Faxploit: Breaking the Unthinkable
- In ground breaking research, dubbed ‘Faxploit’, Check Point researchers show how cyber criminals could infiltrate any home or corporate network by exploiting all-in-one printer-fax machines.
- A fax number is the only thing required to carry out the attack.
- HP all-in-one printer fax machines were used as the test case, and close cooperation with the company ensured a patch for the vulnerability was provided for their products, but similar attacks could apply to other vendors as the vulnerability lies in the fax protocol itself.
See a full Q&A on this research
The ‘Modern Day’ Fax Machine
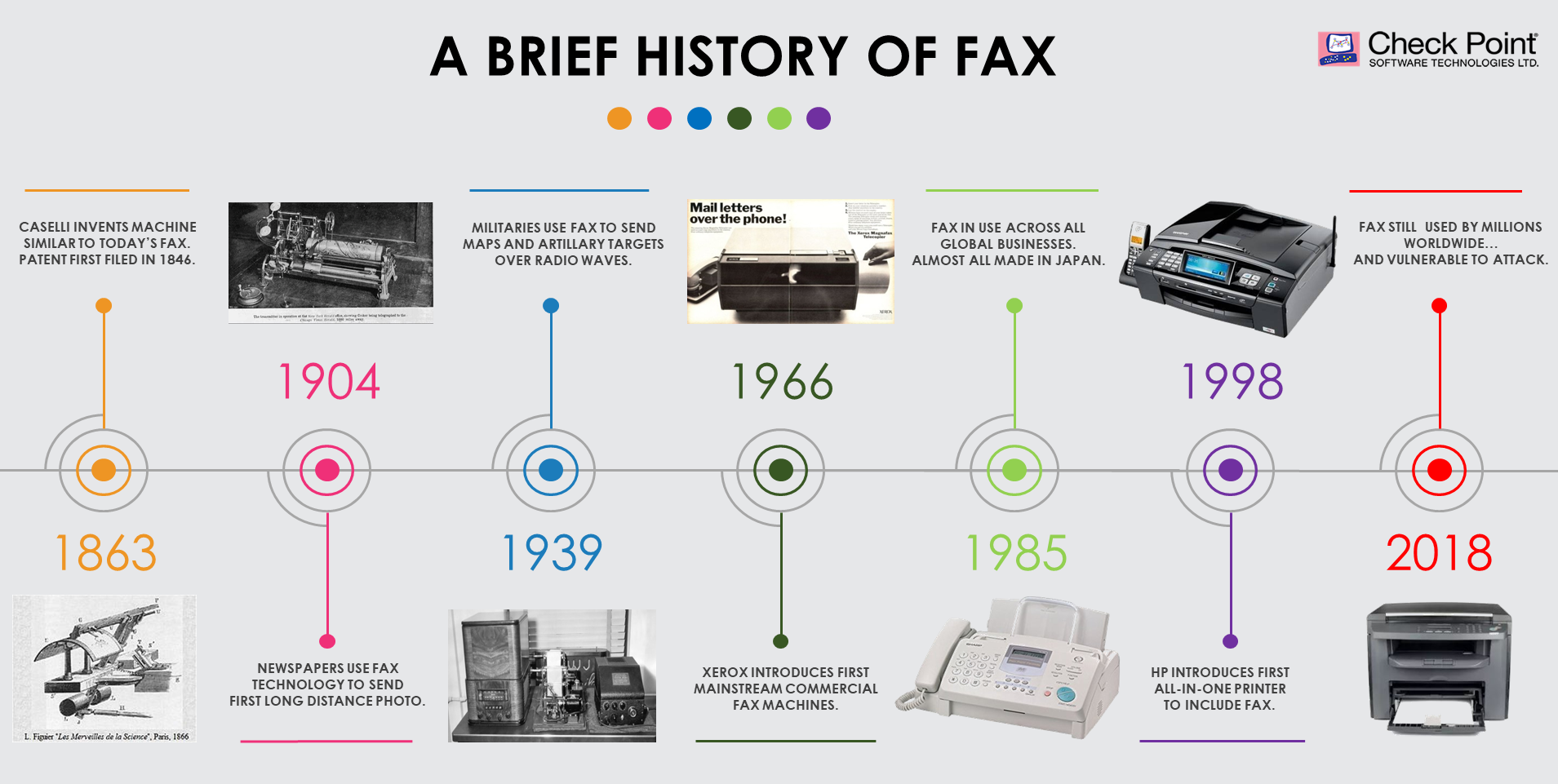
Which was invented first, the telephone or the fax machine? If you guessed the former, then try again. And if you’re surprised by that, imagine how surprised Napoleon III was when he witnessed the first demonstration of fax technology back in 1860.
