t want to go in to look at the JSON files, but they want to have an explanation, a timeline of what happened that is easier to read.
I would like to conclude my work on that slide. We considered just a crime scene with just traditional traces as DNA fingerprints or shoe prints. That is quite normal, but for a few years now, we’ve also added digital evidence from crime scenes.
But now, we also have to consider the distant traces as part of the crime scene investigation. We have to extend this crime scene, not only on what you can see at the crime scene, but with all the choices that can be also outside of the crime scene.
These distant traces, or remote traces, can be very useful for a lot of investigations as missing person cases; for robbery, for fire, as I showed you with with my example; but also for murder.
And this is the case for the Jubillar case that happened in France. I think in 2020, a woman disappeared and her husband is the main suspect of the case. And the French police decided to ask Google to provide his location history, to know if he was the murderer and also to find maybe the body of the woman. As this data is stored on Google’s server in the US, a judge asked to order Google to send this data by international mutual legal assistance, as I told you just before.
I would like to thank you, the FAU for the scholarship they gave me to participate in the Woman in Forensics and also to the DFRWS. It gives me the opportunity to just present to you my work, so thank you for that. And if you have any questions, I’m here.
Session Chair: Thank you very much. And as usual, any questions from the audience here or on Zoom?
Audience Member 1: Thank you for the talk. How confident are you and do you get some information from the providers on what fields are given? I’m asking especially for time stamps. Like, do they tell you the time from the device or the time where the event was received on the server or this kind of information?
Manon: It’s quite complicated to know what data they send to us and why sometimes we have some data and why sometimes we have no data, because when we generate the traces, we expect some data and sometimes we don’t get that, but I don’t have any explanation.
Sometimes when you do some requests, they send you in the best case, an explanation of what is this information in the CSV file, for example, but it’s not the majority of the cases, and sometimes you just have to guess what it is, and yeah.
Session Chair: Do you want to continue? You do? Okay. Thank you. I saw there’s one more question in the chat.
Moderator: Yeah, we have several questions in the chat. This is exciting. Yeah, so the first question is from Christian Mueller. He asks, ”Did you try to get information from Alexa and the like before? If so, what kind of data did you get?”
Manon: I tried once, but just to do some experiments, it’s not just a full experiment. And I get some audio from the commands I send to Alexa, but not all the commands I send. So that’s why I don’t understand if they have the data or if the data recorded, I don’t know, but yeah, I obtained these traces.
Moderator: Brilliant, thank you. And we have another question. Did you try to fetch some data from the burnt devices?
Manon: On the memory use?
Moderator: Yeah, I imagine on the ROM or RAM chip.
Manon: We can add some information into the memory of the device, but it’s not my work, it’s the work of Francesco Servida because we split our work. It’s better for that. And so we can find some information, but it’s difficult to read the memory and after, to understand also the structure of the data into the memory. So we tried that. The main problem also is to recognize the object under the crime scene and after to read the data.
Moderator: Great. Thank you very much.
Session Chair: Perfect. If there are no more questions, I’ve got one. You were talking about how to collect the evidence and you were saying you have to ask quickly because it can disappear. So my question would be, from what you’ve seen so far, is it possible for people, because you’re the owner of these devices, to delete the data on the remote servers, or is that something which is not possible?
Manon: Yeah, it’s possible. With the GDPR regulation, it authorizes you to have a look at your data, to modify your data, and also to delete your data. So it’s possible to lose this data by this way, yeah.
Session Chair: Okay. Thank you very much. Cool. Thank you.