The death of network neutrality and the loosening of regulations on how Internet providers handle customers' network traffic have raised many concerns over privacy. Internet providers (and others watching traffic as it passes over the Internet) have long had a tool that allows them to monitor individuals' Internet habits with ease: their Domain Name System (DNS) servers. And if they haven't been cashing in on that data already (or using it to change how you see the Internet), they likely soon will.
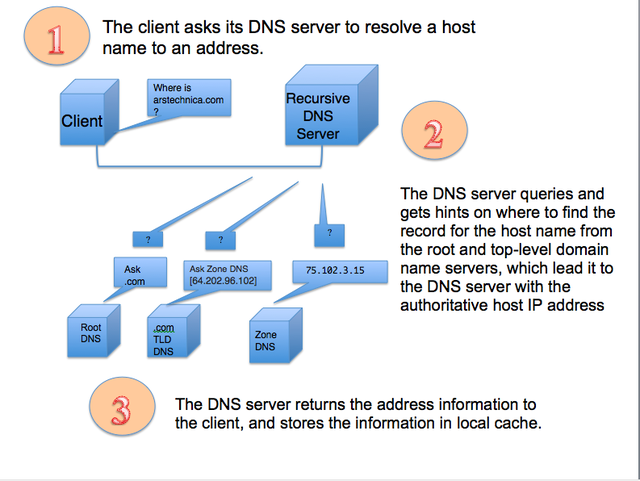
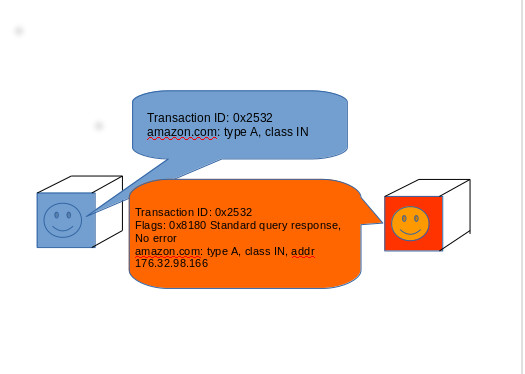
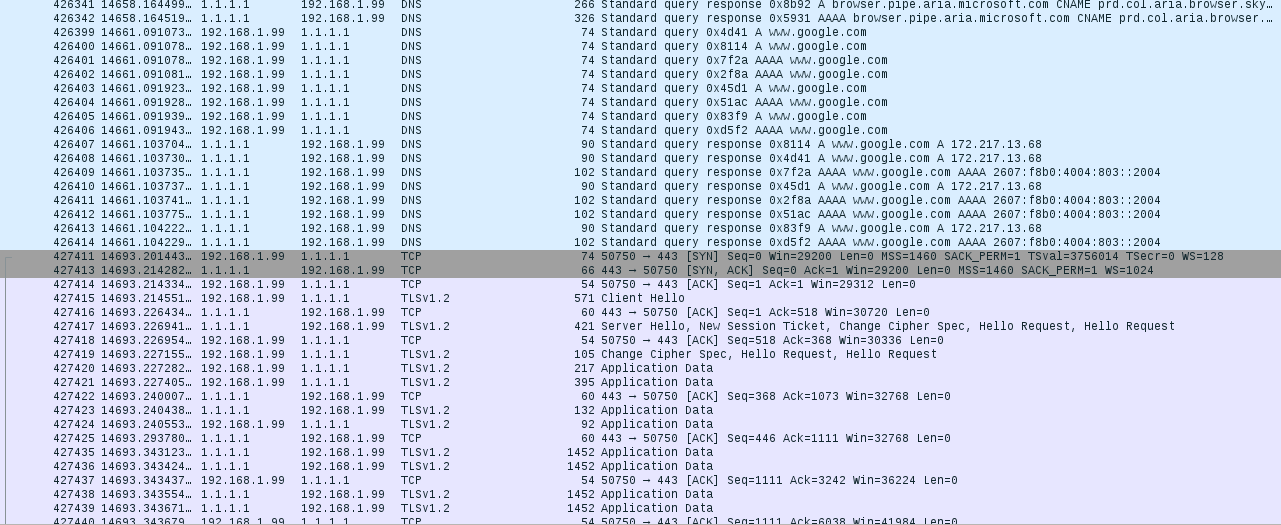
DNS services are the phone books of the Internet, providing the actual Internet Protocol (IP) network address associated with websites' and other Internet services' host and domain names. They turn arstechnica.com into 50.31.169.131, for example. Your Internet provider offers up DNS as part of your service, but your provider could also log your DNS traffic—in essence, recording your entire browsing history.
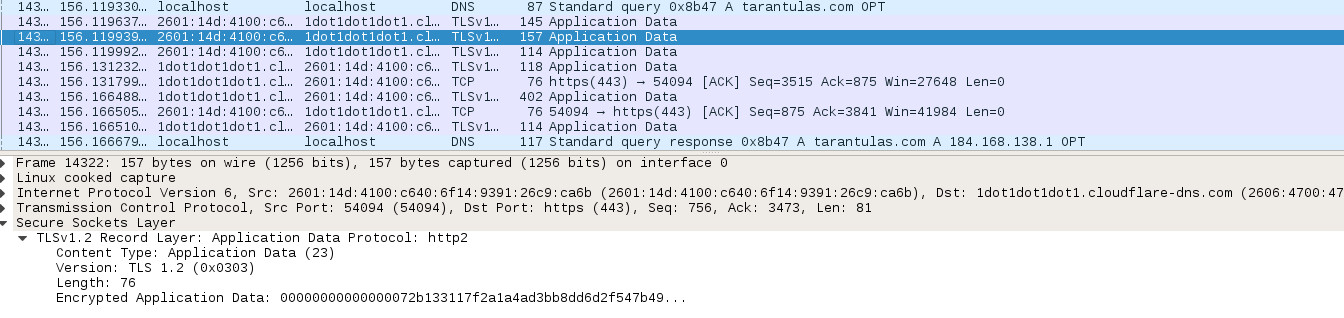
"Open" DNS services provide a way of bypassing ISPs' services for reasons of privacy and security—and in some places, evading content filtering, surveillance, and censorship. And on April 1 (not a joke), Cloudflare launched its own new, free high-performance authoritative DNS service designed to enhance users' privacy on the Internet. This new offering also promised a way to hide DNS traffic completely from view—encryption.
Named for its Internet Protocol address, 1.1.1.1 is the result of a partnership with the research group of APNIC, the Asia-Pacific Internet registry. While it's also available as an "open" conventional DNS resolver (and a very fast one at that), Cloudflare is supporting two encrypted DNS protocols.
While executed with some unique Cloudflare flare, 1.1.1.1 isn't the first encrypted DNS service by any means—Quad9, Cisco's OpenDNS, Google's 8.8.8.8 service, and a host of smaller providers support various schemes to encrypt DNS requests entirely. But encryption doesn't necessarily mean that your traffic is invisible; some encrypted DNS services log your requests for various purposes.












 Loading comments...
Loading comments...