5 Ways to Use Virtual Desktop Infrastructure (VDI)
Achieving virtualization through Virtual Desktop Infrastructure (VDI) opens businesses to a wide variety of opportunities for growth. Not only does it limit or completely rid of on-prem machinery, but it also allows for faster, more accessible data that can remove the boundaries and limits businesses have with traditional IT infrastructure. Many people only scratch the surface when understanding VDI and all it can do for businesses but here in this article, we’re uncovering how you can transform and even expand your business with 5 different ways you can use VDI.
It's no secret that anything stored in the cloud saves you time and money. Virtual Desktop Infrastructure is no different. In fact, it opens up the floodgates for a more flexible and an even more reliable way of doing business. From the ability to create a highly personalized workspace to avoiding maintenance costs and software update costs, VDI offers more secure and reliable resources than one can count. Before a company switches to VDI however, it’s important to understand how VDI fits into the organization and what would work best for the company. For example, will it be best to opt for a persistent virtual desktop infrastructure or a nonpersistent infrastructure? Once questions like these are answered, you can move on to enjoy the awesome benefits of utilizing VDI. Here are 5 ways to use VDI for your business:
- Remote, Local, and Hybrid Workers
- Kiosk, Task, and Contract Workers
- Customer Support Staff
- BYOD Deployments
- Positions involving Graphic-Intensive Applications
Remote, Local, and Hybrid Workers
One of the most popularly known ways to use VDI is to expand the flexibility of the workforce by enabling remote, local, and hybrid workers. VDI is hosted on a centralized server and all Virtual Machines (VM’s) must be host-based. End clients are then connected to a central server. Once the connection is established, a virtual desktop is automatically located from the available options. Afterwards, the VM monitor (VMM) or hypervisor, creates, manages, and runs VDI VM’s.

This enables users to connect from anywhere to a specific desktop environment. This is great for companies that have limited office space or can’t provide all employees with additional laptop or desktop equipment. Most businesses worry about this flexibility creating security issues, but security is actually improved since data isn’t stored locally on computers. Since VDI is controlled from a single point, it’s easy to monitor traffic and applying security patches becomes super easy.
On top of this additional layer of security, those that utilize VDI for remote, local, and hybrid workers get to enjoy cost savings because of the lack of hardware needed to run these environments.
Kiosk, Local, and Contract Workers
These kinds of workers perform repetitive tasks within a usually relatively small set of applications. These applications are usually not as memory intensive as applications used by knowledge workers. The most important aspect to kiosk, task, and contract workers is mobility. They need to access their applications but without all of the extra features associated with desktops usually.
Kiosk users include students using a shared computer in a classroom, nurses at nursing stations, and computers used for job placement and recruiting. Desktops like these require automatic login but authentication can be done through certain applications if necessary. Task users can utilize a terminal server setup and operate at full capacity.

It’s best to consider the types of applications that users run and the quality of the network they’re connecting over as well as the range of devices they will need or want to use. Contract workers usually require their own desktop, and thanks to VDI they’re able to utilize individual workspaces. This flexibility allows for full-stack solutions like those from VMware and Citrix — satisfying many users.
Customer support staff
It is becoming more and more popular for customer support staff to utilize cloud-native VDI (otherwise known as Cloud Desktops). Whether there's an office location or not, the ability to enable remote access for customer support staff has proven highly beneficial. Not only does it increase productivity, but it also reduces costs, simplifies device management, and even improves business operations.
Cloud desktops have lower latency than on-premise VDI which creates an improved connection quality and speed for employees on their devices. Latency is primarily determined by the distance from a device to the data center. There is a vast global network of these data centers, therefore employees are never too far from a data center. On-premise VDI usually requires one data center location for all employees around the globe. This distance usually causes latency issues that often impact customer support staff and service.
Considering customer support staff heavily relies on handling a high volume of phone calls, this saves time, increases efficiency, and improved customer satisfaction. Users get to utilize the dynamic scalability of resources. This feature enables things like easy onboarding and offboarding so new employees can hit the ground running and so much more.
Bring Your OWn Device (BYOD) Deployments
Desktop Virtualization allows employers to piggyback off of BYOD and save lots of money doing sp. This increases flexibility and security of a remote workers and those in office. With BYOD, employees can utilize their own devices with dual-factor authentication to access VDI. Once they’re logged in, a view of the desktop screen will be transferred to their local device. This allows organizations to enjoy streamlined management, cost efficiencies, and improved functionality.

Without relying on the horsepower of endpoint devices, virtual desktops that function in this capacity allow their IT department to increase the life of existing PCs. It is also one way to enjoy the benefits that VDI has to offer while staying cost-effective — and this cost-effective bonus doesn’t mean less security either!
Graphic Intensive Applications
For organizations that utilize manufacturing or oil exploration applications that are graphics-heavy (like AutoCAD or Kingdom), adding a High-Definition Experience (HDX) service enables virtual desktop users to experience consistency across a wide platform of supported devices and networks.
