
At the end of January, WordPress 4.7.2 was released to fix four security issues, three of which were disclosed at the time of the release. These included a SQL injection vulnerability in WP_Query, a cross-site scripting (XSS) vulnerability in the posts list table, and the Press This feature allowing users without permission to assign taxonomy terms. The fourth and most critical issue, an unauthenticated privilege escalation vulnerability in a REST API endpoint, was fixed silently and disclosed a week after the release.
Contributors on the release opted to delay disclosure in order to mitigate the potential for mass exploitation, given that any site running 4.7 or 4.7.1 is at risk. This allowed time for users to update manually and for automatic updates to roll out.
“We believe transparency is in the public’s best interest,” WordPress Core Security Team Lead Aaron Campbell said. “It is our stance that security issues should always be disclosed. In this case, we intentionally delayed disclosing this issue by one week to ensure the safety of millions of additional WordPress sites.”
WordPress worked with Sucuri, the company that discovered the issue, along with other WAF vendors and hosting companies to add protections before the vulnerability was publicly disclosed.
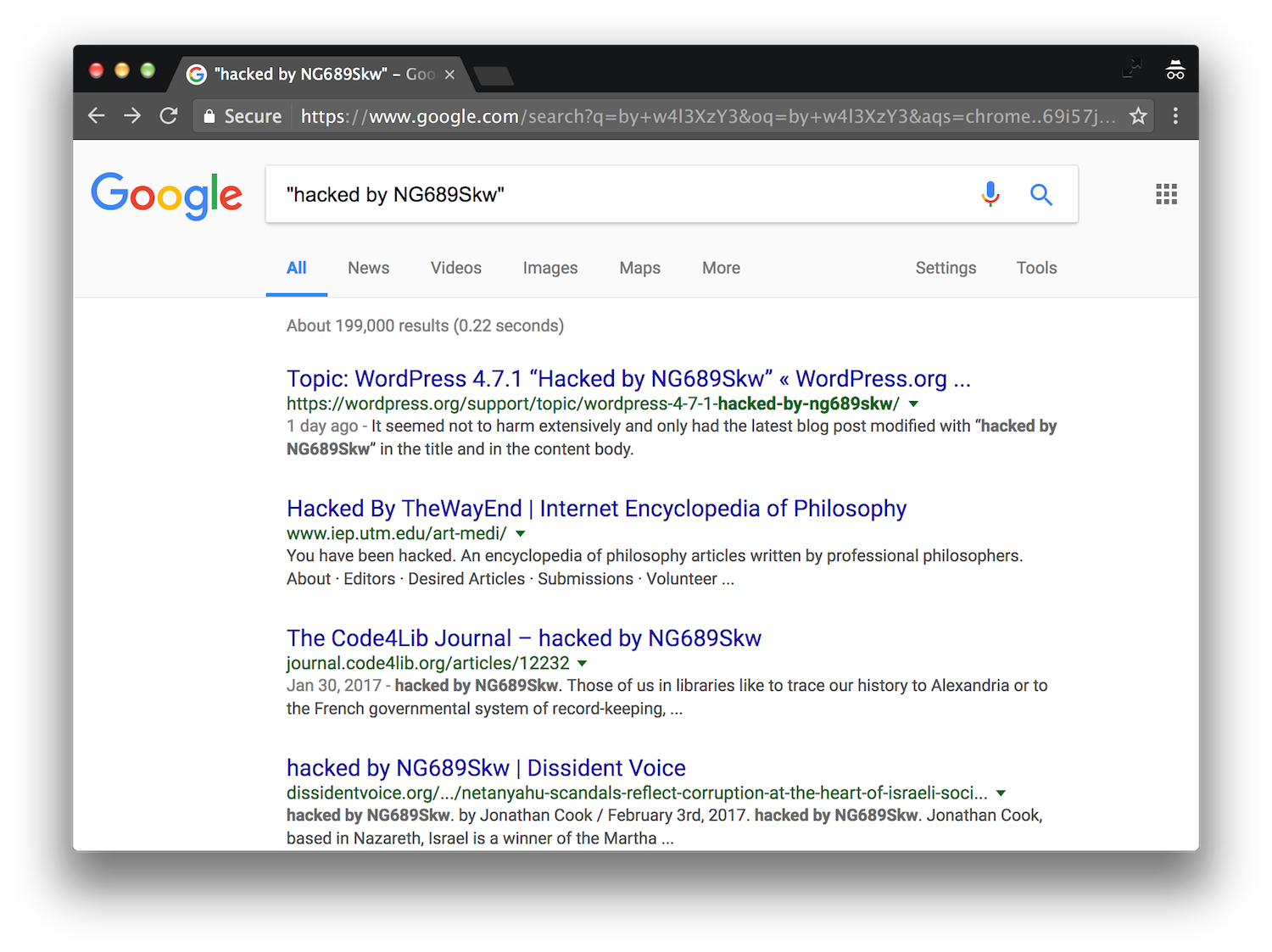
The vulnerability has been public for less than a week and is now being actively exploited. Thousands of WordPress sites have been defaced with messages like “Hacked by NG689Skw” or “Hacked by w4l3XzY3” or similar. Googling for information about these particular hacks returns thousands of other hacked sites in the results.
Sucuri founder and CTO Daniel Cid said his team saw exploits in the wild less than 24 hours after the disclosure. The attacks are primarily simple defacements so far.
“There are some good bad guys updating the post excerpt with the message: ‘Update WordPress or you will be hacked,’ which is kind weird,” Cid said. “But overall we’re seeing just simple defacement attempts, using modified versions of the exploit that was shared publicly.”
Multiple Campaigns Have Defaced Hundreds of Thousands of WordPress Sites
Sucuri is monitoring multiple defacement campaigns, each with varying degrees of success. The company published an update on the active attacks as well as the IP addresses they are originating from.
“We are currently tracking four different hacking (defacement) groups doing mass scans and exploits attempts across the internet,” Cid said. “We see the same IP addresses and defacers hitting almost every one of our honeypots and network.”
