Password safety has been drilled into our heads for so long that it’s hard to imagine anyone isn’t aware of the importance of a strong password.
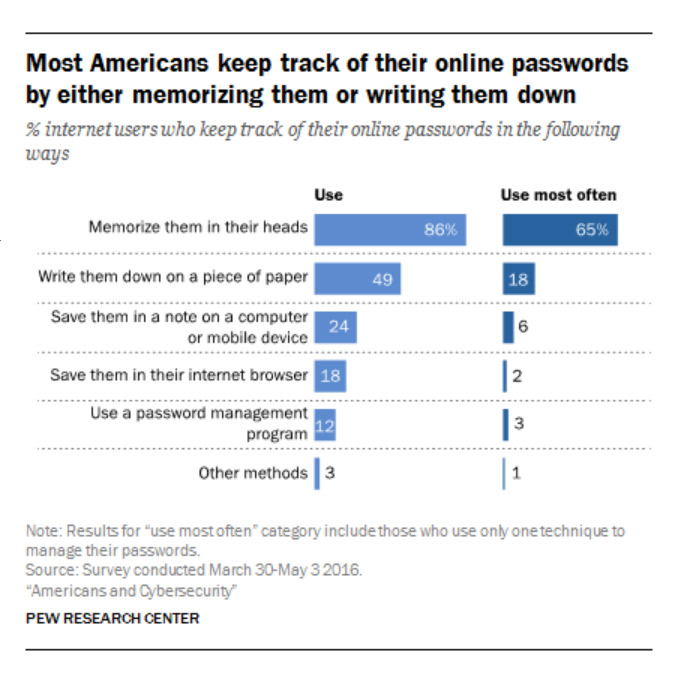
But, in fact, Americans’ password hygiene is surprisingly poor. When it comes to personal passwords, only 3% of people use a password manager to keep track of their never-ending list of passwords, according to the Pew Research Center.
But while poor password control on a personal level only affects the individual, improper management and sharing of corporate passwords can have some pretty devastating effects on an organization.
And anecdotal evidence from IT professionals suggests that people don’t suddenly become more security-focused as soon as they arrive at the office – the same password habits they keep in their personal life likely extend into their work life.
If you’re involved with enforcing password security at your company, one of the most important actions you can take is to identify and eliminate risky password sharing. Here’s where to start.
Sources of Insecure Password Sharing
Insecure password sharing happens frequently through the channels your employees already use for their daily communication: think emails, social media, text messages, Slack, handwritten messages, and the like.
Emailed passwords
How It Happens: Employees may send and receive passwords through emails for many reasons, such as needing help from a colleague on a project.
This may happen because your employees have received little to no cybersecurity training. For example, Information Age reported that less than 20% of employees who telecommute are aware of their company’s security policies – so this behavior is common.
The Risk It Poses: The risk is significant because hackers can take advantage of sent messages. If someone hacks into an employee’s email account, they can access sent messages and retrieve any passwords that have been sent out.
You can eliminate this risk of undue exposure by managing password sharing with a secure password manager.
Social media chat tools
How It Happens: Just like sharing passwords through email, your employees also might share their passwords in a social media chat. In fact, 25% of employees in the U.S. and U.K. said they shared a password because a colleague asked them for it.
The Risk It Poses: Sharing passwords over social media chats exposes your employees and firm to several security threats:
- Hackers – Hackers could gain access to the social media account and then access the password your employees shared in the chat.
- Colleagues and friends – The employee’s colleagues or friends may access their device and purposefully take the password.
- Corporate espionage – This is rare, but it’s still a possibility. If the social media platform sees your firm as a competitor, they may decide to use this password sharing event against you.
- Accidental exposure – An employee may lose their device or dispose of it without removing sensitive information.
- Government spying – Social media companies that share data with the government may be giving the authorities unauthorized access to your company’s internal workings.
In a nutshell, don’t leave your organization’s password sharing to chance. It can spell the end of your business or cause severe damage.
