The time to respond and mitigate DDoS attacks can be costly for companies, and some businesses can lose roughly $2.5 million on average per attack, a research report released today said.
Neustar, an analytics firm that sees swathes of DDoS attack telemetry daily, boiled down some of the figures in a dispatch, its annual Worldwide DDoS Attacks and Cyber Insights Research Report, on Tuesday.
The data was culled from a survey it carries out bi-annually to track the shifting trends of DDoS attacks; 849 of the 1,010 organizations it surveyed, 84 percent, had been hit by a DDoS attack. A slight tick more, 86 percent, of respondents, had been hit by a DDoS attack multiple times.
Together, the 849 companies lost $2.2 billion in revenue over the last 12 months responding to the attacks, according to the report.
One company, a video gaming firm based in the US that makes $1M an hour in revenue, said it was attacked between two to five times in the last 12 months. While the company is at the high end of the spectrum, Neustar claims each DDoS attack may have cost the firm between $12M and $30M to mitigate, assuming the attacks take three hours to detect and three hours to respond to.
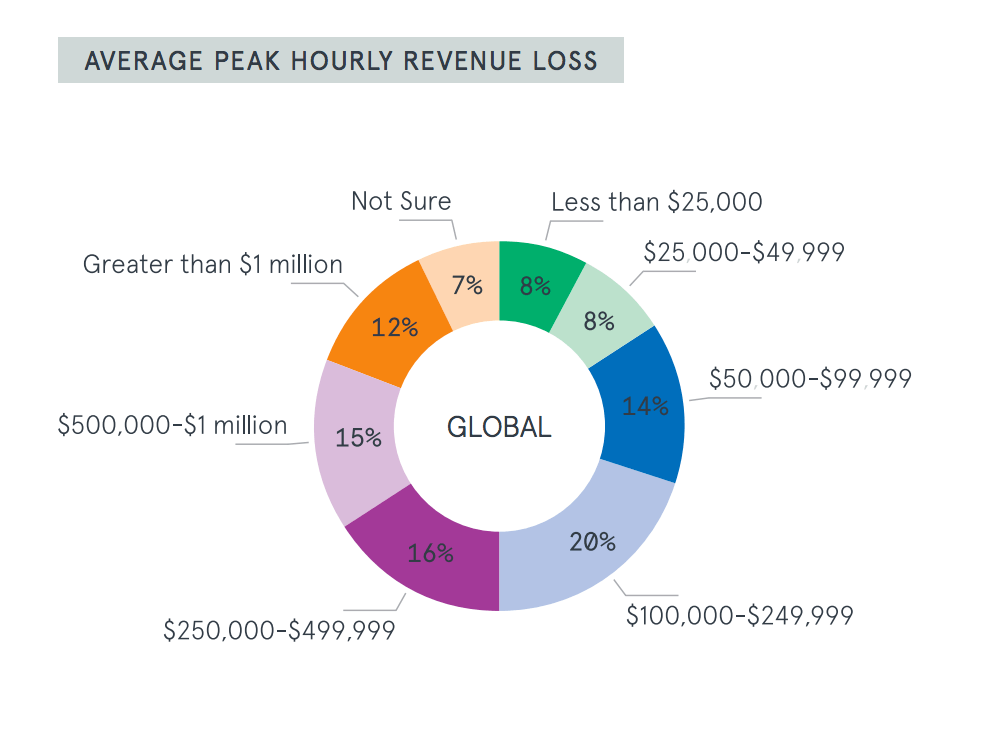
For 63 percent of the companies Neustar talked to, a DDoS attack can amount to a loss of $100,000 in revenue per hour. That’s up 13 percent, from 50 percent in 2016, the firm says. Attacks can cost even higher, $250,000 per hour, for 43 percent of organizations it talked to, according to the report.
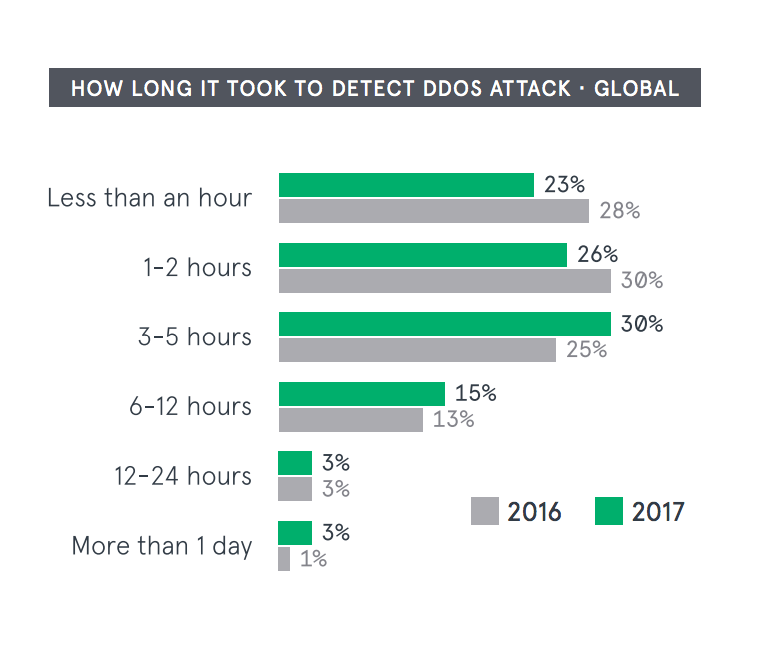
While it’s getting pricier to fix DDoS attacks, the firm said it’s taking longer to detect and deal with DDoS attacks as well. More than half, 51 percent of attacks the company has followed so far this year, have taken at least three hours to address. While on the whole, companies are still mostly finding out about attacks via their internal security teams, those numbers are down in 2017. Instead, there’s been a spike in organizations finding out about attacks through their customers. So far this year, 40 percent of respondents said they learned of a DDoS attack through their customer base, up from 29 percent last year.
