A new bootlocker ransomware was discovered by Malware Blocker called RedBoot that when executed will encrypt files on the computer, replace the MBR, or Master Boot Record, of the system drive and then then modifies the partition table in some manner.
As the ransomware does not provide a way to input a key to restore the MBR and partition table, unless the ransomware developer has a bootable decryptor this malware may be a wiper.
The RedBoot Encryption Process
When the RedBoot ransomware, which is a compiled AutoIT executable, is executed it will extract 5 other files into a random folder in the directory that the launcher was executed. These files are boot.asm, assembler.exe, main.exe, overwrite.exe, and protect.exe and are described below.
assembler.exe - This is a renamed copy of nasm.exe that is used to compile the boot.asm assembly file into the master boot record boot.bin file.
boot.asm - This file is an assembly file that will be compiled into the new master boot record.
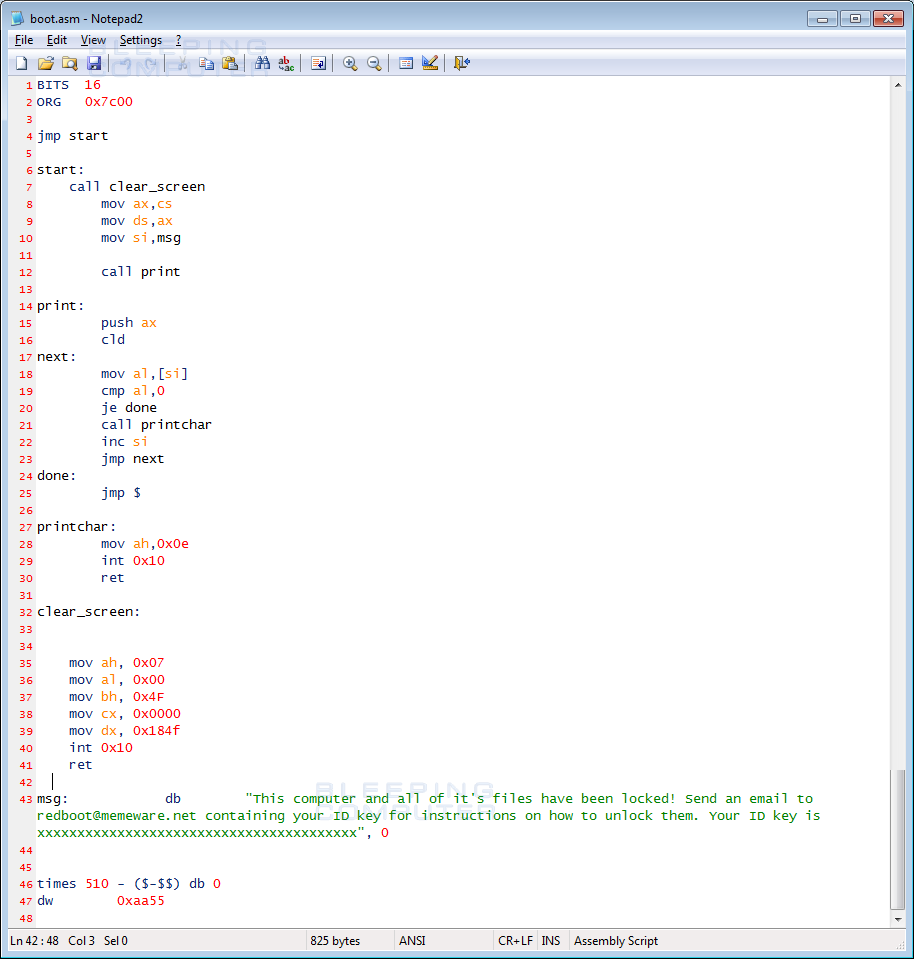
boot.bin - When the boot.asm has been compiled by assembly.exe, it will generate the boot.bin file.
overwrite.exe - This program is used to overwrite the existing master boot record, or MBR, with the newly compiled boot.bin.
main.exe - This is the user mode encrypter that will encrypt the files on the computer.
protect.exe - This executable will terminate and prevent various programs from running. This includes task manager and processhacker.
Once the files are extracted, the main launcher will now execute the following command to compile the boot.asm file into the boot.bin file.
[Downloaded_Folder]\70281251\assembler.exe" -f bin "[Downloaded_Folder]\70281251\boot.asm" -o "[Downloaded_Folder]\70281251\boot.bin"
Once boot.bin has been compiled, the launcher will delete the boot.asm and assembly.exe files from the computer. It will then use the overwrite.exe program to overwrite the computer's current master boot record with the compiled boot.bin using this command.