Building on Alexander Bain’s synchronization of two moving pendulums through a clock in 1846 and later Frederick Bakewell’s synchronized rotating cylinders, the Italian physicist, Giovanni Caselli, was able to solve the biggest issue in image transmission – how to synchronize two machines in different locations. His outcome, the Pantelegraph, was the invention that many believe to the ancestor of today’s modern fax machine.

Sorry, did you just say ‘today’s modern fax machine’? Standing on the other side of this time scale in an age of AI, IoT and other hi-tech acronyms, you would be forgiven for thinking that fax machines are a relic of the ‘90s. However, this ‘outdated technology’ should not be overlooked in today’s modern IT environment, especially from a security perspective.
In a ground breaking new discovery, dubbed ‘Faxploit’, Check Point researchers illustrate how organizations of all sizes, as well as consumers, could be exposed to infiltration by hackers looking to exploit vulnerabilities in fax machine communication protocols. Furthermore, and perhaps more worryingly, the only information required to do this is the organization’s fax number – something which is often publicly available on any employee’s business card or company website.
This alarming research was carried out on HP fax machines, however the same fax communication protocols are used by other fax machine vendors and our team of analysts has every reason to believe the same exploit can be applied to fax machines of other vendors. Our research team worked closely with HP to collaborate on providing a patch, which has already been rolled out as an automatic update to the majority of their customers. Other fax and all-in-one printer-fax manufacturers, however, may still be exposed.
Compared to the past, when fax machines were standalone devices, today they are one of the components in all-in-one office equipment to combine fax, printers and photocopiers altogether. Indeed, these multi-functional devices are part of almost every organization, company or home’s internal IT network, and even if they are primarily used only as a printer their fax functionality is still enabled.
With merely a fax number as its sole piece of information, however, our team of researchers was able to penetrate though the vulnerabilities inherent in the fax protocol to gain access to an entire IT network. This presents a completely new attack vector in the fifth generation of the cyber threat landscape from which cyber criminals could launch an offensive, targeting industries that hold even the most protected data.
While this research focused on all-in-one printer fax machines, the same communication protocols apply to all fax machines from all vendors, and the same vulnerabilities likely lie in these devices too. In addition, as popular online fax services, such as fax2email, are using the same protocol the same vulnerability may well also apply there too.
How Printer-Fax Machines Expose Your Network
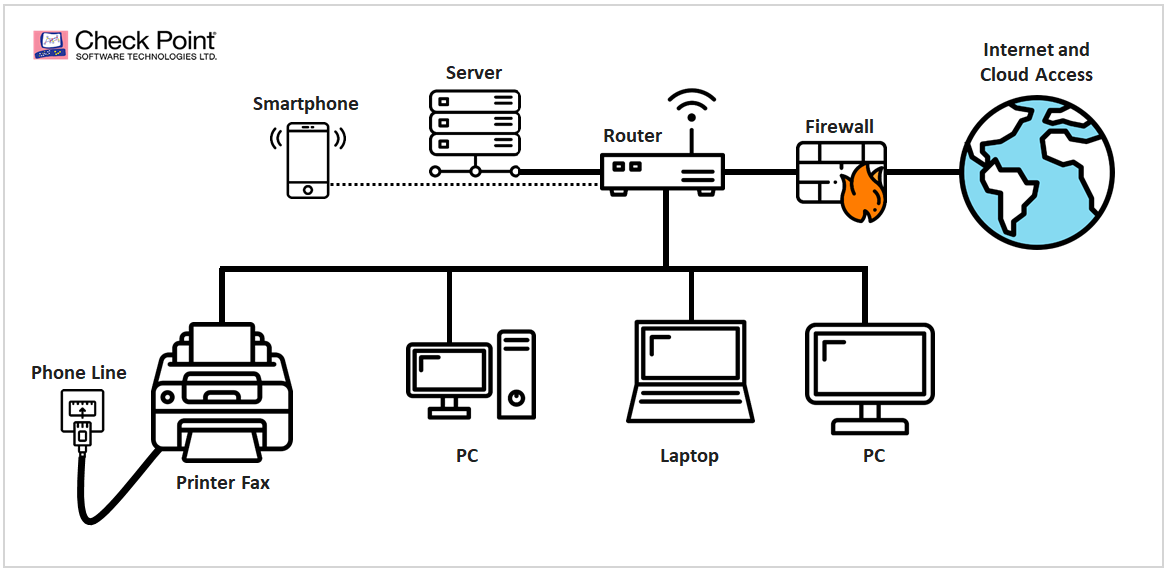
Looking at the basic network layout of a corporation, it is clear how exploitation of a printer-fax device could lead to a conquest of the rest of your IT network. Indeed, unfortunately, most organizations set up their IT infrastructure based on business and operational needs rather than security considerations and requirements. It is important to note, though, that our research holds true even in networks that are completely disconnected from the Internet. This is due to the leveraging of telephone lines rather than the internet itself to carry out the attack.
