
A little over a week ago, researcher promised to run a 51% attack on the blockchain of a small cryptocurrency called Einsteinium (EMC2), to show the world how easy the entire process was.
He kept his promise he made in a message on Reddit and over the weekend he managed to get control of about 70% of the network of a different cryptocurrency, Bitcoin Private (BTC). And he live-streamed it.
In the cryptocurrency world, the more control an entity has over the network's mining power (hashrate), the better their chances to influence transactions, like reversing the process of completing them (double spending) or preventing confirmations.
Using the handle GeoCold, inspired by the alias of hacker George Hotz, the researcher set things up to stream the demonstration on Twitch, but he got banned. He then tried StreamMe and got banned on that service, too.
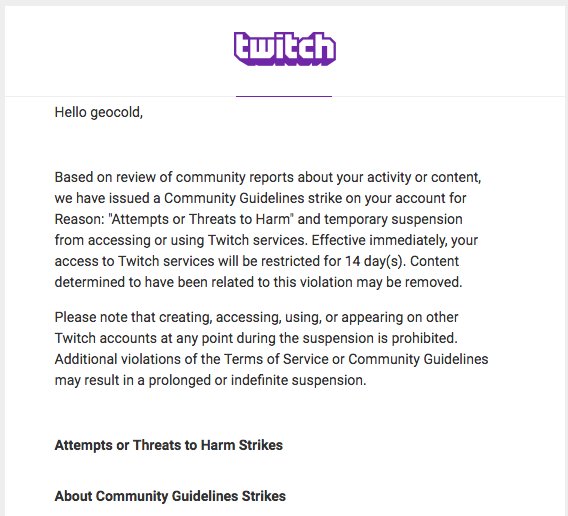
Update on the stream. Got banned from two streaming platforms fairly quickly. I'm going to try to find a platform where I can be assured report spamming won't work. If not I'll just post a video on youtube. But attack wise: We got ~70% of BTCP's network and I was about to fork it
— GeoCold "Mischief-Maker" (@geocold51) October 13, 2018
Nevertheless, GeoCold managed to prove his point: that cryptocurrencies with a small market cap are easy to attack. He is not a beginner at this. He told BleepingComputer that he did this type of attacks many years ago.
He shared with us the details of the demo from an attacker's point of view, which takes nine steps to complete:
- Get two servers with the same wallet running on it.
- On one server setup a mining pool, we’ll call this the offline server.
- Disconnect that server’s wallet from all its peers on the network.
- Send a transaction from address A (which is on both wallets/servers) to address B which is just an arbitrary address we also own.
- Then, start mining with a greater hashrate than 50% the hashrate of the coin so that we can consistently (in aggregate at least) get a longer blockchain than the normal network.
- Next, on the online server/wallet, we send the money we just sent on the offline server to an exchange. We wait for it to deposit to go through and then exchange it for another coin like Bitcoin and withdraw that.
- By this point, we’ll have a longer blockchain on our offline server that contains a transaction that conflicts with the one we just sent to the exchange.
- We take the offline server online and then the world is told about our new, longer blockchain and they all use it because it’s longer. They go through and merge their chain with mine and in doing they see that there’s a conflicting transaction (the on to the exchange and the one from wallet A to wallet B). They pick the one from A to B because it’s part of the longer chain.
- Boom, you’re done, you’ve doubled your money via crypto magic.
GeoCold got to step six in front of the audience and did step seven offline. He said that he could have completed the demonstration, but he did not want to do it without viewers.
The cost for a 51% attack on small cryptocurrencies is far from being restrictive. A website that exposes this reality shows a collection of coins and the theoretical cost of such an attack on each network.
"I thought the world should know how easy they are to pull off because any time you talk about a 51% attack people will say it’s not possible for XYZ reason and I wanted to show that they are and that devs should fix their coin," GeoCold told us.
The truth is that 51% attacks are quite common, especially when cloud mining services like NiceHash are used. In fact, NiceHash is the resource hackers use to pull 51% attacks.
We asked him if there was something that could have prevented his demo attack. The answer was a straight "Yes." By implementing checkpointing or hybrid Proof of Stake, which allows someone to mine or validate transactions by the number of coins they have, GeoCold said.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now