
The catastrophic Heartbleed security bug that has already bitten Yahoo Mail, the Canada Revenue Agency, and other public websites also poses a formidable threat to end-user applications and devices, including millions of Android handsets, security researchers warned.
Handsets running version 4.1.1 of Google's mobile operating system are vulnerable to attacks that might pluck passwords, the contents of personal messages, and other private information out of device memory, a company official warned on Friday. Marc Rogers, principal security researcher at Lookout Mobile, a provider of anti-malware software for Android phones, said some versions of Android 4.2.2 that have been customized by the carriers or hardware manufacturers have also been found to be susceptible. Rogers said other releases may contain the critical Heartbleed flaw as well. Officials with BlackBerry have warned the company's messenger app for iOS, Mac OS X, Android, and Windows contains the critical defect and have released an update to correct it.
The good news, according to researchers at security firm Symantec, is that major browsers don't rely on the OpenSSL cryptographic library to implement HTTPS cryptographic protections. That means people using a PC to browse websites should be immune to attacks that allow malicious servers to extract data from an end user's computer memory. Users of smartphones, and possibly those using routers and "Internet of things" appliances, aren't necessarily as safe.
Chief among vulnerable devices are those running Android. While exploiting vulnerable handsets often isn't as simple as attacking vulnerable servers, the risk is high enough that users should tightly curtail use of their Android devices until users are sure their handsets aren't susceptible, Lookout's Rogers advised.
"If you have a vulnerable device and there's no fix available for you, I would be very cautious about using that device for sensitive data," he told Ars. "So I would be cautious about using it for banking or sending personal messages."
How Android phones are vulnerable
Rogers said the most likely scenario for an attacker exploiting a vulnerable Android device is to lure the user to a booby-trapped website that contains a cross-site request forgery or similar exploit that loads banking sites or other sensitive online services in a separate tab. By injecting malicious traffic into one tab, the attacker could possibly extract sensitive memory contents corresponding to the sites loaded in other tabs, he said. A less sophisticated version of the attack—but also one that's easier to execute—might simply inject the malicious commands into a vulnerable Android browser and opportunistically fish for any sensitive memory contents that may be returned.
Luckily, Android's security sandbox design prevents a malicious app from being able to access memory contents used by separate apps. Also fortunate is the fact that the majority of Android phones aren't susceptible. Still, the risk shouldn't be dismissed. About 34 percent of Android devices run on version 4.1.x of the mobile OS, according to figures supplied by Google. Google has said it's working with partners to roll out a patch, but as Ars has chronicled before, millions of Android smartphones never, or only rarely, receive available updates that patch dangerous security defects.What's more, the threat of a vulnerable Android device being exploited by someone on the same Wi-Fi network as the targeted user, or by someone combining a Heartbleed attack with a separate exploit, should be enough to give people pause, even if they don't intend to visit banking sites or connect to Web-based e-mail or other sensitive services, Rogers counseled.
"The risk is that someone could either man-in-the-middle your Internet connection or use a cross-site request forgery-type attack or could use some kind of malicious thing to trick you into doing something secure and then fish out your secure credentials while you do that," he said. "That risk is sufficiently high as to say that you should be careful if your device is vulnerable."
Because Android is frequently customized for specific devices or manufacturers, it's possible some versions besides 4.1.1 and 4.2.2 are vulnerable. For that reason, Android users should download Heartbleed Detector, a free app developed by Lookout. In the vast majority of the tests Ars carried out, it found various Android versions contained a vulnerable version of OpenSSL, but that the Heartbeat extension that hosts the coding bug wasn't enabled, making the devices immune to attack. The sole exception was when Ars executed the app on a handset running version 4.1.1, which returned the screenshot below.
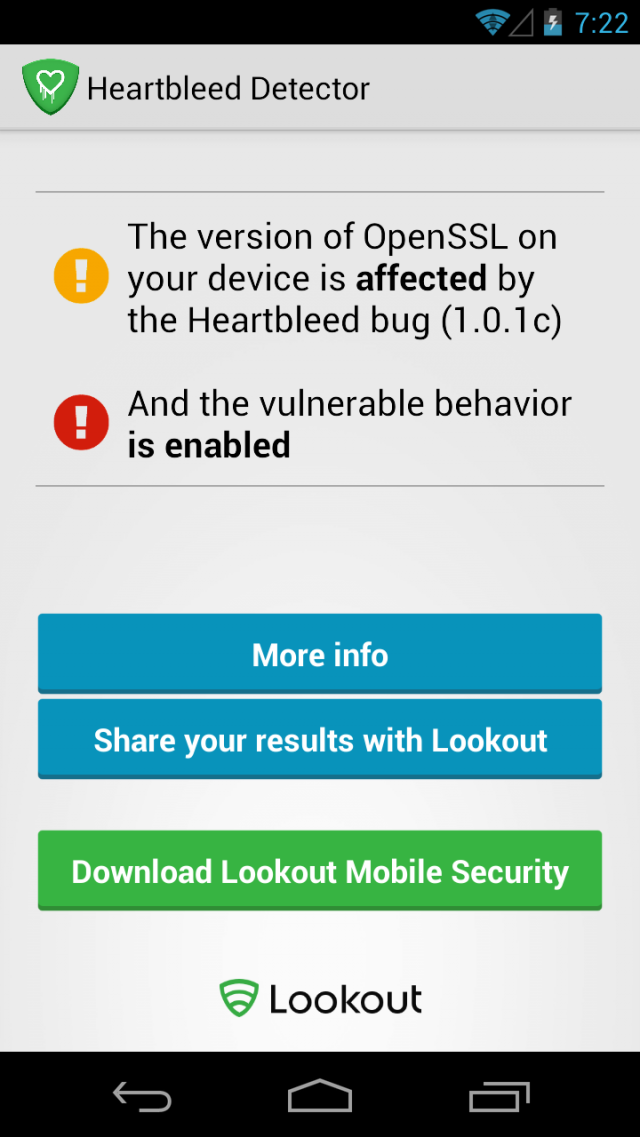
Security researchers have only begun to analyze the risks Heartbleed poses to people using home and small-office Internet routers, modems, and all kinds of other devices that rely on OpenSSL. It's too early to say which, or how many, of the appliances are susceptible to exploits that extract passwords or other data. But until more thorough audits are performed, users shouldn't rule out the possibility.
reader comments
101