"[Downloaded_Folder]\70945836\overwrite.exe" "[Downloaded_Folder]\70945836\boot.bin"
The launcher will now start the main.exe program, which will scan the computer for files to encrypt. The main.exe program will also launch the protect.exe program in order to block programs that may be used to analyze or stop the infection.
While main.exe is encrypting files, it will encrypt executables, dlls, and normal data files and append the .locked extension onto each encrypted file's filename.
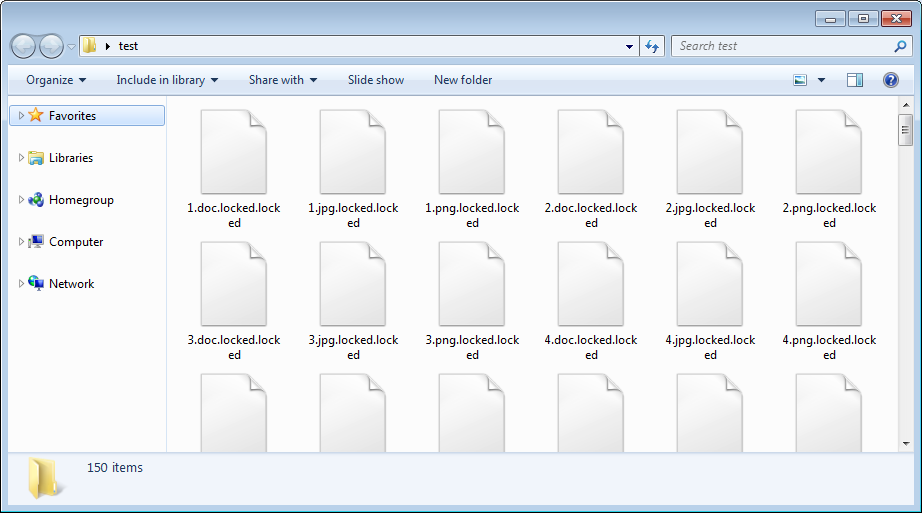
When it is done performing the file encryption, it will now reboot the computer and instead of starting Windows, will instead display a ransom note being generated by the new master boot record.
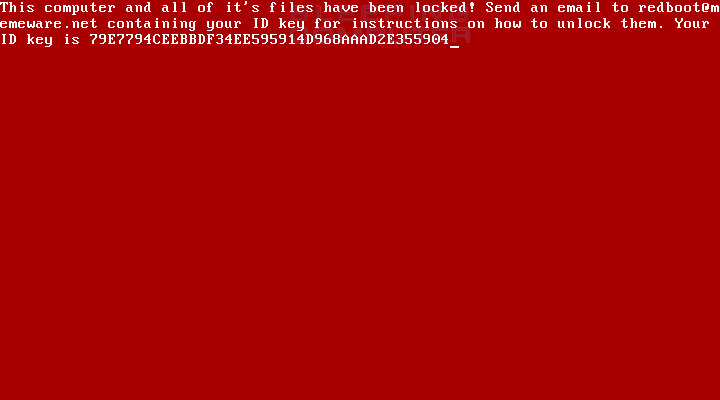
This ransom screen will instruct the victim to send their ID key to the developer at redboot@memeware.net in order to get payment instructions.
While this ransomware is brand new and still being researched, based on preliminary analysis it does not look promising for any victims of this malware. This is because in addition to the files being encrypted and the MBR being overwritten, preliminary analysis shows that this ransomware may also be modifying the partition table without providing a method to restore it.
This means that even if the victim contacted the developer and paid the ransom, the hard drive may not be recoverable. As this ransomware is further analyzed, if anything changes with this analysis I will be sure to update the article.
Is it a buggy ransomware or a wiper?
While this ransomware does perform standard user mode encryption, the modifying of the partition table and no way of inputting a key to recover it, may indicate that this is a wiper disguised as a ransomware. Then again, since the developer used a scripting language like AutoIT to develop this ransomware, it could very well be just a buggy and poorly coded ransomware.
So is this just a buggy ransomware or wiper disguised as one? Hard to tell unfortunately, but after viewing Memeware.net, I am leaning towards the former.
UPDATE [September 29, 10:02 ET]: The developer of RedBoot contacted BleepingComputer and stated that the sample I analyzed is a developement version and new version will be released in October.