The figures come as DDoS attacks continue to grow and diversify. The second half of the report points that there’s been an uptick in the number of mitigations Neustar has seen its customers deploy during the past year, an increase in the average size of attacks its seen mitigated, and a higher average peak attack size. The firm claims attacks are leveraging multiple vectors, and using botnets to carry out larger packet per second traffic, something that results in larger average attack sizes.
The company says multivector attacks, attacks that combine ICMP, UDP, and DNS, are clearly on the upswing. One of the biggest attacks the firm observed over the past few months exceeded 100 Gpbs and used UDP, multiple TCP, and ICMP. Attackers are becoming so motivated to bypass defenses they’ve begun adopting multiple attack vectors to get the job done.
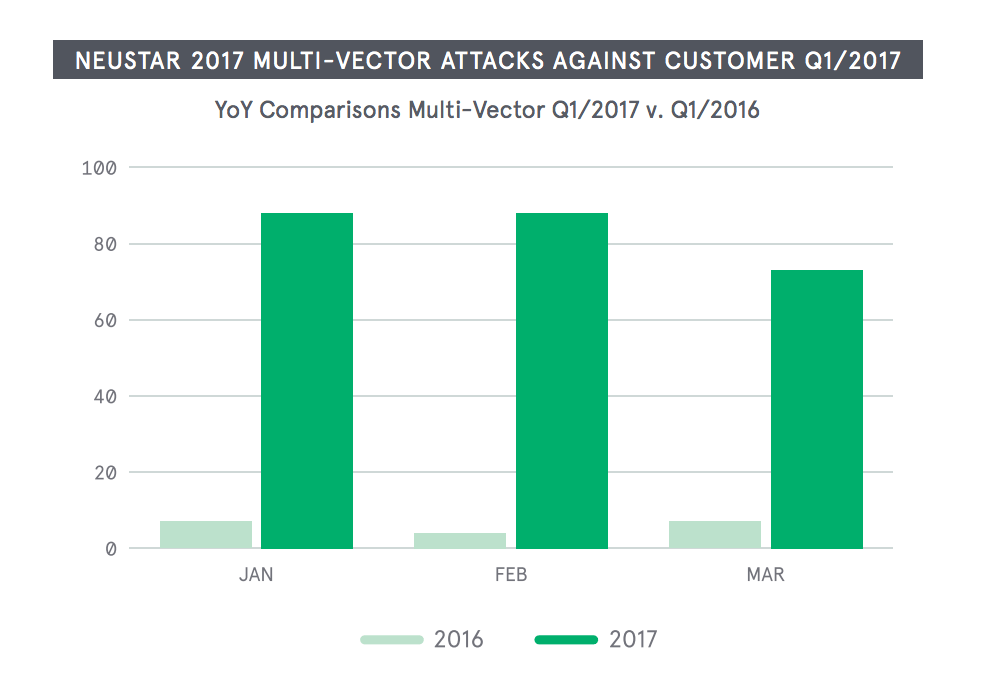
At the end of last year multivector attacks totaled 71 percent of the attacks the firm saw; that number is up to 81 percent over the last three months alone, according to the report.
Only a small part of the report is devoted to Mirai, the botnet that ensnared more than 103,000 IP addresses and knocked dozens of sites offline last fall. The firm says activity relating to the botnet – for now at least – has been slower in volume and smaller in size over the year’s first three months.
Mirai attacks haven’t gone away but aside from a 54-hour DDoS attack on a U.S. college in February, they haven’t commanded as many headlines over the last few months.
While Neustar says it doesn’t expect these trends to hold, it’s possible that Hajime, an IoT botnet first uncovered a few weeks back, could be helping drag down those Mirai numbers. The vigilant malware, which helps close off vulnerable Telnet ports used by Mirai, had infected upwards to 185,000 devices by the end of April.
“They are both competing for the same resources, so it’s a constant battle of good versus evil in the IoT landscape at the moment,” Travis Smith, a senior security research engineer at Tripwire, told Threatpost last month of the Mirai/Hajime battle.