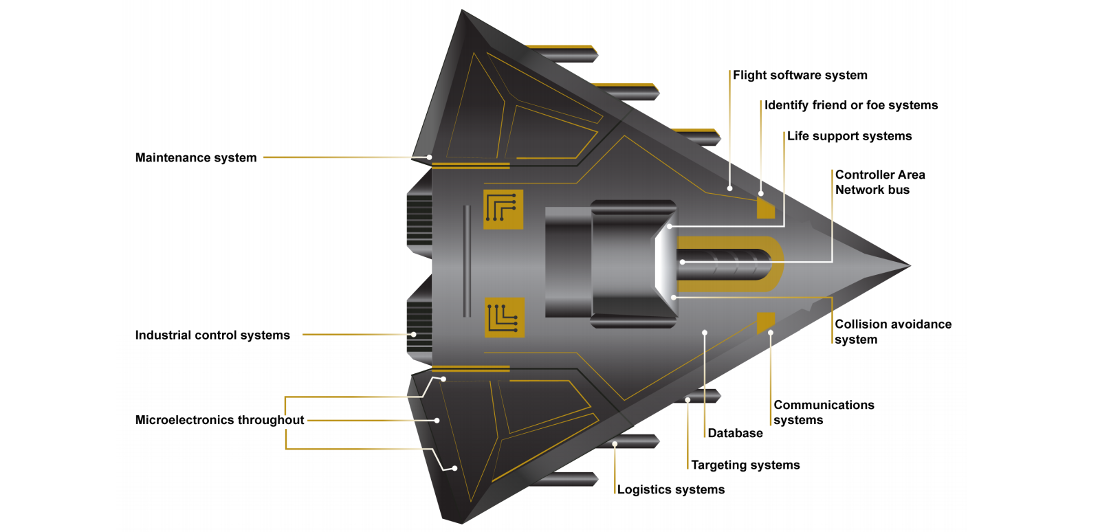
Major weapon systems developed by the US Department of Defense are riddled with vulnerabilities that make them an easy target for adversaries trying to control them or disrupt their functions.
As the DoD plans to spend about $1.66 trillion to advance its weapons arsenal, the US Government of Accountability Office (GAO) finds reports from various development stages of the systems showing that mission-critical vulnerabilities are a regular find in "nearly all weapon systems that were under development."
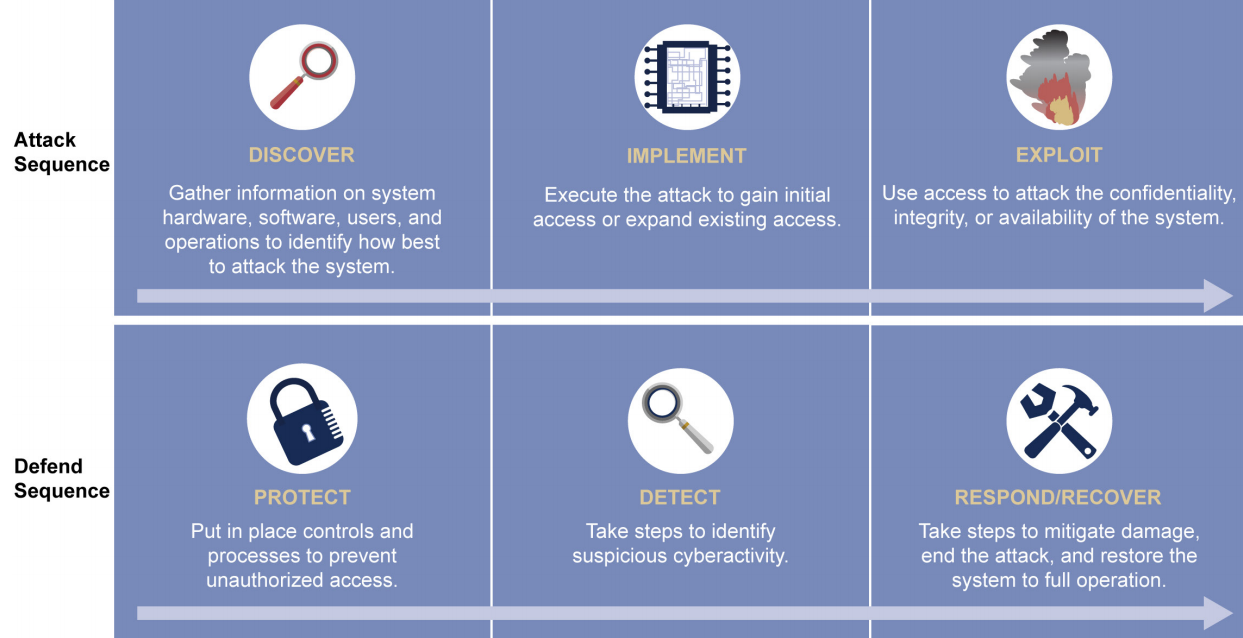
Testing teams charged with probing the resilience to cyber attacks were able to take control or disable the target using basic tools and techniques. Sometimes, just scanning the system caused parts of it to shut down.
GAO says that it found test records about credentials management being so poor that one team was able to guess the admin password of a system in nine seconds. The most likely reason for this was that the administrators did not change the default passwords in the software installed on the weapon system.
Hiding malicious operations and bypassing protection controls was possible by using information or tools available for free to anyone with an internet connection, GAO informs in a report published today.
The trouble runs deeper
Multiple factors allowed the intrusion of the red team to remain undetected, sometimes for several weeks. GAO officials learned about cases where the trespassers were deliberately loud in their actions, yet the operators of the system failed to see the signs of the suspicious activity.