IOCs
RedBoot Hashes:
Installer: 1001a8c7f33185217e6e1bdbb8dba9780d475da944684fb4bf1fc04809525887
boot.bin: 2ae74130ac809fb54f12e72f589069ad7b5e1f56e68cee00db8867b02112c4b9
main.exe: 1001a8c7f33185217e6e1bdbb8dba9780d475da944684fb4bf1fc04809525887
overwrite.exe: f2bc5886b0f189976a367a69da8745bf66842f9bba89f8d208790db3dad0c7d2
protect.exe: e61a8382f7293e40cb993ddcbcaa53a4e5f07a3d6b6a1bfe5377a1a74a8dcac6
assembler.exe: 2a5305369edb9c2d7354b2f210e91129e4b8c546b0adf883951ea7bf7ee0f2b2
RedBoot Files:
[Downloaded_Folder]\[random]\assembler.exe
[Downloaded_Folder]\[random]\boot.asm
[Downloaded_Folder]\[random]\boot.bin
[Downloaded_Folder]\[random]\main.exe
[Downloaded_Folder]\[random]\overwrite.exe
[Downloaded_Folder]\[random]\protect.exe
Redboot Emails:
redboot@memeware.net
RedBoot Ransom Note:
This computer and all of it's files have been locked! Send an email to redboot@memeware.net containing your ID key for instructions on how to unlock them. Your ID key is 79E7794CEEBBDF34EE595914D968AAAD2E355904


Comments
Sadi90 - 6 years ago
Great article Lawrence, I work in a large scale organisation where we handle a lot of customer data. Ransomeware is something we really need to be secure against. would you have any advice on a good ransomeware protection solution for large organisations? I've heard of <a href="http://www.ivanti.co.uk">Ivanti</a> and know people within the business that have used their solutions and are happy with it, is there any recommendations you would make?
Demonslay335 - 6 years ago
The files are decryptable, but the bigger problem is recovering the files in order to decrypt them since the partition table is destroyed.
Amigo-A - 6 years ago
Typically, MBR can be easily restored.
Files can be restored by recovery programs, regardless of the damaged MBR.
Lawrence Abrams - 6 years ago
Partition table is trashed in this case.
Amigo-A - 6 years ago
The partition table is also restored - this is in most possible cases of damage. New cases of damage to the partition table have not yet been invented.
Lawrence Abrams - 6 years ago
I am not sure what you mean. Restoring the MBR in this case does not fix the partition table.
Amigo-A - 6 years ago
Data can be recovered even if the MBR is killed, even if the partition table is killed.
You can write a new MBR - it's easy.
You can restore the partition table after crash. There are programs that define the sections that were before the breakdown and recreate them.
Amigo-A - 6 years ago
This is the standard practice of data recovery. New cases of damage to the partition table have not yet been invented.
Lawrence Abrams - 6 years ago
Restoring mbr was not the problem. Have some example programs to repair/restore/replace the partition table? Would like to test this.
Amigo-A - 6 years ago
Gpart
TestDisk
Parted Magic
Partition Wizard
EaseUS Partition Table Doctor, EaseUS Data Recovery, EaseUS Partition Manager, EaseUS Partition Master ...
All will not list.
There are Freeware and Shareware.
Amigo-A - 6 years ago
http://www.geekyprojects.com/storage/how-to-repair-a-damaged-partition-table-or-mbr/
this is as minimum
Lawrence Abrams - 6 years ago
Thanks..will give it a test.
ChrisN98 - 6 years ago
Can you use bcdedit and bootsect through with a repair CD to fix the mbr and partition table or has anyone tested GParted or other third party tools?
Amigo-A - 6 years ago
Yes. Using repair special CD / DVD / USB with repair utilities is the most preferred variant. Another variant is to connect the affected Disk to another computer as secondary Disk.
This is standard practice.
Stretch_911 - 6 years ago
It seems to me that the development of wipers disguised as Ransomware is entirely counterproductive to the expansion of Ransomware effectiveness and profitability. Adding even more doubt to the ability to recover data will make victims far less likely to pay the ransom. Because of that, new developments like this or like the NotPetya family seem to be contributing more to killing Ransomware than expanding it, which is actually good for users. When it no longer becomes profitable, it will die, and wipers disguised as Ransomware are destroying the profitability. This is a perfect example of cyber-criminals shooting themselves in the foot or sabotaging the rest of the Ransomware underground.
Occasional - 6 years ago
You make some valid points; but the cyber economy and ecology are complicated, perhaps even complex.
Your projections for some combinations of attacker and victim categories make sense; and that would lead to an average reduction in high payoff attacks.
What you might see are more numerous attacks, with lower ransoms to the point where they are seen as a nuisance; and cheaper to pay than to fight (like settling out of court).
With spectrums of sophistication, motivation and available resources for both attackers and victims, the players will change, but ransomware will almost certainly persist.
1ntgr - 6 years ago
Thanks for the article. I was having a look at the installer.exe and there is mention of the FtpOpenFile function - do you know what it is used for?