Diagram: A standard corporate IT network
To explain, if all are connected to the printer-fax machine, and, in turn, all of them are connected to one another, then an attacker need only to penetrate one access point (in this case the printer-fax) in order to enter the entire corporation’s network. From this point, through a process of lateral movement, the attacker would be able to hop from one part of the network to the next infecting a wider portion of it as he progresses. Upon such an attack, it would be a matter of seconds before an entire network was compromised and you had an intruder well embedded across your systems.
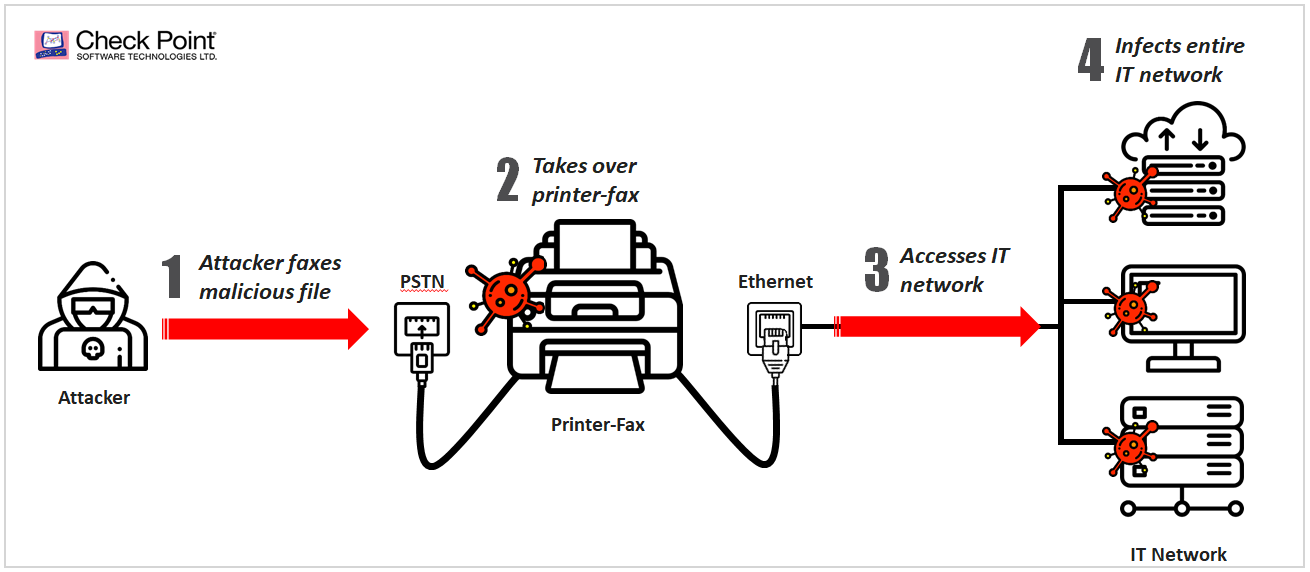
The below diagram shows the Faxploit attack flow, following which a threat actor could then move laterally across your network to access your organization’s most confidential information. The crucial element to notice is that whereas most attacks today penetrate through an internet connection to enter an organization’s network, using this vulnerability in the fax protocol even a network that is completely detached would be vulnerable. This is due to the attack being channeled through a route that until now was considered to be secure and need not have protection layers applied.
