Passwords. We all have lots of them these days. And yet we're told repeatedly to not reuse passwords and to make them strong. For most of us, that's an opposing set of directives. Unless you have some amazing memory, there's no way that we mere mortals will ever be able to remember a different and complex password for every account. This difficult situation causes us to make serious password security mistakes, but we'll share best practices to make using passwords both easier and more secure.
The Problem with Reusing Passwords
We tend to fall into the trap of reusing passwords because it's nearly impossible to remember a different password for every site we visit, especially when there's no one standard for password complexity. One site might want you to use at least 14 characters, including a capital letter, a symbol, and a number. Another might not let you use more than eight characters and no symbols allowed to boot. Proof this is frustrating? An OpenVPN survey found that 1 in 4 people use the same password for every enterprise system they regularly use, despite a majority of employees saying personal data compromise is their top security concern.
So let's talk about data breaches. They sometimes hit the news — you might remember that in 2016 LinkedIn was compromised to the tune of 164 million user accounts. In this case, LinkedIn was storing passwords insecurely–not only did the hackers retrieve a lot of information about the users, they were able to retrieve the actual passwords as well. Data breaches happen somewhere every day, to organizations large and small. In many cases, a data breach means passwords get exposed.
What that means, beyond the immediate effect that someone has access to your account on site X, is that all of those passwords end up in lists that people can download or buy. Hackers will then go around looking to see what other sites those passwords will work on. So, even if site Y protects your password properly, if it can be breached via site X, then you are at risk of compromise on site Y anyway. That's one very good reason to not reuse passwords.
Protip: There's a great tool, Have I Been Pwned, that will notify you if your account has been compromised on any known security breaches. You can also check if a password—your password—is a known breached password at https://haveibeenpwned.com/Passwords.
Trying to Invent a Clever Algorithm for All Your Passwords Doesn't Work
Instead of reusing passwords, we might try coming up with some method or "algorithm" to generate a password for a site. But using a method to generate a password just means that when one of your passwords is compromised, it usually doesn't take a lot of effort to figure out what that method might be.
For example, password is always in the top 25 popular passwords (and yet people still use it!) And sure, we can get clever and replace 'o' with '0', or 'a' with '@'. Let's see, though. Running password and a few of its variants through that password checker will tell us how many times that particular password has been seen in data breaches.
password - 3,645,804
p@ssw0rd - 50,431
p@ssw0rd! - 563
Compared with m^N@tTa8gm969=Zr which has been seen zero times, well, that's a pretty good case to use strong, unique passwords.
Most of the clever algorithms we use for creating passwords are actually very common and predictable: We tend to use a place, name, or common word as the base; capitalize the first letter; add a number (usually 1 or 2) at the end; and add one of the most common symbols (~, !, @, #, $, %, &, ?.
Fido1! anyone?
The Solution: Use a Password Manager
What to do, then, if you care about the security of your passwords? You should be using a password manager. It's like a little black book of passwords—but encrypted, which means that even if someone gains access to your black book (or file) of passwords, they wouldn't be able to read it without the master password.
At their most basic, all password managers work in more or less the same way:
Create an encrypted file (or vault) that all of your passwords get stored in
Have the means to allow you to verify that you are allowed to access the vault (e.g. password, cryptographic key, fingerprint, etc.)
Let you copy the password for a given account so that you can paste it into the password box when logging in somewhere. You never need to actually know or type the password.
There are two main options here: password managers with cloud storage and password managers with a local file.
A password manager with cloud storage means that your vault is stored "in the cloud," which is a fancy buzzword that really just means 'on someone else's computer'. That sounds scary, but as long as your vault is properly encrypted it's not a problem. This also has the big benefit of letting you have the password manager application on all of your devices, all using the same vault. When you add or change a password on one device, it automatically is reflected everywhere else.
A password manager with a local file means that the vault is totally under your control and it's up to you to store it somewhere. This means that if you want to share the vault between all your devices, you still need to put it in some accessible location like Dropbox, OneDrive, or whatever your choice is. That is, of course, 'in the cloud'—but it's your choice of where that is and it means that a hacker would need an additional step to get to your passwords; they'd need to get into your cloud storage account (login information and perhaps two-factor authentication) and also know the login for your password manager.
An example of a password manager with local storage is KeePass. Two of the more popular cloud-based password managers are 1Password and LastPass. Checkout our 1Password vs. LastPass showdown to compare the two.
The biggest benefit to using a password manager is that you can now generate passwords as complex as you want—without having to remember it. And you should. Make them as long as a given site will let you use. Ideally, that's at least 16 characters but some places have funny password rules that you'll have to obey. If you can get away with 64 characters, do it!
What should a password look like? Some sites have odd password requirements. Fortunately, every password manager lets you change the way passwords are generated, so for any site it only takes a little fiddling to find a good, random password that the site will accept. In general, you should start out with letters, numbers, and symbols and remove some only if the site can't handle them
The Only Two Passwords You Need and How to Create Them
When it comes down it, you should only have two passwords that you need to remember:
The one to let you log into your device
The one to let you access your password manager
To create this memorable password that is still secure, create a passphrase.
