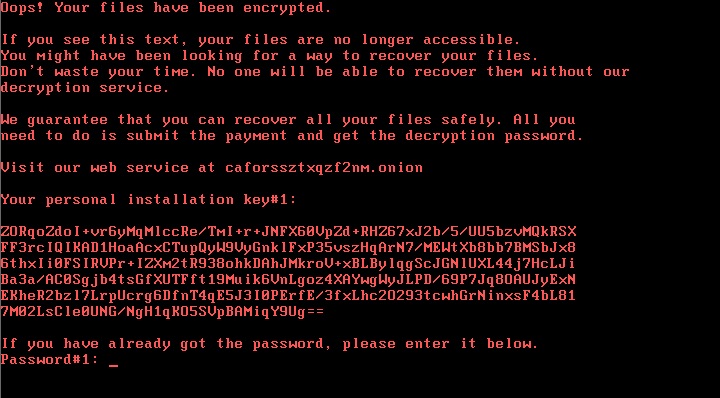
A new, potentially virulent wave of data-encrypting malware is sweeping through Eastern Europe and has left a wake of outages at news agencies, train stations, and airports, according to multiple security companies Tuesday.
Bad Rabbit, as the outbreak is being dubbed, is primarily attacking targets in Russia, but it's also infecting computers in Ukraine, Turkey and Germany, researchers from Moscow-based Kaspersky Lab said. In a blog post, the antivirus provider reported that the malware is using hacked Russian media websites to display fake Adobe Flash installers, which when clicked infect the computer visiting the hacked site. Researchers elsewhere said the malware may use other means to infect targets.Bad Rabbit appears to specifically target corporate networks by using methods similar to those used in a June data-wiping attack dubbed "NotPetya" that shut down computers around the world. Bad Rabbit infects Windows computers and relies solely on targets manually clicking on the installer, Kaspersky Lab said. So far, there's no evidence the attack uses any exploits.
Russia's Interfax news agency reported on Twitter that a hacker attack has taken out some of its servers and forced it to rely on its Facebook account for the time being. Russian forensics firm Group IB said Bad Rabbit has infected two other Russian media outlets besides Interfax. In nearby Ukraine, computer systems for the Kiev Metro, Odessa airport, and Ukrainian ministries of infrastructure and finance have also been affected, according to a blog post published Tuesday morning by antivirus provider Eset. Meanwhile, the Ukrainian computer emergency agency CERT-UA also posted an advisory on Tuesday morning reporting a series of cyberattacks, without specifically naming the malware used in those attacks.
Preliminary analysis indicates the malware is professionally developed and incorporates a variety of advanced measures designed to allow it to rapidly infect large government and corporate networks. Security researcher Kevin Beaumont said on Twitter that Bad Rabbit uses a legitimate, digitally signed program called DiskCryptor to lock targets' hard drives. Kaspersky Labs' blog post said the executable file dispci.exe appears to be derived from DiskCryptor and is being used by Bad Rabbit as the disk encryption module.
Beaumont went on to say that Bad Rabbit relies on hard-coded credentials that are commonly used in enterprise networks for file sharing and takes aim at a particularly vulnerable portion of infected computers' hard drives known as the master boot record. A malicious file called infpub.dat appears to be able to use the credentials to allow the Bad Rabbit to spread to other Windows computers on the same local network, Kaspersky Labs' blog post added. In a second blog post, Eset said the malware also uses the Mimikatz network administrative tool to harvest credentials from the affected systems.

The outbreak is the latest reminder that people should back up all their data on drives that are secured with a password or other measure to protect them from ransomware. Microsoft has provided some useful guidance here network administrators can follow to protect their organizations against Bad Rabbit.
This post was updated repeatedly to add new details as they became available.
Listing image by Wired UK/Shuttershock
reader comments
57