Hackers are getting more impish by the day. Security researchers have discovered a new hacking vector for Chrome that prompts users to download a ‘missing font’ and then tricks them into installing malware on their systems.
The infection was first spotted by Mahmoud Al-Qudsi from cybersecurity firm NeoSmart Technologies, which has since detailed the attack in a blog post.
The researcher initially noticed the trap while browsing an unnamed WordPress website that was allegedly already compromised. Unlike other worn-out attacks, this one was particularly well-disguised.
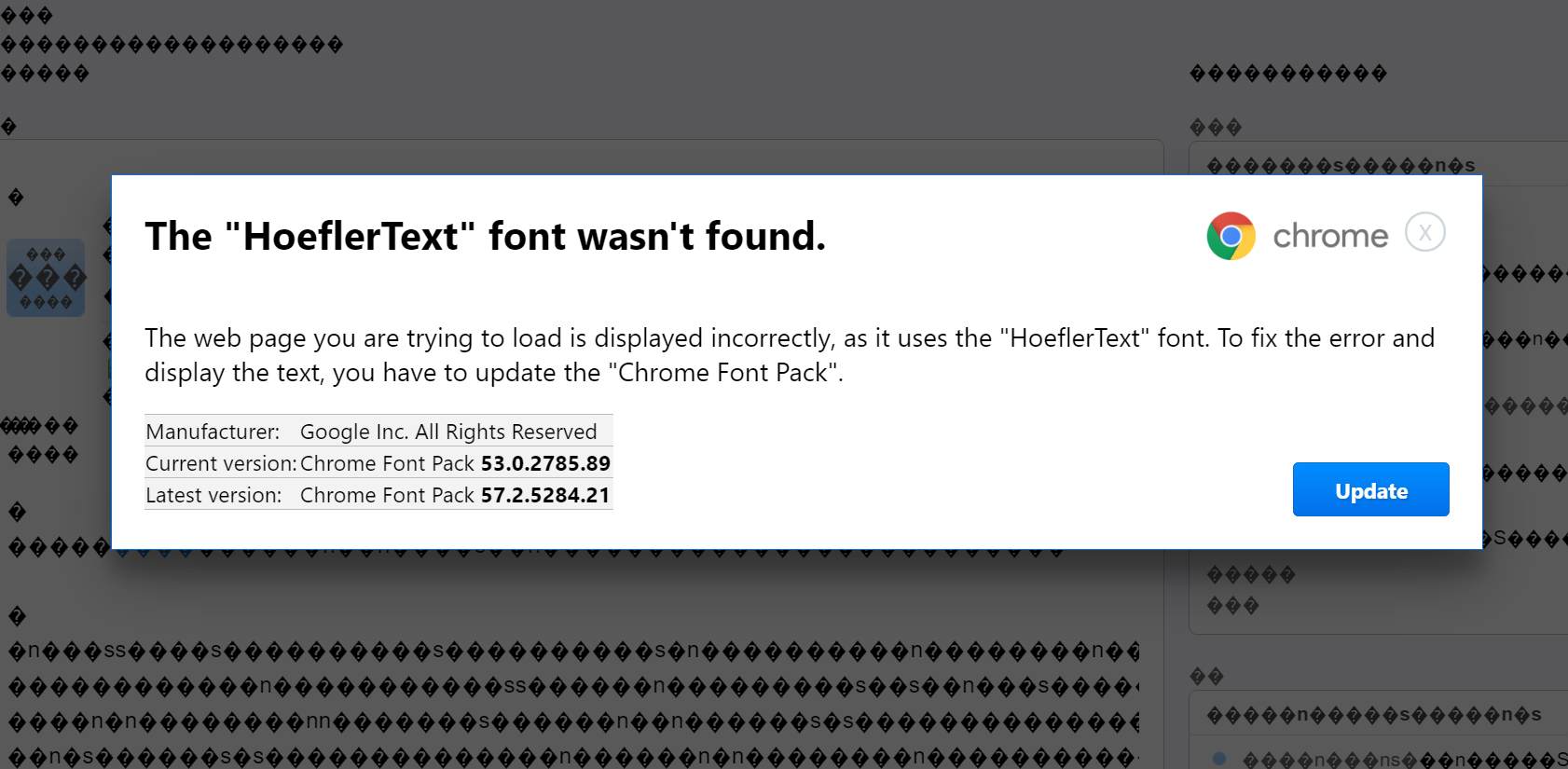
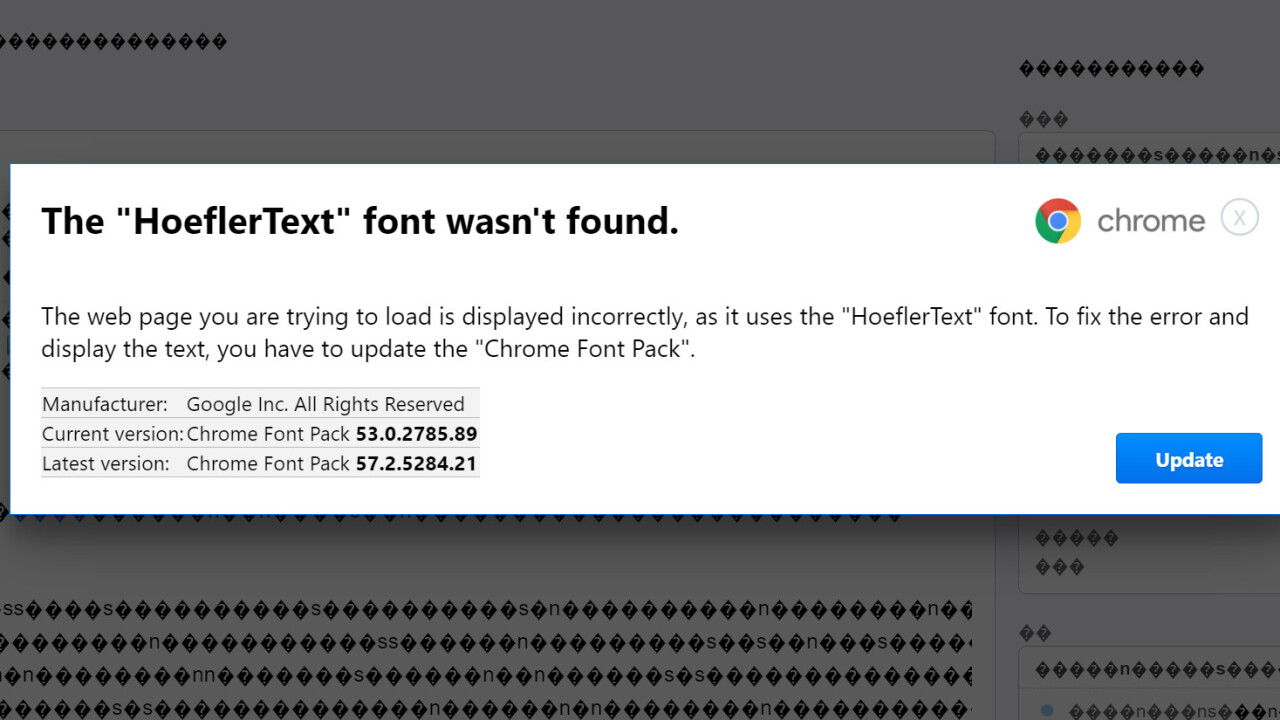
The hackers fundamentally use JavaScript to tamper with the text rendering, causing it to resemble mis-encoded text in place of actual content. The script then prompts users to fix the issue by updating the ‘Chrome font pack.’
What makes the attack especially sly is the subtle hacking vector it employs. In addition to the credible premise involving the ‘missing font,’ the dialog window has also been formatted to accurately resemble an actual Chrome pop-up: It uses the correct logo as well as the correct shade of blue for the ‘update’ button.
As NeoSmart Technologies point out, there are a few “tell-tale signs” that ought to alert careful users. For one, the dialog window has been hard-coded to display the user is running version 53 of Chrome – a clue that could tip off some users running other reiterations of the browser that something might be off.
Additionally, while clicking ‘Update’ will proceed to download a file titled “Chrome Font v7.5.1.exe,” the name of the downloaded file doesn’t match the one displayed in the malicious instruction image, which reads “Chrome_Font.exe.”
Despite this, researchers warn that as of now Chrome still fails to filter out the file as malware – it is, however, blocked by the standard “this file isn’t downloaded often” warning. Windows Defender similarly misses to label the file as malicious.
The security firm has since ran the malware through VirusTotal, which reveals that at present only nine out of the 59 anti-virus scanners in its database are accurately identifying the file as malicious.
NeoSmart Technologies has documented the hacking vector in more detail at their official blog. Head to this page to get the full report.
Get the TNW newsletter
Get the most important tech news in your inbox each week.