Diagram: The Flaxploit Attack Flow
The video that follows provides a technical demonstration of how our researchers carry out an attack, using nothing more than a fax number to infiltrate a computer and steal a private document.
Video: Faxploit in action
Of course, theft of computer documents is just one option for an attack and there are many others. These could include sending a copy of every fax that a customer sends to their bank, for example, with sensitive account information included, back to the attacker. Another possibility could be tampering with the fax content itself (i.e. replacing the documents received with altered versions of them). With a little imagination it is not hard to think of many nefarious ways that intervening in this form of communication could benefit a threat actor looking to profit from this vulnerability.
Who Uses Fax Anyway?
Despite advanced communication applications and technologies, there are currently around 46.3 million fax machines still in use, with 17 million of them in the US alone. Surprisingly, in some countries that are at the forefront of technology, like Japan, there is a particular affinity for the fax machine, with 100% of its businesses and 45% of private homes still owning a fax machine.
In the 1990s, sending faxes was part of the daily office frustrations. Whether they be frequent paper jamming, multi-feeding or streaky images, many professionals were super frustrated by the daily grind of using fax machines. But who is still willing to put up with these drawbacks today?
Well, the Healthcare industry, for one, governed by HIPAA regulations, is still a big player in sending faxes and the main customer of worldwide fax sales. In fact, according to a recent report, the UK’s NHS is world’s biggest buyer of fax machines. According to HIPAA, documents transmitted between doctors, labs and insurers have to be secure, which, over time, has been interpreted to mean primarily through the use of fax.
In addition, the Legal Industry argues that fax machines offer legal professionals convenience when sending documents to clients and confirmation that the message was received. In many countries email is not even considered an official form of evidence in courts of law, so fax is the preferred communication method.
Other areas that rely on fax to administrate the delicate handling of written signatures on documents are the Banking and Real Estate sectors. In fact, in some countries regulations even dictate that faxes are required to handle these processes.
And finally, although the use of fax machines fell with the massive spread of computers and smartphones, baby boomers who are not as familiar with newer technologies allows for the continued prominence of fax usage among consumers in general.
So, while the use of fax machines has in general radically subsided over the last 15 years, due to the rise of email and other electronic communication applications, it is still very much the norm for many industries who consider it a more secure or legally binding form of doing business. In addition, the presence of fax machines in both the home and work place is still very much prevalent, regardless of how often they are actually used.
The Security Risk
Although fax machines are still being used by many organizations, until now it was not considered a potential attack channel by threat actors.
In the fifth generation cyber threat landscape, though, this groundbreaking research highlights a brand new attack vector available for hackers to reach a corporate network and pose a risk to an organization’s IT security. Ironically, of course, the vector is from previous generations of technology, but one which, as we have seen, is still in use by millions of organizations and individuals worldwide.
Recommendations for Staying Secure
One of the best ways to protect your organization from attacks that could come from fax machines, and many other types of attack is through the segmentation of your network.
Unfortunately, due to the high operational demands placed on a business, most enterprises overlook many IT security practices and lack properly defined segmentation policies. This means that once a threat actor has penetrated your perimeter defenses, they can roam freely within your network. This can help them with reconnaissance activity as they prepare for a secondary stage of their attack that could involve stealing sensitive company data or locking down your entire network with ransomware. Indeed, with limited security controls in place, there is very little work an attacker need do to exploit these gaps.
 Network segmentation, however, is a key security strategy that aims at closing these gaps. It is a policy that should be implemented to minimize the level of access to sensitive information for those applications, servers, and people who don’t need it, while enabling access for those that do. Once unauthorized access is gained, network segmentation can provide effective measures to mitigate the next stage of intrusion into a network and limit the spread of the attack by lateral movement across it.
Network segmentation, however, is a key security strategy that aims at closing these gaps. It is a policy that should be implemented to minimize the level of access to sensitive information for those applications, servers, and people who don’t need it, while enabling access for those that do. Once unauthorized access is gained, network segmentation can provide effective measures to mitigate the next stage of intrusion into a network and limit the spread of the attack by lateral movement across it.
So, if you do not want to disconnect your printer-fax machine then at least make sure it is placed in a segmented area. By doing this, even if it does become compromised the attacker will not be able move laterally and infect other parts of your IT network.
