GDPR has changed how we run referral programs forever.
And only for the better.
The need for explicit consent, for example, pushed companies to become more mindful of their audience.
The control over their data put customers in control. And, as I pointed out in an earlier article, it might make them more open to engaging with companies again.
But GDPR poses some challenges too.
One of them is the issue with collecting information to send referral emails.
Today, to run a referral program, you must be able to prove that your organization truly needs whatever information you collect during the process.
And that’s actually not so simple.
For one, most email referral programs would need access to more data than they need, even if only for a short moment.
For example, to send referral emails, you need to access a person’s entire address book. It’s the only way to allow them to select recipients of the referral email.
At the same time, GDPR clearly states that a data processor, in this case a company running the referral program, should only use as much data as it is required for the given task.
So, in this post I decided to shed some light on the data minimization principle, discuss its implications for referral programs, and then suggest some potential solutions.
What is the Data Minimization Principle?
The data minimization principle says that organizations must only process personal information that they actually need to achieve the objective of processing the data.
For example, rec.39; Art.5(1)(c) says:
“Personal data must be adequate, relevant and limited to what is necessary in relation to the purposes for which those data are processed.”
In other articles, GDPR defines the requirement for the data as:
- Adequate,
- Relevant,
- Limited to only the necessary information required for the purpose it is processed.
In other words, the data minimization principle forces you to be more conscious about what data you collect.
Again, not a bad thing. But it does have certain implications for your growth strategies.
Take a lead generation form, for example. Typically, companies have used lead capture forms to ask visitors for anything from just the basic information like name and email, to details that would help them prequalify a person.
Hubspot, for example, asks for email and job title. And they clearly do it to qualify new leads better.
(Although, worth to note that pre-GDPR their lead capture forms were much longer, asking for more detailed information about a person.)
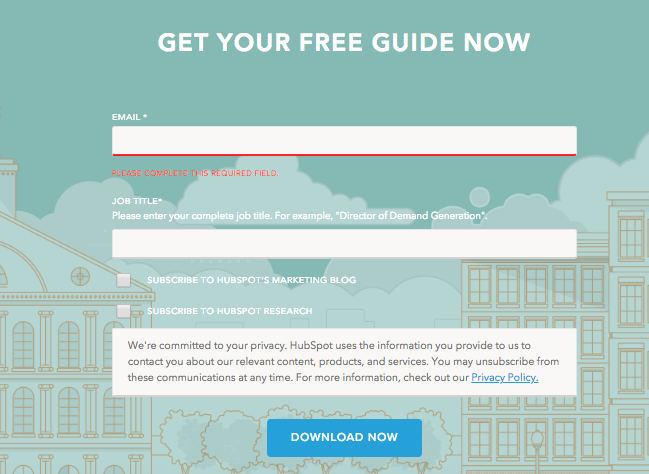
Under the data minimization principle, however, they have to justify every field on the form. What’s more, they must be able to prove how necessary it is to carry out the objective for collecting the data.
In this article, Dataguise, a company providing GDPR compliance, outlines three other scenarios where the principle impacts how organizations store and process the data.
- Development or testing environments in which data helps assess and test new functionality or other elements, and because of that, has to behave in the exact same way as in a live product.
- The production environment, where real data might have to be collected, and thus, forces companies to re-evaluate the information they collect.
- Data warehousing and analytics, forcing companies to assess whether they still require the information they hold in various databases.
And as I hinted in this post’s introduction, it also relates directly to referral and viral programs.
Here’s how.
Data Minimization Principle in Referral Programs
A typical referral or friend-invite program depends on two factors:
- An engaged user who decides to share a product with their network, and
- Easy access to all their contacts to send referral emails.
In other words, a person who decides to recommend your product to others must be able to access their friends’ contact information to send a referral.
In practical terms, this means importing their address book to select whom to notify about a product.
