
A cryptomining hacking group has been observed exploiting the recently disclosed remote code execution flaw in Atlassian Confluence servers to install miners on vulnerable servers.
The vulnerability, tracked as CVE-2022-26134, was discovered as an actively exploited zero-day at the end of May, while the vendor released a fix on June 3, 2022.
Various proof of concept (PoC) exploits were released in the days that followed, giving a broader base of malicious actors an easy way to exploit the flaw for their purposes.
One of the threat actors who took advantage of this offering is a cryptomining group called the “8220 gang,” who, according to Check Point, perform mass net scans to find vulnerable Windows and Linux endpoints to plant miners.
Miners are special-purpose programs that use the host’s available computational resources to mine cryptocurrencies like Monero for the threat actor.
The direct consequence of this activity is reduced server performance, increased hardware wear, increased running costs, and even business disruption.
Additionally, by having access to the system, these actors can upgrade their attack anytime and drop more potent payloads.
8220 gang Attack chain
The attack begins on both Linux and Windows systems by sending a specially crafted HTTP request that exploits CVE-2022-26134 and drops a base64-encoded payload.
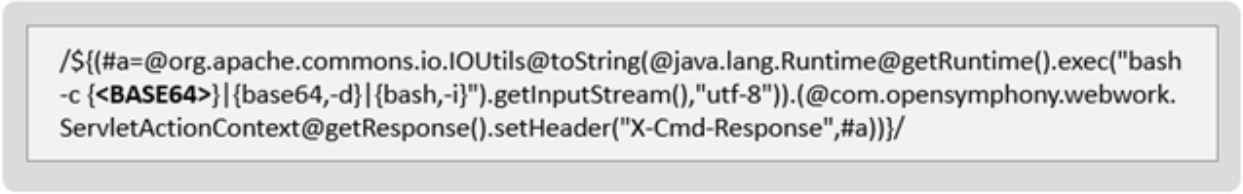
Next, the payload fetches an executable, a malware dropper script on Linux, and a child process spawner on Windows.
Both cases aim to establish reboot persistence (via cron jobs or startup folder), uninstall all running agents, and then activate the miner.
.png)
In both cases, the miner will exhaust all system resources, so the “8220 gang” is going for maximum profit until their malware is uprooted instead of silently mining on compromised servers and striving to stay undetected by using only part of the available computational power.
Finally, the Linux script also searches for SSH keys in the host to attempt to spread to adjacent machines on the breached network.
Confluence RCE exploitation
While the “8220 gang” exploits CVE-2022-26134 for cryptomining, other threat actors are installing web shells, creating new admin accounts, executing commands, and even taking complete control of the server.
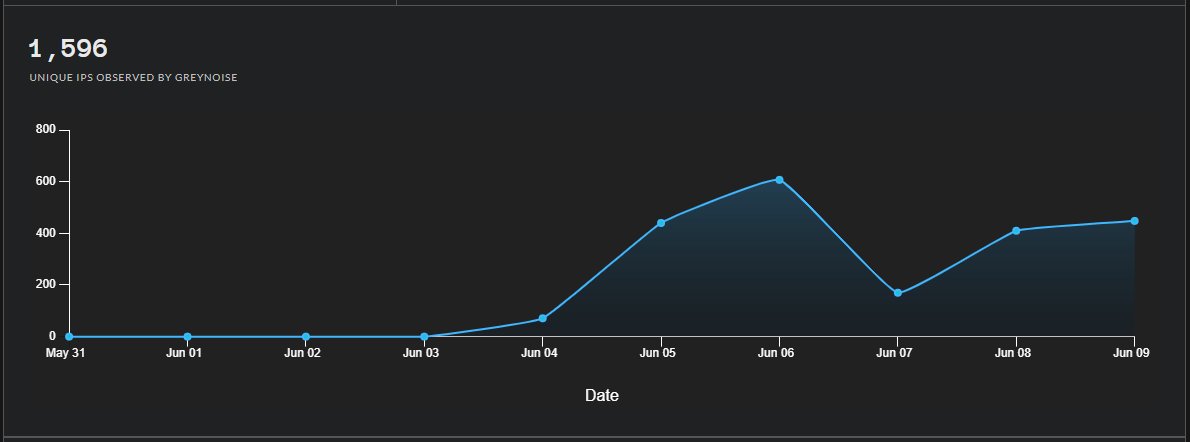
According to Greynoise data, the exploitation attempts peaked on June 6, 2022, but the detection of malicious attempts continues at high levels today.
Linux botnets, such as Kinsing, Hezb, and Dark.IoT, are also exploiting the vulnerability to deploy backdoors and cryptominers.
Atlassian has warned its customers that the only mitigation for the critical flaw is to apply the security updates, which have become available in versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4, and 7.18.1.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now