A massive survey of nearly 1,200 IT security practitioners and decision makers across 17 countries reveals that half the people who fell victim to ransomware infections last year were able to recover their files after paying the ransom demand.
The survey, carried out by research and marketing firm CyberEdge Group, reveals that paying the ransom demand, even if for desperate reasons, does not guarantee that victims will regain access to their files.
Timely backups are still the most efficient defense against possible ransomware infections, as it allows easy recovery.
Over a quarter of all victims lost their data for good
The survey reveals that 55% of all responders suffered a ransomware infection in 2017, compared to the previous year's study, when 61% experienced similar incidents.
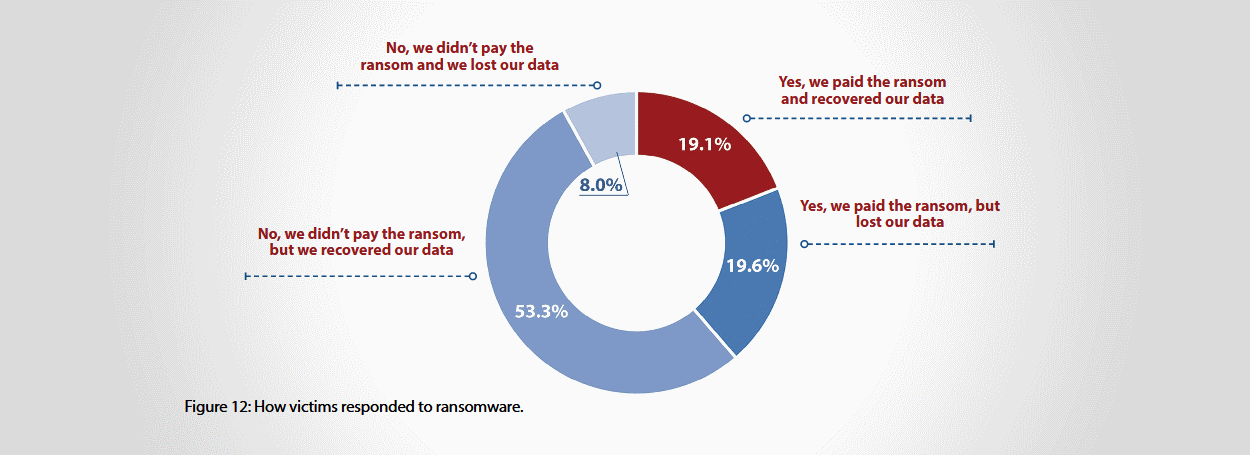
Of all the victims who suffered ransomware infections, CyberEdge discovered that 61.3% opted not to pay the ransom at all. Some lost files for good (8%), while the rest (53.3%) managed to recover files, either from backups or by using ransomware decrypter applications.
Of the 38.7% who opted to pay the ransom, a little less than half (19.1%) recovered their files using the tools provided by the ransomware authors.
The rest (19.6%) lost their data. Ransomware authors either didn't provide ransomware decryption instructions or apps, or these tools did not yield expected results.
Overall, the study found that over a quarter of ransomware victims (27.6%) lost their data for good, either by paying or not paying the ransom demand.
Other findings of the CyberEdge survey are below:
⩺ Security-related budgets are prognosticated to rise in 2018 with 4.7% compared to last year.
⩺ Security-related budgets are expected to account for 12% of the overall IT budget for companies in 2018.
⩺ Four in five organizations said they are experiencing a shortage of personnel with IT security skills.
⩺ Nine in ten companies are experiencing cloud-related security and privacy problems.
⩺ Survey respondents said they perceive mobile devices and app containers (Docker, Kubernetes, Cloud Foundry) as their organization's weakest link in terms of security.
⩺ Respondets said they plan to invest money in 2018 in advanced malware analysis/sandboxing (network security), containerization/micro-virtualization (endpoint and mobile security), and API gateway (application and data-centric security).


Comments
cdcjb - 6 years ago
--Heads up: the title on the browser window is "Facebook". It's happening on multiple articles and multiple browsers.--
Edit: fixed
Occasional - 6 years ago
Thanks CC - reports of this kind are important arguments against paying ransomware. The fewer people that pay, the less incentive to deploy RW - and that will make life a bit easier for everyone.