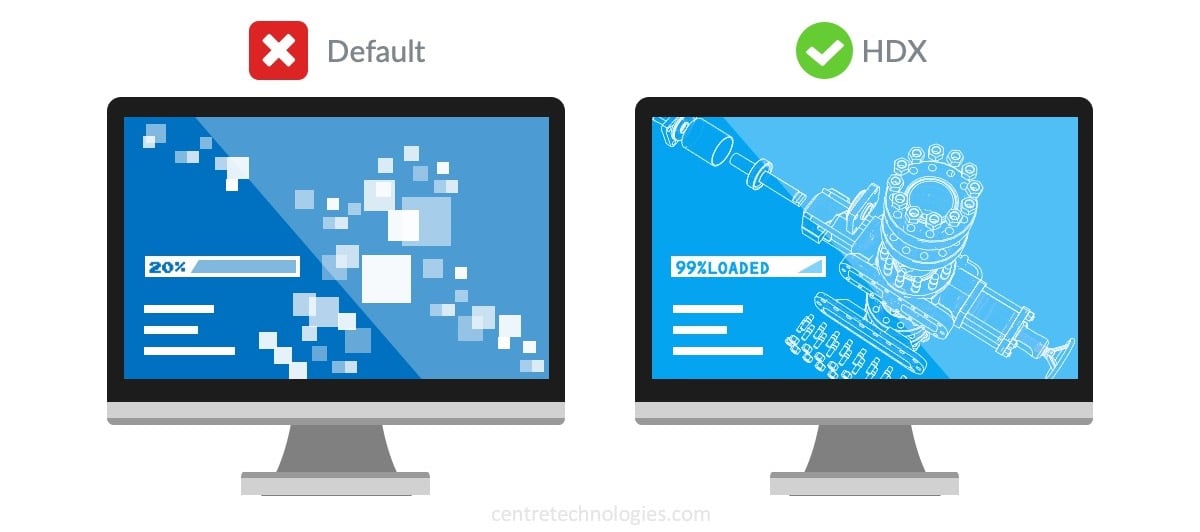
With HDX services, all user sessions maintain their performance, even if network characteristics change. Enabling display optimization by utilizing long-haul connections, while maintaining server scalability, ensures optimum performance and productivity. These sessions can be seamlessly switched without any additional configuration needed. Therefore, a highly responsive session can be provided for a variety of endpoints and devices.
Virtualizing 3D engineers, geoscientists, graphic designers, and business professionals alike allows for increased productivity, collaboration, flexibility, and availability no matter where they are located. Because virtual desktop interface has evolved over the years, it is no longer restricted to desktops with minimum resolutions and now holds the capacity of outputting quality high resolution for numerous desktops.
Work with Remote Desktop Support to Build and Manage a Bring-Your-Own-Device Policy
Our world has made a massive shift into the digital environment since the COVID-19 pandemic began. This means that more businesses have moved their workplace and products online. Bring-your-own-device (BYOD) policy goes hand-in-hand with remote desktop work, with employees using personal devices to connect to their organization’s network and access their data. While BYOD policy can improve employee productivity, if left unaddressed by your IT team, it can present challenges. Read on as discuss how remote desktop support is capable of improving your company’s experience with personal devices by integrating them with acceptable use policies and IT security.
Challenges of BYOD Policy
Whether you are a small business or an enterprise, you must exert some level of control over devices that are not owned by you. When it comes to your IT department, there must be an adequate number of staff members for remote desktop support issues that may arise. BYOD policy places more complex responsibility on your support team because there are greater risks of vulnerability to your company’s data. Of those that don’t plan on adopting BYOD policy in the near future, the most common reason is security concerns. For instance, your employees may not have anti-virus software or firewalls on every device they are using.
There also comes the headache of the lack of uniformity of devices. Perhaps everyone is using a Mac except for one person who is using Windows. This may lead to operating issues, which will require your team to learn two different operating procedures. When your business provides the same devices to all employees, there is less disruption. In the same vein, when it comes to software, BYOD policy isn’t a one-size-fits-all solution. Finding software programs that work conveniently for everyone can be frustrating, on top of the eventual differences in upgrades. While outsourcing your IT to Software as a Service (SaaS) is the easiest measure you can take, your employees still may struggle to use their devices.
Benefits of BYOD Policy
If your remote desktop support team is prepared to take on the necessary additional security measures, a BYOD policy can help out your business with the struggle that is not being with everyone. Over half of today’s highest-performing, customer-oriented companies are authorizing the use of personal devices both at home and in the office. By allowing employees to use their own devices from home, there is an increase in their productivity and job satisfaction. The flexible work arrangements and comfort with their devices mean lower technology costs for your business. After all, with the cost of a device shifting from the company to the employee, so does the data plan, regular updates, and insurance.
