Microsoft Authenticator is a pleasant enough two-factor authentication app. You can use it to generate numeric authentication codes for accounts on Google, Facebook, Twitter, and indeed, any other service that uses a standard one-time password. The login process is straightforward: first you sign in to each site with your username and regular, fixed password, then you use the code generated by the app.
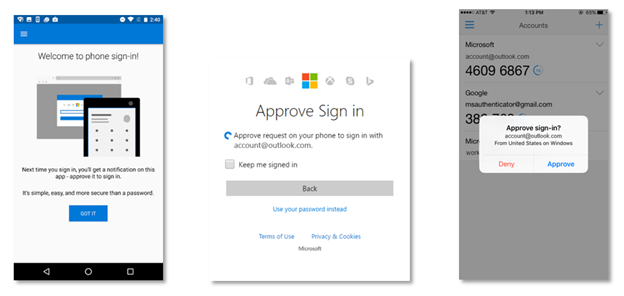
But for Microsoft accounts, Redmond is offering something new: getting rid of that first password and using just the phone to authenticate. With phone-based authentication enabled, after entering your Microsoft Account e-mail address, you'll receive an alert on your phone. From that alert, you can either approve or reject the authentication attempt—no password necessary.
This same approve-or-reject choice on the phone has been offered previously to Microsoft Accounts, but in the past, it still required the use of the fixed password.
The Authenticator app is available for iOS, Android, and Windows 10 Mobile, but regrettably, while the first two include the new feature, Microsoft has not seen fit to add it to the version of the software that runs on its own platform, citing low usage. The eternal chicken-and-egg situation of low usage both causing weak app support and being caused by weak app support continues to be something that Microsoft has little interest in fixing.
The new authentication is also strictly limited to Microsoft Accounts; Office 365 and Azure Active Directory are not presently supported. For those who would prefer to keep the traditional password, Microsoft Account passwords also appear to still be restricted to a mere 16 characters.
reader comments
126