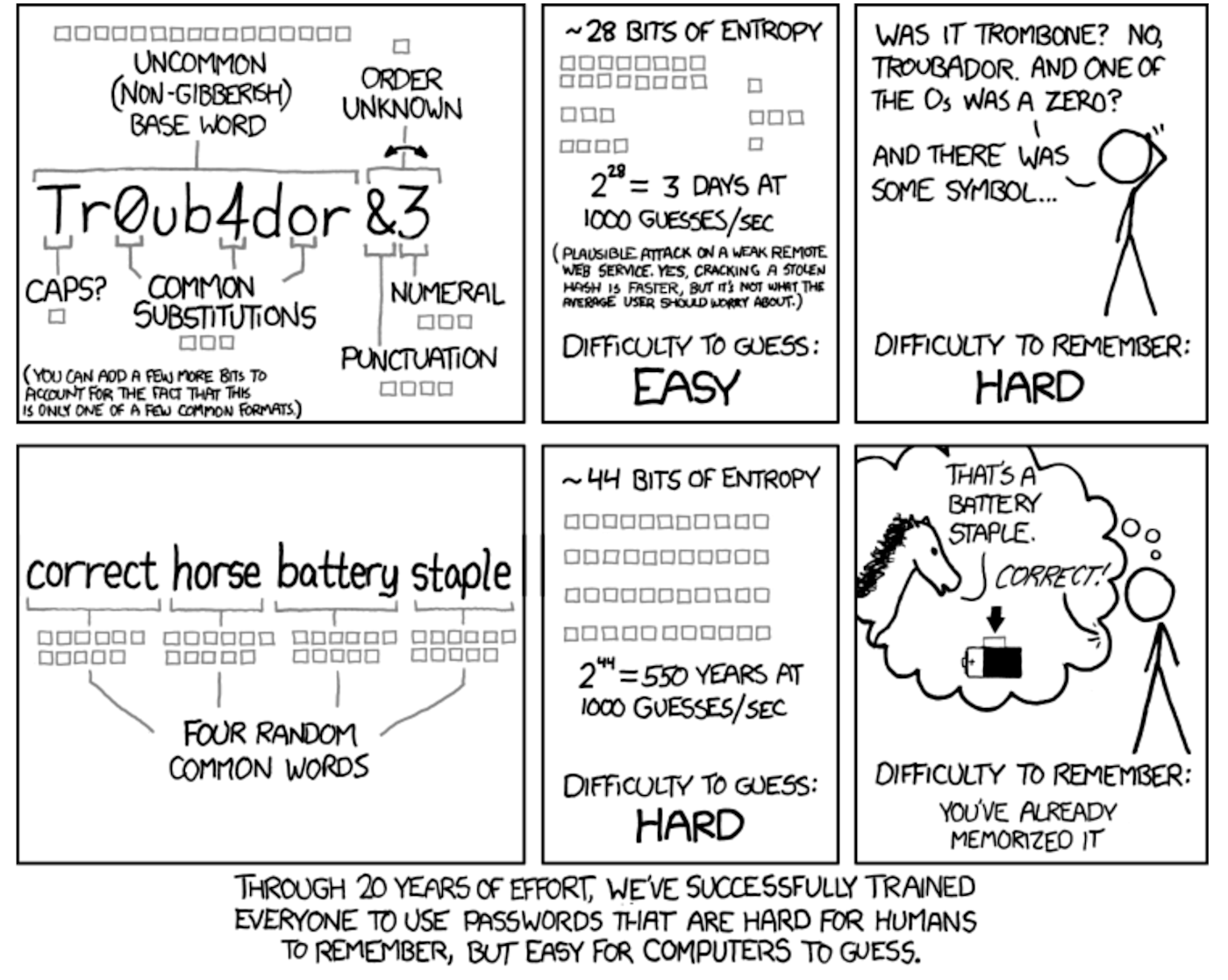
While it's proven that passphrases aren't as effective as a good random password, they're better than a difficult-to-remember password for either logging into your devices or your password manager. Passphrases are also good for those sites that for whatever reason don't let you paste into the password field or a device that you can't or shouldn't get your password manager installed on (for example, a server that you often use for work). Using a passphrase for these cases, you can look at your phone displaying the words and more easily type skill northern polaroid norton than a password with lots of @#*^!$; characters.
It's still a good idea to not use common "easy" words, so generating them with something like Use a Passphrase is a good idea. If you can get away with it. use more than four words, which makes it harder to guess and therefore is more secure. And, of course, don't reuse passphrases!
What to Do About Account Security Questions
One final thing to talk about is security questions. You know, where a service asks you for several questions to answer in case you lose your password, or even just to log in every time. These are the bane of your bank account login and logging into most other "official" institutions. And they are ridiculous.
They're either so simple that anyone who can type google.com can figure them out, or you enter an answer that is not easily guessed... and then you're sitting there wondering if you put "Public School #6", "PS #6", or "P.S. #6", and now you're locked out anyway.
The solution? You should totally make up fictional or nonsense answers to them. That's right. Don't give anyone a chance to research or guess. Passphrases work nicely for these. You'll definitely need to record those answers somewhere. Best bet is to keep them in a text document or a spreadsheet that isn’t connected online anywhere. You could also keep them in your password manager, but if by some chance someone does extract data from the encrypted vault, while they might not get the actual password, a security question answer can be just as good for getting into your account. It’s better to keep those separate if possible.
But wait, what about two-factor authentication? That's an excellent question. You should also definitely turn that on because it's the extra layer of security beyond just password management that can protect your digital life.
Did you get pwned? Here's how to change all your passwords at once.