Over the past month, researchers have observed several new phishing campaigns that demonstrate a more sophisticated and targeted approach to social engineering by threat actors.
For example, on Monday Trustwave wrote about the Carbanak gang targeting the hospitality and restaurant sectors. The actors began the attack by using public tools such as LinkedIn to find the names of company department heads or other key employees. Then they called the organization’s customer service line and claim that they were having difficulties with the online registration system and ask to send the information via email. They would spend a significant amount of time on the phone with the employee — often dropping those researched names in order to build trust — until the employee eventually opened the malicious Word document attached in the email.
Finally, the organization would be infected with malware capable of stealing system information, taking desktop screenshots, and downloading additional tools such as point-of-sale malware.
Targeted Social Engineering Becomes Less Direct
Other threat actors are shifting towards similarly indirect paths of compromise — beginning their attacks with a message, or several messages, designed to build trust before attempting to cause harm. This is the case with recent business email compromise (BEC) scams, which the FBI has repeatedly warned is a growing problem for organizations.
“In most cases, a BEC scam attempts to portray an email or request as being urgent, placing pressure on the recipient to act fast without asking questions,” SurfWatch Labs noted in a blog post about the FBI’s July alert. “The email is often sent from a legitimate looking source — such as a high-ranking company official or a bank that works with the company — which further eliminates questions from the recipient.”
However, Symantec recently warned that BEC scams had shifted to a less urgent approach. Instead, most BEC scams now begin with a simple introductory message before requesting a fraudulent wire transfer, as this email exchange demonstrates:

In June, shortly before the FBI’s last BEC warning, just 20 percent of BEC emails began by inquiring about the recipient’s availability — with the rest directly requesting a wire transfer, according to Symantec. By October, 60 percent of the emails began with the more indirect approach of inquiring about the recipient’s availability.
A Look at SurfWatch Labs’ Threat Intelligence Data
Warnings of targeted attacks like the ones described above have led to spear phishing being the most common practice tag related to social engineering over the past 90 days, according to SurfWatch Labs’ data.

A wide variety of industry groups have been tied to spear phishing threats over the period. However, the most talked about cybercrime stories of the past month may have been the hacking and publication of emails from the Democratic National Committee and Hillary Clinton’s campaign chairman John Podesta, as well as what role those breaches had in shaping the recent US presidential election.
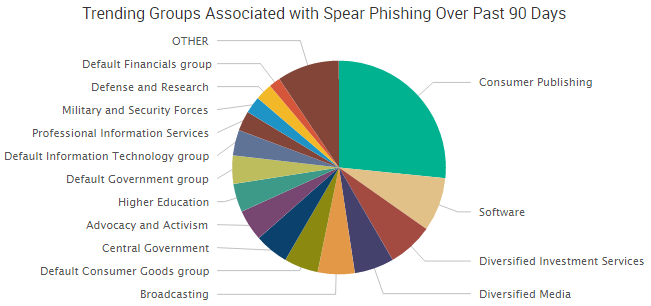
In those cases, the leaks have been tied to spear phishing emails from Russian hacking group Fancy Bear, one of the most prominent hacking groups related to spear phishing over the past 90 days, behind only Peter Romar, a 37-year-old Syrian national who recently pled guilty to his role in the Syrian Electronic Army.

Those Fancy Bear attacks used a particular tactic: the use of shortened URLs. As Esquire’s Thoma Rid wrote explained, those shortened URLs both tricked users into clicking malicious links at an alarming rate and, ultimately, helped researchers uncover the actors behind those targeted attacks:
To manage so many short URLs, Fancy Bear had created an automated system that used a popular link-shortening service called Bitly. The spear-phishing emails worked well—one in seven victims revealed their passwords—but the hackers forgot to set two of their Bitly accounts to “private.” … Between October 2015 and May 2016, the hacking group used nine thousand links to attack about four thousand Gmail accounts, including targets in Ukraine, the Baltics, the United States, China, and Iran. … Among the group’s recent breaches were the German parliament, the Italian military, the Saudi foreign ministry, the email accounts of Philip Breedlove, Colin Powell, and John Podesta—Hillary Clinton’s campaign chairman—and, of course, the DNC.
These breaches highlight some of the ways in which social engineering has continued to affect organizations across all sectors and how new techniques are incorporated in order to make it harder for individuals to detect suspicious activity.
That’s why training and awareness is often touted as the most important and cost effective step in combating social engineering, as we noted in a prior social engineering blog. Having the proper tools and training, along with up-to-date threat intelligence to inform them of the latest threats, can help organizations and their employees provide a better front line of defense against the evolving techniques used by threat actors.


One thought on “Recent Campaigns Highlight Evolving Social Engineering Tactics”