Misconfiguration of alert systems is part of the problem as multiple reports indicated that the intrusion detection systems (IDS) raised the flag correctly, but the operators did not receive the alert. In another, the IDS showed a permanent alert status, making it undependable to the user.
"One test team emulated a denial of service attack by rebooting the system, ensuring the system could not carry out its mission for a short period of time. 41 Operators reported that they did not suspect a cyber attack because unexplained crashes were normal for the system," says the report from GAO.
System operators are also to blame
Some of the attacks went completely unnoticed despite evidence in the activity logs because the operators did not bother to check them.
Reports of tests revealed cases when intrusions were detected but the operator failed to deploy an effective counteraction. In one instance, the defense measures were easily bypassed by the test team. In another, outside assistance was necessary to restore the computer.
The red team having fun
Finding a way to gain access to the target and control it, fully or partially, was the main objective, but the teams assessing the vulnerable state of the weapon systems also had their fun.
Internal reports show that when they got a foothold on the system, the testers were able to escalate privileges and move around easily, even watch in real time every move of the operators of the target systems.
Copying, deleting or modifying data was just as regular an occurrence as the discovery of major vulnerabilities. One team even managed to steal 100GB of data.
Among the pranks they pulled on the defenders, the "attackers" displayed a pop-up message on the user's terminal, "instructing them to insert two quarters to continue operating," the GAO report notes.
Root cause analysis
GAO's audit lasted for over a year, from July 2017 until October 2018, and involved examining cybersecurity reports on selected weapons tested between 2012 and 2017.
The congressional watchdog also looked into the steps the DoD is taking to improve the security stance in the weapon systems, by analyzing acquisition, requirements, testing policies and guidance revised since 2014.
The conclusion is dire, though: the DoD is late to the game and missed important steps for the development of weapons capable to withstand cyber attacks.
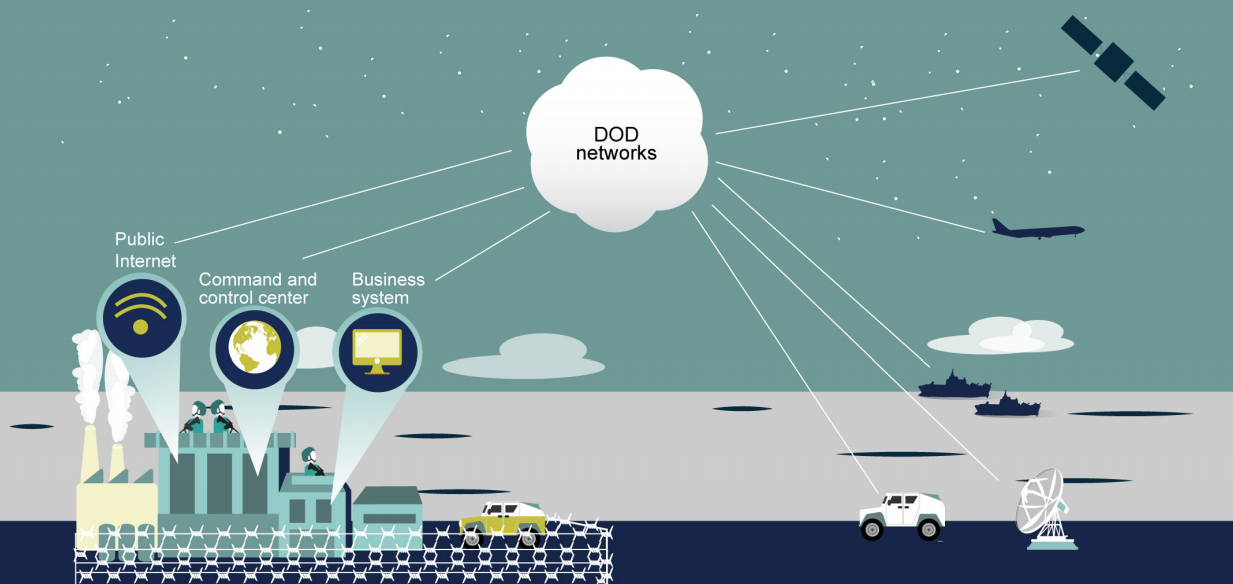
The cyber defenses focused mostly on the infrastructure and the networks, not on the weapons themselves, which also evolved into computerized systems that require at least the same level of attention.
"Multiple factors contribute to the current state of DOD weapon systems cybersecurity, including: the increasingly computerized and networked nature of DOD weapons, DOD’s past failure to prioritize weapon systems cybersecurity, and DOD’s nascent understanding of how best to develop more cyber secure weapon systems," GAO officials conclude.
Despite loud warnings about cybersecurity risks, the DoD took its time making this aspect a priority. The result is a basic understanding of today's issues and how they can be exploited by a real adversary.
According to GAO, some program offices still struggle to recognize the cybersecurity implications as far as system design and connectivity are concerned.
Probably discounting the modern attack scenarios, there are officials that dismissed some of the test results as being unrealistic; they also showed a strong belief that the weapon systems were properly protected.
The current state discovered by GAO may be just the tip of the iceberg, as this is the agency's first audit of weapon systems acquisitions and it did not analyze the problems in a larger context that includes security of contractor facilities, Internet-of-Things devices or industrial control systems.


.jpg)
Comments
Maelish - 5 years ago
Funny how Hedy Lamarr was concerned about the nazis hacking radio controlled torpedos in WWII but no one seems concerned about these things in our era. It's pretty sad.
the_moss_666 - 5 years ago
It's just as it is with most IoT devices. Features first, security second.