The segmentation of where critical data is stored, whether by firewalls or configuring VLANs, requires planning, measured deployment and constant adjustments. Although this demands discipline and regular attention, and can become an unwieldy task as your organization’s network grows, it is not so overwhelmingly challenging, however, that it should be ignored altogether.
The Faxploit vulnerability also illustrates how important it is for organizations and consumers alike to regularly update and patch the software installed on their devices. In this way they will gain the protections provided by vendors that become aware of security flaws in their products.
Furthermore, having endpoint protections deployed across users’ devices goes a long way to mitigate the risks of unauthorized access. By installing endpoint protections, security administrators and home users can feel safe in the knowledge that their endpoints are provided with an extra layer of protection both inside and out of the network. So, whether an organization’s users are exposed to various types of attacks while working remotely or are targeted through phone lines via fax machines, the user’s endpoint itself is protected from known and unknown threats.
Conclusion
The ground breaking ‘Faxploit’ research into the vulnerabilities found in fax machine protocols, a technology that many would mistakenly consider to be risk-free, proves once again how organizations and consumers alike cannot overlook any part of their corporate or home network.
In fact, while our world becomes more connected through IoT devices, the cloud and mobile platforms, there still remain simpler technologies which can allow potential hackers to infiltrate IT networks and provide unauthorized access to sensitive information.
As a result, maintaining a frequent patching schedule and segmentation infrastructure, along with a high level of IT hygiene in general, is essential for protecting your data from potential attacks, from wherever they may come. By following best practices such as these, organizations can stay safe no matter what age of technology they choose to use.
Questions and Answers:
Q: What is this research about?
A: Check Point Research has uncovered critical vulnerabilities in the fax protocol. These vulnerabilities allow an attacker with mere access to a phone line, and a fax number to attack its victim’s all-in-one printer – allowing him full control over the all-in-one printer and possibly the entire network it is connected to.
Q: Does this apply only to all-in-one printers?
A: No. We conducted our research on all-in-one fax printers; however similar vulnerabilities are likely to be found in other fax implementations, such as fax-to-mail services, standalone fax machines, etc.
Q: Who uses fax anyway?
A: Surprisingly fax is still used by many industries, governments and individuals around the world. These include the healthcare industry, legal, banking and commercial – some of which are governed by regulations, and others simply for legacy reasons.
Q: What is the severity level of this vulnerability?
A: HP classified this vulnerability as ‘Critical’. Full details can be found here.
Q: How does this affect organizations and consumers?
A: Once an all-in-one printer has been compromised, anything is possible. It could be used to infiltrate an organization’s or consumer’s internal network, steal printed documents, mine Bitcoin, or practically anything.
Q: Does this apply to all fax machines?
A: Our research was done on HP Officejet all-in-one printers though this was merely a test-case. We strongly believe that similar vulnerabilities apply to other fax vendors too as this research concerns the fax communication protocols in general.
Q: Is it widespread?
A: By our estimates, there are currently hundreds of millions of fax machines still in use around the world. Financial reports from Wall Street indicate that tens of millions of all-in-one printers are sold worldwide each year.
Q: Has it been fixed?
A: We worked closely with HP to fix the vulnerability and, following the process of responsible disclosure, they managed to release a patch before this publication. In fact, if your device is already configured to auto-update then the patch has likely already been applied. This patch, however, only applies to HP all-in-one printers and the vulnerability may well still apply to devices from other manufacturers as well.
Q: What should I do to protect myself?
A: If you own an HP Officejet all-in-one printer then follow the instructions from HP here. In addition, you should implement segmentation policies, software patching and proper IT hygiene – please see our ‘Recommendations’ section in the above blog post. Also, if you are no longer actually using the fax functionality in your all-in-one printer then we recommend you to disconnect the PSTN line.
Q: Has it been seen it the wild?
A: Not yet. Our research was intended to highlight a potential security risk.
Q: Can you share more technical details.
A: Yes, please visit Check Point Research for full technical details.
Q: Why is Check Point doing this research?
A: As a cutting edge research team, we believe it is our professional responsibility to look into known and unknown risks and vulnerabilities in the cyber threat landscape. By carrying out this kind of research, along with the rest of the cyber security community, we hope to make the online world safer.