In a study done by Samsung and Oxford Economics, 80% of American senior executive respondents claimed that their employees need their mobile phones in order to work effectively. Approximately 75% of them said that mobile devices are important for their workflows. Despite this, the survey reported that only 17% of organizations provide mobile devices to all of their employees. If your business is opting to go the BYOD route, mobile device management (MDM) solutions offer simultaneous freedom for employees and control for employers. Components include application and endpoint security, identity and access management (IAM), and device tracking. With MDM tools to deal with monitoring and troubleshooting, a BYOD policy can run much smoother.
Remote Desktop Support Objectives and Procedures
Once you have decided to implement a BYOD policy, also create a data classification policy. This provides a way to ensure that all information is handled properly. It should include the confidential data of your customer relationship management (CRM) and financial reports, the internal data of your API keys and encryption keys, and the public data of your business details that anyone can find on your website. You will be able to leverage tools that can streamline the classification process by categorizing data based on your parameters. While you can easily categorize some information, using automation technology to analyze large data sets quickly will serve you well in all aspects of your business.
Set clear expectations with your employees. The lines of their privacy can get blurry when you are enforcing controls on their personal devices. So, articulating your aims for technology usage from the beginning is important. Remote workers should be aware of what kinds of data they can and cannot access and send through their personal devices. It only takes one person to accidentally cause a data breach. A multifaceted BYOD policy will effectively separate company and personal data by providing specialized apps with multi-factor authentication. Employees must also know that, upon termination, their devices will be wiped of company data to keep sensitive information secure.
Consider Your Technology Capabilities
Once again, recognize that not all solutions are compatible with your operating systems and devices. Your two options, in this case, are to offer different solutions for each type or purchase solutions with cross-device compatibility. By evaluating your current technology capabilities, you can fill the gaps to develop a successful BYOD policy. Your business should also work with your remote desktop support team to determine the best security solutions. Cloud storage is a great way to give employees access to internal documents. However, the controls are dependent on the provider. Before leaving the cloud open, have some discussion with the provider about leveraging additional technical controls to enforce your BYOD policy.
Cloud storage is a convenient way to give your employees access to internal files. An example of this is the cloud-based service of Microsoft Intune. With this, you can better manage personal devices. Administrators will be able to configure them to meet your security standards. They can remove sensitive data if it is lost, push certificates for easy network connection, and see a clear inventory of devices accessing resources. Microsoft Intune focuses on MDM and mobile application management (MAM), and integrates with Azure Active Directory and Azure Information Protection. Is your business is comfortable with using the Microsoft 365 suite for daily tasks? Then, this feature will only add to your experience.
Manage Your Policy with Security Solutions
Cybercrime is a prime concern of remote desktop support. When developing security solutions that are specific to your BYOD policy, explain what acceptable use means to you. From there, you can determine what applications your employees should be using. Blacklisting is the process of prohibiting applications that clearly pose a security risk. A blacklist can never be comprehensive, due to new threats constantly emerging. That being said, threat information sharing can help make them more effective. Whitelisting takes the opposite approach of providing a list of approved applications. To create a network-level whitelist, consider the tasks that the users need to perform and what tools they need to complete them. Your whitelist will include things like infrastructure, websites, and services, as well as plugins, extensions, and configuration files.
Set your employees on the right track with accountability provisions. Your BYOD policy needs to explain how accountability will be measured and enforced. You can avoid basic problems with the incorporation of employee security awareness training. This is a recurring program that you can have either online or in-person. Its intention is to provide employees with a strategy for responding to cyber incidents and how to mitigate them. Some ways to get them more engaged are to do simulated phishing campaigns, focus on situations that are commonly faced in your industry, or even offer certification upon completion. The end goal should be to provide content that will stick with them.
Hire Centre Technologies for Virtual Desktop Services
BYOD solutions can create efficiencies in your workplace, but they also introduce vulnerabilities. Before you kick off a BYOD policy, think about what impact it could have on your business in the future. If you have the right safeguarding systems in place to protect your company data, then it can be a great option for your small or medium business. At Centre Technologies, we operate with integrity and professionalism to reduce the cost of managing your IT for remote desktop support and beyond.
The most significant contribution to improving your bottom line is keeping your workforce productive through all kinds of challenges. With Centre Technologies, you can virtualize your desktops, host accounts, applications and operating systems in the cloud. This enables you to scale your organization quickly and securely without relying on individual devices.
At Centre Technologies, we want to help you maximize your systems and processes and create a digital transformation that helps you stay competitive and keep up with industry trends. Contact us today to learn more about our services and insights into innovative technologies.
Be a thought leader and share:
About the Author
Organizations partner with Centre to harness the benefits of cloud services and minimize the cost. Centre’s cloud services deliver comprehensive planning and dedicated support so customers can choose, navigate, and secure their cloud journey with confidence. With a focus on personalized solutions, Centre’s certified experts help customers achieve their business goals through public cloud services, private hosting options, or a combination of both. Learn more about Cloud Solutions »



