 nice touch). "/>
nice touch). "/>
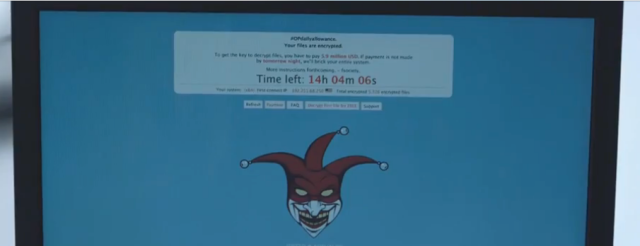
Near the intermission of Mr. Robot's two-part season two premiere, fsociety hacker Darlene boots her desktop computer and opens up something called the "Social-Engineering Toolkit." She scrolls through a list of options including a "Java Applet Attack" (done through a Remote Administration Tool) then chooses to unleash the "F-Society Cryptowall." Suddenly, tellers and high-level employees at one of the world's most powerful banks all stare at the same screen (above).
Ars readers will recognize this as another instance of art imitating life. And as Mr. Robot's premiere played out, the episode relied on a cryptoransomware story arc that could've been ripped from any number of headlines, including those high-profile Maryland hospital hacks. Similar to that real-life outcome, executives at fictitious E-Corp decide they could come up with the requested $5 million in the couch cushions and eventually pay up (or at least intend to).
As everyone from Wired to Forbes will tell you, the whole thing boasts tremendous accuracy. But the most impressive part: The writers initially wanted to do an entirely different kind of hack. The ransomware approach had to come together on short notice.
“We were going in a different direction, but as we started to peel back the onion—what systems do we need to compromise, how would this spread and move laterally around the systems?—we ran into a hiccup where we couldn’t get into this system easily,” Andre McGregor, the show's FBI consultant, told Ars. “Sam [Esmail] said, ‘Well if we can’t do it, we can’t do it. We’re not going to try and make it work, pretend that it works, or use art magic to do it. We’re going to have to rewrite everything.”
If Mr. Robot ultimately proves to be pop culture's best depiction of hacking culture, people like McGregor will be a big reason why. The Director of Cybersecurity at Tanium joined Mr. Robot as a consultant for S2 after show creator Sam Esmail encountered the company at CES. Before his latest role, McGregor spent his entire career in IT and security. He worked as an engineer at Goldman Sachs and became an IT director elsewhere before the feds came calling. "The FBI recruited me to come to the academy, and they taught me to take a punch, arrest people, shoot a gun, and then said 'let’s go fight some bad people who are hacking,'” he said.
McGregor worked with the FBI in the NYC office during some of the most high-profile hacks in the 21st century: incidents involving China, Russia, Iran, Anonymous, and Lulzsec. "There was never a quiet day as an FBI agent in NYC," he said. "There were times where I had trouble sleeping." In this week's Decrypted podcast (hosted by yours truly), he mentioned a few specific examples like Iran hacking US water dams and China exfiltrating US data.
TV hacking via Metasploit
Luckily, hacking for television has proven to be much less stressful for McGregor. He now brings almost unparalleled knowledge of both the bad guys and how the FBI would respond to the Mr. Robot's writers' room. Look for that red-headed FBI agent from the premiere to stick around a bit longer in S2.
“Sam is very much about accuracy," McGregor said. "He did not want to do or say anything that would not be done in the field either by agents or what would be done as a response to a cyber security attack. So as the show progresses, you’d have to think such an attack [like the five/nine hack on E-Corp from S1] would warrant a response from the government… This is exactly how our government operates today. When there’s a big intrusion, we need a response team.”
Though he didn't work on S1, McGregor admires what the show has done to this point. Things like the Raspberry Pi hack or the mass spear-phishing of e-mails were “exactly what I lived and breathed every day at the FBI." In particular, the integral role of the Dark Army—Mr. Robot's mercenary-ish Chinese hacking outfit—brings a smile to McGregor's face.
“I lived and breathed China for such a long time; it’s interesting to see it on TV," he said. "Watching a show like Mr. Robot, you juxtapose it with something like CSI: Cyber, and you say, 'Finally—a show that is reflective of the work that I do and the intricacies of hacking.' In many ways, it’s easy to do—I can open up Metasploit, create a package, and gain access—but in many ways it’s very complicated and not easy to show on TV.”
As for the ransomware attack in the season two premiere, it represents the standard operating procedure for Mr. Robot's writers. All ideas start in the show's core writers' room (which met last fall for S2) and then consultants like McGregor come in later in the process. When McGregor met with staff in January, the framework of S2 episodes was already in place, and he could then plug in ideas to help increase the accuracy of show. "With this particular hack [what became the ransomware attack], everything was in place," McGregor said. "But when I had to come up with the tech screenshots, I realized it wasn't feasible." (McGregor wrote a bit more about the process on his Tanium blog.)
You read that correctly. In order for a hack to appear in the show, writers and consultant will attempt to execute it in real life. It's a big reason why screenshots of those lines of code inspire many a blog post. When McGregor's original white hat-testing failed, he then went back to Esmail and the writers, who empowered McGregor and head technical writer Kor Adana to come up with a more viable alternative.
“We wanted to do a big hack in episode one that affected E-Bank, and one of the ideas we came up with was to do ransomware—it's very topical and it affects businesses today," McGregor said. “So I got the opportunity to dust off my pen-testing skills from the FBI. I opened the Metasploit framework, did some customization, and what was shown [in the episode] was a bit of my own technical artwork for the show. That's pretty cool."
McGregor joked that he might have to save his own screenshots of the episode to share across social media, but he admitted an even cooler keepsake will be revealed this season. During our conversation, he mentioned that a character would appear on the show in his honor named "FBI Andre," similar to how fellow consultant James Plouffe had a doppelganger in S1. However, Plouffe's TV parallel ended up being the E-Corp exec who tragically kills himself during a press conference—so McGregor requested that FBI Andre avoid a similar fate. If you follow McGregor on Twitter (@AndreOnCyber), you may have already seen a hint about his namesake's introduction. And like McGregor's contributions at large, look for FBI Andre to also stick around.
Hear Andre McGregor below on this week's episode of Decrypted, Ars Technica's Mr. Robot podcast. If you've got questions for McGregor going forward, get in touch through the comments section, on iTunes, or via e-mail.... he may come back on later in the season.
Listen
- Direct Download URL: Decrypted, Ep. 2: This is how you pen test for Sam Esmail
- Listen or subscribe on Stitchr
- Listen or subscribe on Soundcloud
- Subscribe via RSS
- Subscribe via the iTunes store
reader comments
43