The world of cyber security has many technologies across the entire attack surface. There is a web of complexity to be managed. This becomes frighteningly obvious when trying to investigate threats, both historical and in real time. How do you translate event logs from a myriad of systems into a story of what happened and what is happening? How do you operate at a great scale and at the same time paint a simple picture? How do you allow the analyst to unpack and unpeel the story the logs are telling quickly and intuitively. This is amongst the greatest cyber-specific challenges facing the SOCs & CSIRTs.
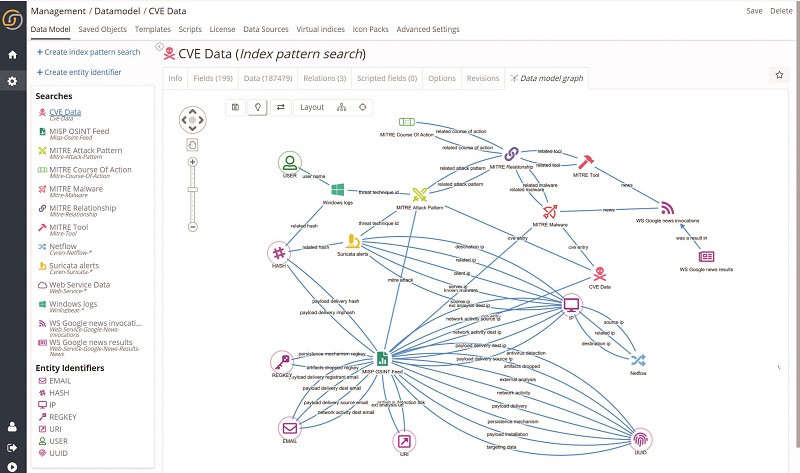
The Siren data model leverages the MITRE ATT&CK® framework to encode, define, categorize, and present the cyber attacks in a manner that is easy to understand.
When investigating cyber threats, it requires skilled analysts to fuse, understand, and analyze the available data. Siren enables security analysts to search all the data in a single pane of glass, moving from one index to another through intuitive graphs or relational navigators that makes exploring logs effortless – without complex query languages.
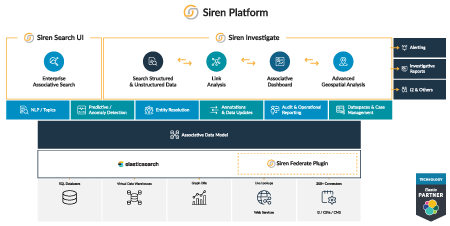
Siren is built on Elasticsearch, a system popular in the Cyber Security world for streaming, storing, and searching system logs. Siren holds a rich set of integrated capabilities that can seamlessly integrate into any organizations’ framework.
Some of the Siren’s key capabilities include:
Siren is used in SOC centers as an Investigative complement to existing SIEMS, SOAR, and particularly Elasticsearch deployments. Real time investigations and situational awareness is essential in both National Security & Large Corporates. Siren can help make sense of these massive amounts of information. Typical cyber use cases include:
Our experts can show you exactly how to leverage your data to uncover powerful insights! Learn how Siren's investigative intelligence capabilities effectively address the threats in the cybersecurity world.
Read more on Siren for Cyber Security
Ready to kick-start-your project?
Siren for Cyber Threat Intelligence: Keep Your Networks Safe