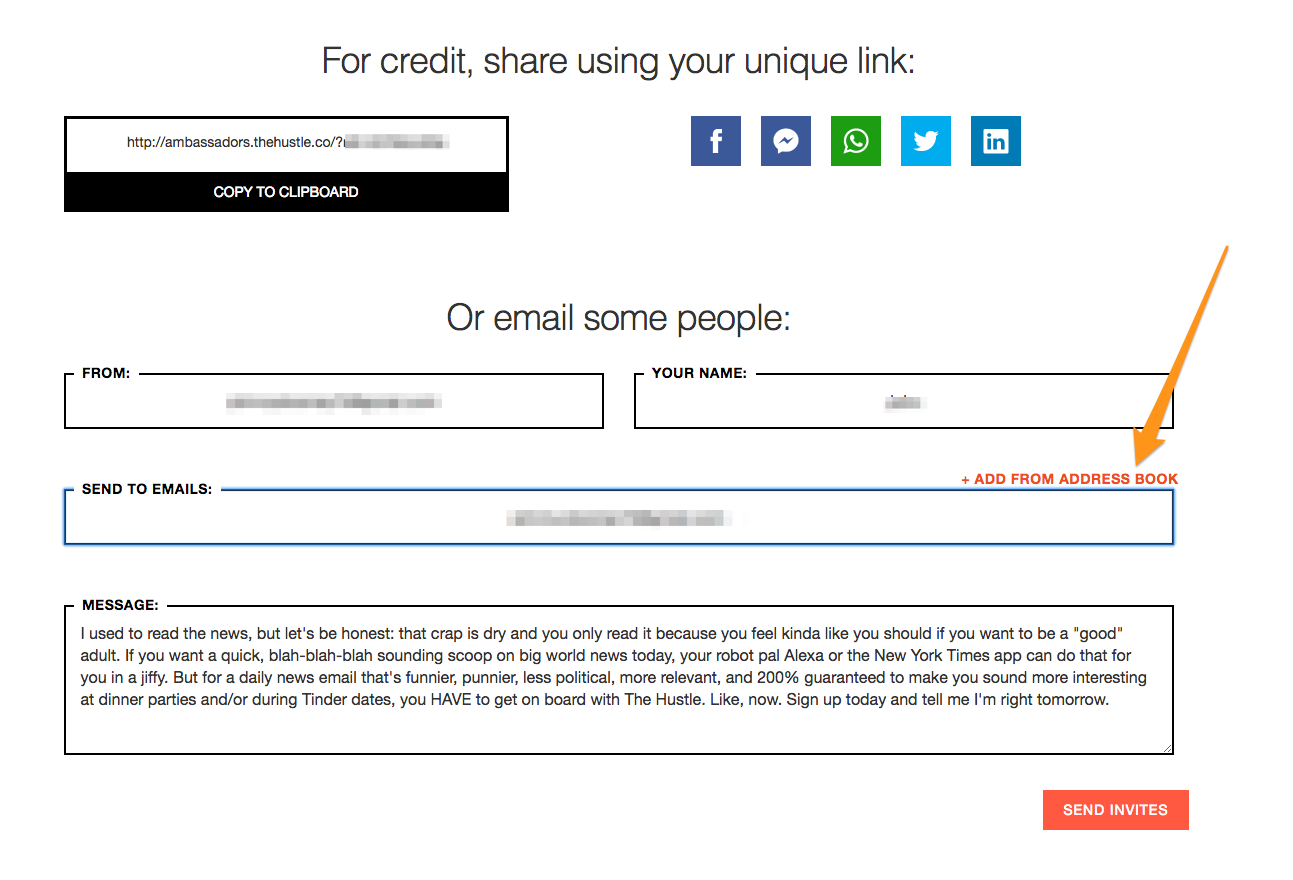
Unfortunately, processing such a request might violate the data minimization principle.
By accessing a person’s entire address book, an organization – who in this circumstance would become a data processor – might be gaining access to more than accurate, relevant and necessary data from a person – the data controller.
Think about it. To facilitate sending a referral, a company needs only a recipient’s email, not a person’s entire address book.
Now, I believe it is acceptable for processors to access a person’s address book to select specific recipients. However, in doing so, they might have to implement various technical and organizational measures that processing will meet the requirements of GDPR and ensure protection of data subjects rights.
Some of these include:
- Specific or general consent of the controller to engage a subprocessor.
- A processor shall inform the controller of any processing requirement unless legally prohibited from doing so.
- Processors need to ensure anyone processing the data is under a confidentiality restriction.
- The processor has to assist the controller in responding to requests made by data subjects.
- Processors are the processor is supposed to inform the controller if instructions the controller gives to the processor violate GDPR.
- As far as security, the processor should take measures to:
- Use pseudo-anonymisation and/or encryption when accessing the controller’s data. This specifically includes:
- Ensuring the ongoing confidentiality, integrity, availability and resilience of processing systems and services.
- Restoring the availability and access to personal data in a timely manner in the event of a physical or technical incident.
- Regularly testing, assessing and evaluating the effectiveness of technical and organizational measures for ensuring the security of the processing.
- Use pseudo-anonymisation and/or encryption when accessing the controller’s data. This specifically includes:
And needless to say, the legal implications of failing to meet these criteria are costly: the greater of 4% of global revenue or $20M.
How to minimize this risk
The challenge above is you gaining access to a person’s entire address book to collect the necessary information. In this case, you’re becoming a data processor.
But what if you weren’t?
What if another company took the processor’s responsibility, forwarding you only the data you need?
That’s precisely how CloudSponge can help you minimize the risk.
CloudSponge’s Contact Picker allows you to allow users select referral email recipients from their address book without your involvement.
In this instance, the only data you’ll receive will be email addresses of people, to whom a user wants to send referral emails.
Try out the CloudSponge Contact Picker here.
Review and Audit Your Sharing Process
Download our Better Sharing Workbook Now
(it's quick, easy and absolutely free!)