Many companies approach achieving better security the way some people approach achieving better fitness. They spend a lot of money buying a Security Information and Event Management (SIEM) product, much like the way people will purchase an expensive health club membership. But if the company does not follow through and use the SIEM properly, they will fail. Same with people and health clubs – paying for it is just the first step; it is no guarantee of results. So it is imperative to focus on the fundamentals of SIEM logging in order to succeed. This is a 3 part blog to help you understand these fundamentals.
Why SIEM log analysis and management is paramount
Successful attacks on computer systems rarely look like real attacks except in hindsight – if this were not the case, we could automate ALL security defenses without ever needing to employ human analysts. This is why it’s important to know what is in your log files, even in hindsight – they are often the only way to detect attacks.
In fact, if you didn’t know better, your own network and system Admins might look a lot like hackers. They are often using elevated privileges to make changes that could look (or be) malicious. So it is important to have more information and insights in order to effectively detect malicious behavior.
Security Information and Event Management (SIEM) is about looking at your network through a larger lens than can be provided by a single security control or information source. For example:
- Your Asset Management system only sees applications, business processes and administrative contacts.
- Your Network Intrusion Detection system (IDS) only understands Packets, Protocols and IP Addresses
- Your Endpoint Security system only sees files, usernames and hosts
- Your Service Logs show user sessions, transactions in databases and configuration changes.
- File Integrity Monitoring (FIM) systems only sees changes in files and registry settings
None of these technologies, by themselves, can tell you what is happening to your network and your business. Hence, the great interest in SIEM, in companies of all sizes.

Cloud-based SIEM solution
Threat detection, incident response, and compliance in a single, cloud-based platform.
Learn moreReviewing SIEM terminologies
First, let’s set some terms. Although the industry has settled on the term ‘SIEM’ as the catch-all term for this type of security software, it evolved from several different (but complementary) technologies before it.
- LMS - “Log Management System” – a system that collects and store Log Files (from Operating Systems, Applications) from multiple hosts and systems into a single location, allowing centralized access to logs instead of accessing them from each system individually.
- SLM /SEM– “Security Log/Event Management” – an LMS, but marketed towards security analysts instead of system administrators. SEM is about highlighting log entries as more significant to security than others.
- SIM – “Security Information Management” - an Asset Management system, but with features to incorporate security information too. Hosts may have vulnerability reports listed in their summaries, Intrusion Detection and AntiVirus alerts may be shown mapped to the systems involved.
- SEC - “Security Event Correlation” – To a particular piece of software, three failed login attempts to the same user account from three different clients, are just three lines in their log file. To an analyst, that is a peculiar sequence of events worthy of investigation, and Log Correlation (looking for patterns in log files) is a way to raise alerts when these things happen.
- SIEM – “Security Information and Event Management” – SIEM is the “All of the Above” option, and as the above technologies become merged into single products, became the generalized term for managing information generated from security controls and infrastructure. We’ll use the term SIEM for the rest of this presentation.
SIEM is essentially a management layer above your existing systems and security controls. SIEM connects and unifies information from disparate systems, allowing them to be analyzed and cross-referenced from a single interface. Bear in mind, SIEM is only as useful as the information you put in it – the old adage “Garbage In, Garbage Out” pertains in this situation.
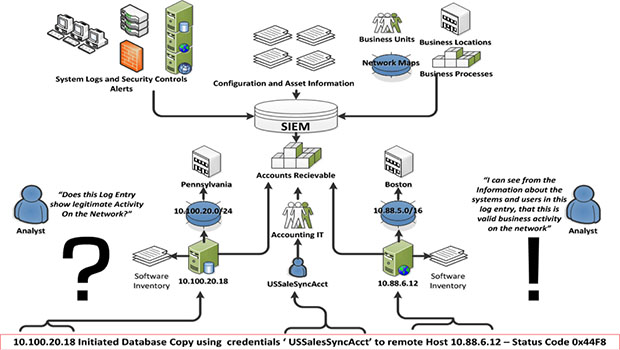
Oh, and it’s often a complicated situation. See below an example of how the SIEM is required to look at a log entry and the “many moving parts” that must be considered to make a valid decision as to whether this is a valid business activity on the network.
SIEM is not a security control or detection mechanism by itself, but it makes the security technologies you have more effective. It enables the whole to be greater than the sum of the parts.
SIEM is about collecting logs, and mapping information about your infrastructure and business processes to those logs. It empowers security analysts to make reasoned, informed investigations into activities on the network to determine their impact on security integrity and business continuity.
The SEIM should act as your single portal to activity on your network, decoupling your analysts from a need to have product-specific knowledge about security capabilities. This allows them to focus on what they do best – security analysis.
In the final analysis, SIEM by itself does not do very much – it is akin to a “Database without Data.” However, the more information you put into it, the more useful and insightful it becomes. The critical consideration is feeding the SIEM the logs it needs to make it effective.
Learn more about AT&T Cybersecurity's SIEM and SIEM logging capabilities