
Thinking about making a ransomware payment? If so, you may want to think twice before doing so as it could land you in trouble for violating U.S. government sanctions.
This week the Department of Justice unsealed a grand jury indictment against two Iranian hackers allegedly responsible for the SamSam Ransomware. As part of this indictment, for the first time the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) also publicly attributed cryptocurrency addresses to individuals who were involved in the converting ransomware cryptocurrency payments to fiat currency.
"While OFAC routinely provides identifiers for designated persons, today’s action marks the first time OFAC is publicly attributing digital currency addresses to designated individuals" stated the Department of Treasury's announcement.
In this particular case, the cryptocurrency addresses are being attributed to Iran-based individuals named Ali Khorashadizadeh and Mohammad Ghorbaniyan who the U.S. government states have facilitated the exchange of ransomware payments into Iranian Rial. The addresses attributed to these individuals are 1AjZPMsnmpdK2Rv9KQNfMurTXinscVro9V and 149w62rY42aZBox8fGcmqNsXUzSStKeq8C and contain a combined total of 5,901 bitcoins. At the current prices of bitcoins this is equivalent to over $23 million USD.
OFAC has also added Khorashadizadeh and Ghorbaniyan to the Specially Designated Nationals And Blocked Persons List (SDN), which means that U.S. individuals and companies are blocked from doing business or conducting any transactions with these individuals. These sanctions could also affect non U.S. businesses and individuals who conduct transactions with them due to secondary sanctions.
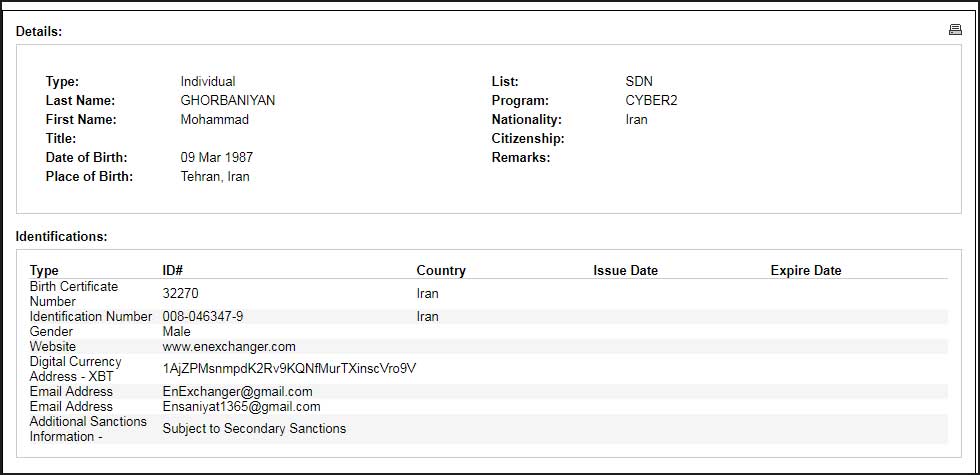
"As a result of today’s action, persons that engage in transactions with Khorashadizadeh and Ghorbaniyan could be subject to secondary sanctions," continued the announcement. "Regardless of whether a transaction is denominated in a digital currency or traditional fiat currency, OFAC compliance obligations are the same."
With these addresses now being attributed to known sanctioned individuals, those who are infected with ransomware and wish to pay the ransom must be extra careful not to send money to these bitcoin addresses. Doing so could impose fines that are far greater than a ransom payment itself.
The impact on ransomware recovery companies
This news is also going to have a wide impact on both ransomware negotiators and data recovery companies as they commonly interact with ransomware developers.
Coveware, a company that manages ransomware incidents for companies and negotiates on their behalf, now has to be extremely careful who they are sending ransomware payments in order to avoid fines or other legal ramifications.
"OFAC has made it clear that any U.S. business that sends cryptocurrency to wallet address, regardless of the reason, needs to check the OFAC list first.," Coveware CEO Bill Siegel told BleepingComputer via email. "Paying for ransomware with cryptocurrency had previously been tacitly acknowledged as a necessity, despite the legal and regulatory opacity of the activity. Treasury has officially taken the first steps towards setting a regulatory minimum standard of care for ransomware payments, and its a big step up."
With the rise of ransomware, we have also seen a rise in data recovery companies who claim that they are able to recover ransomware victim's files for a fee. It has long been suspected that these companies are not actually using any home grown techniques to recover victim's files, but are negotiating with the ransomware developers and simply paying the ransom on your behalf while tacking on a fee for their work.
While sources tell BleepingComputer that data recovery companies are already under scrutiny from law enforcement and are known to have been questioned in the past, they will also have to be extra careful with how they conduct their business.


Comments
Amigo-A - 5 years ago
Instead of sitting and inventing stupid sanctions, it would be better to allocate from the budget of a 33 penny to search for real extortionists.
This article mentions two people behind the extortion, but how real are these characters? Judging by the names, he is not a representative of Iranian nationality. One Azerbaijani, from Iranian Azerbaijan, another Armenian with a Muslim name. It seems that they are as real as Petrov and Boshirov. It is rather a myth, terrible for hysterical ladies only. :)