Text messages containing passwords
How It Happens: Text messages are encrypted while in transit between sender and receiver. But service providers are obligated to store your data and grant access to the government for surveillance purposes as necessary.
The Risk It Poses: Even if employees don’t have to worry about surveillance (and that’s still a possibility, however remote), that data is still potentially vulnerable. So it’s good practice not to send any sensitive data via SMS if you don’t want a third party to potentially access it.
Slack messaging
How It Happens. Slack is a coworking platform that boasts over 8 million daily users, where plenty of information is passed back and forth between employees and senior staff. That could include sensitive internal documents and conversations.
Slack has increased its paid users from 2 million to 3 million in just one year, so hackers have a lot of incentive to keep targeting the platform. It’s already been hit a few times by cyber attackers. Slack bugs can be another security nightmare as well.
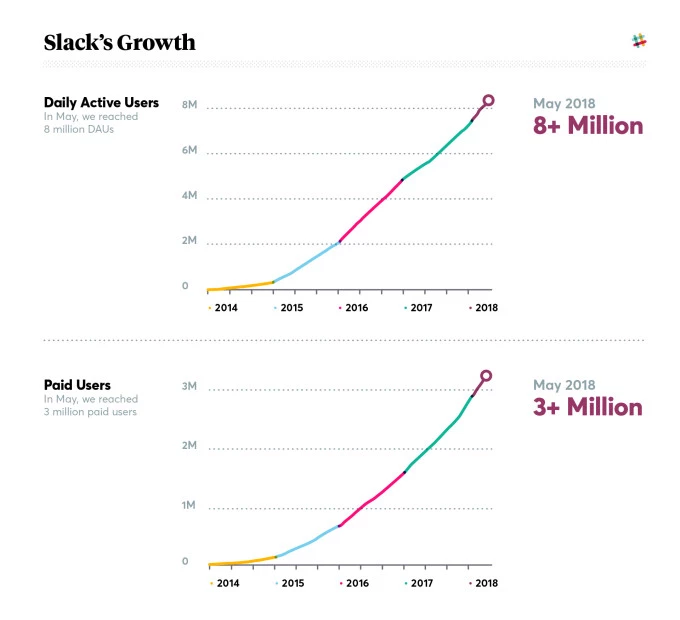
Image credit: TechCrunch
The Risk It Poses: Members of the same community can usually interact safely, but this doesn’t eliminate insider or outsider threats. It’s best not to share sensitive information like passwords, customer data, or corporate secrets in any chat room.
Using Slack? Here’s Our Guide To Covering These 5 Security Risks
Printed copies of passwords
How It Happens: Employees may print their passwords on paper, thinking that it will keep them from being hacked. But it won’t protect them from a determined cybercriminal who lives or works with them.
The Risk It Poses: Papers containing printed passwords could be misplaced, found by colleagues or friends who have access to the employee’s desk, or mixed up with other documents and thrown in the trash. Even if they’re hidden from the internet, they can be stolen locally.
Aside from all these threats, passwords on paper defeat the aim of having a secure retrieval system for easily remembering passwords. Instead, employees will find themselves looking through long lists of passwords to find the right one.
G-Suite password storage files
How It Happens:Data is saved in real time on G-Suite, but employees are also likely to unwittingly delete data. They might think that the deleted files can be recovered, but the available time frame is limited, after which the data is lost for good.
In fact, G Suite has many risks associated with it, from ransomware to third-party apps to errors in sharing permissions.
The Risk It Poses: Data stored in the cloud, which includes G-Suite, is open to malware attacks. Period.
Third-party apps may request permission to send messages for users, delete or edit data, and other requests that can alter data. While these third-party add-ons aren’t necessarily bad, they do increase your risk exposure.
In short, a cybercriminal who successfully hacks into these third-party services can take advantage of them to alter your data.
Handwritten notes with login credentials
How It Happens: This habit is similar to that of printing out passwords, and the risks are the same – people close to your employees can quickly get ahold of these passwords and flush your hard work down the drain.