One defacement campaign Sucuri is tracking already has more than 68,000 pages indexed on Google. After perusing the WordPress.org forums, the problem seems to have a much larger reach than Sucuri’s network has initially detected. For example, “Hacked by NG689Skw” returns approximately 200K indexed results. “Hacked By SA3D HaCk3D” returns more than 100K results. There are multiple permutations of this defacement in play on WordPress websites across the web. Not all results that share this same campaign structure are guaranteed to be associated with this vulnerability, but the few listed above were recent posts on the WordPress.org forum from users who failed to update to 4.7.2 in time.
“On our end, we are seeing a big growth on exploit attempts, specially for defacement,” Cid said. “But SPAM SEO is slowly growing too.”
Cid said the vulnerability allows attackers to inject content into a post or page by default, but defacement is the easy first step, along with SEO spam. If a site has a plugin like Insert PHP or PHP Code Widget installed, the vulnerability can lead to remote code execution. These two plugins have more than 300K combined active installs and there are others that perform similar functions.
“The core of the issue is people not updating,” Cid said. “Even with auto and simple updates, people still do not update their sites.”
Needless to say, if you haven’t updated to 4.7.2 and your site is running 4.7.0 or 4.7.1, you are at risk for content injection. For most sites that have been defaced, the simplest solution is to update to the latest version of WordPress and rollback the defaced post(s) to a revision.
So a feature that sites didn’t need and will most likely never use, and by design can not be turned off makes a lot of damage…. who would have thought it could happen.
It is time that like it is expected from all plugin and theme authors, core will own its mistakes. (Not that the plugin authors do, ninja forms still provides its version two and three in the same plugin and it is probably only a matter of time until some bug will expose the users of the untested version two to hackers.)
Anyway, “decisions instead of options” assumes that the people that make the decisions make it based on the merits of the issues, and not based on social pressure and the need for “employee satisfaction”.
And yes I know that I am just ranting against the wind and nothing is going to change.