
It's as if a robber were to break into a bank today and stay there until Christmas before someone noticed.
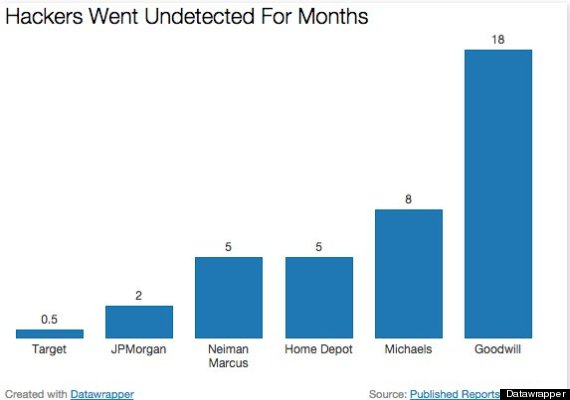
That's how long hackers had access to JPMorgan Chase's computer system, The New York Times reported this week. If two months seems like an eternity for cyberthieves to wander through the computers of the country's largest bank, consider that hackers have had free rein for even longer at several major retailers this past year.
Hackers resided on the computers of Neiman Marcus for five months, Home Depot for five months, arts and crafts store Michaels for eight months and Goodwill, the thrift store, for a year and a half.
That hackers were able to roam through JPMorgan's computer network for two months is another sign that companies are struggling not only with keeping cybercriminals out, but with spotting them once they get in.
A spokesman for JPMorgan did not respond to a request for comment. The bank said earlier this month that hackers had compromised the data of 76 million households, but that no money or Social Security numbers were stolen and the bank hadn't seen any unusual customer fraud.
The length of time that hackers reside on a computer system doesn't always correlate to the number of people affected. The size of the company's customer base also makes a difference. Target, for example, said 40 million customers had their payment card data compromised during an attack last fall that lasted just two weeks, while Michaels said that a much smaller number -- 3 million people -- were affected during its eight-month attack.
Still, the length of time of a data breach matters. Unlike real-life bank robbers who escape in minutes, digital bank robbers can take weeks or months before they gain access to the data they're after.
"A lot of people think hacking happens overnight and the the bad guys break into the network and they're done," said Aleksandr Yampolskiy, chief executive officer of SecurityScorecard, a cybersecurity firm. "The reality is it takes a long time."
Hackers are able to go undetected for so long because they use numerous techniques to disguise their activities. For one, they often attack computers using malicious software that doesn't set off alarms with anti-virus programs. And once inside, they route the data they steal through a series of intermediary computers, for example at a church or a public school, according to Yampolskiy. Such computers seem innocent to security teams and avoid raising red flags by communicating directly with computers in Russia, where many hackers are based, he said.
Some cybercriminals even fix the security flaws that allowed them to gain access to a computer network in the first place, like a burglar breaking a window and then replacing it before he leaves so nothing appears amiss.
But Yampolskiy said perhaps the biggest reason that hackers go unnoticed is that security teams are often overwhelmed with data. Companies will spend millions of dollars on sophisticated intrusion detection systems and vulnerability scanners that set off numerous alarms, many of which aren't serious. A security engineer at a company with 4,000 employees might get an alert every time an employee visits a suspicious website on the network, for example.
While those security tools are supposed to help keep hackers out, they create an avalanche of alerts that allow hackers to blend in.
"You get so much information that the event that matters is buried in those security logs," Yampolskiy said. "It's like looking for a needle in a haystack."