The Risk It Poses: It’s dangerous to have login details in plain sight, and since employees’ friends, family, and coworkers are likely to be familiar with their handwriting, that poses an additional risk. A password manager can reduce or even eliminate your risk exposure.
Instituting Better Password Control
If you don’t have a password manager in place, you really have no idea how your users are sharing passwords – which means they’re probably engaging in some – or all – of the bad habits described above.
The truth is, password sharing happens and is necessary within organizations for a variety of reasons, such as vacationing staff members or absentees needing to share their login details to ensure projects are completed while they’re out of the office.
So, password sharing is inevitable, and it’s done for good reason. But how your employees share passwords matters; otherwise they may unknowingly expose your organization to cyber attacks.
Your employees are probably sharing passwords via unsafe channels because they don’t understand the implications of sharing passwords in that way. The best answer is to use a password manager; but in addition, make sure to take the following steps.
Teach your employees the risks of not sharing passwords securely
According to ZDNet, 14% of European employees would give out their company’s passwords for £200 or less, not realizing that it could cost the company millions. This is because employees don’t understand the true value of data, and what can happen if it falls into the wrong hands.
If a security breach does occur, it’s very likely to come from your employees sharing passwords via vulnerable channels. You want to make them see how this isn’t helping them, the customers they serve, or your company.
Promote organization-wide awareness for your company’s telecommuting policies
Remember the Information Age report that states that less than 1 in 5 employees know their company’s telecommuting policies? If employees don’t know the policies, they don’t know the right way to handle password sharing, e.g. a password manager.
And without a tool in place to monitor password usage, you don’t have any visibility into what’s actually happening.
Simplify your organization’s password management policies
If employees are already stressed and overwhelmed, and your password control policies and management system are a jumbled mess, elaborate password control measures probably won’t be followed.
In fact, Americans are growing increasingly tired of complex password practices. A FICO survey of 2,000 adults found that:
- 81% don’t see the need for what they consider unnecessary security procedures
- 64% are annoyed by the need for elaborate passwords featuring a mix of numbers, symbols, and capital letters
- 48% are tired of the use of two-step verification, and 71% are frustrated by captcha codes
Password managers like Password Boss help you simplify your password sharing and management safely.
Use a password manager
If you don’t have a password manager and/or a strong password policy, you put individual users in charge of figuring out how to keep their passwords safe. There’s probably no other aspect of your business where you put this much control in the hands of your employees – and you shouldn’t be doing it with passwords, either.
Look for an option that’s both secure and easy to use
Experts have proposed several solutions that are either difficult to remember or entirely impractical. In some cases, they’re even contradictory. One expert might say you should never write passwords in a book because it could get stolen, while another might say it’s best to write them in a book in order to avoid malware attacks and cyber theft.
The challenge is that malware attacks are just one of many ways attackers steal passwords. In fact, most employees share passwords by word of mouth.
A password manager like Password Boss doesn’t have any of the problems that come with improper offline or online password storage. A password manager helps you create strong passwords and store them in an encrypted database. You can also share passwords without exposing yourself and your organization to any risk.
Educate, educate, educate
Educating your employees is an investment that may save you millions of dollars. This is especially true in a world where employees are willing to sell their access privileges for a small amount of money.
Here are some things every company should do to start:
- Develop a policy that defines explicitly who should have access to different passwords or password privileges.
- Make employees aware of the stakes of improper password sharing. Make it clear that doing so puts the company’s financial livelihood – and their jobs – at stake.
- Offer thorough training on your chosen solution, and make yourself available for ongoing support, as needed.
- Pay particular attention to those who are responsible for onboarding or provisioning accounts for new hires or guest users.
And of course, provide your employees with a safe environment to create, manage, and share passwords with a good password management platform. That environment will also give you insight into what’s happening.
Not all password management solutions are born equal, so look for one that offers quick set-up, advanced security features, cross-device access, and is easy and affordable to use. With the right education and the right password management software, you can protect the safety and security of your business now and into the future.
What steps does your company take to secure company passwords? Do you use a password manager? Share your thoughts in the comments below: