Elevating identity and access management to the digital era
by Fintechnews Switzerland December 2, 2015Identity and access management is no exception to the digitization of everything. The use of biometric features, behavioral aspects and physiological technologies is just around the corner, bringing new authentication and authorization methods to the market. Another wave of technology disruption or an actual business need?
by Maurice Bollag*, Senior Manager Ernst&Young
Era of digitalization and disruptive technology
The unprecedented explosion of technology disruption and innovation, the velocity of change and the tremendous impact on businesses are ultimately forcing a large number of industries to increase the pace at which they do business and transform technology. At the same time, the need for increased data and information protection cannot be overstated.
The recent Ashley Madison hack (stolen personal information from a website dedicated to matching up people who want to engage in extramarital affairs) is prime evidence that the management of identities and accesses goes beyond the purpose of regulatory and security compliance. It impacts the society as a whole and plays an important role in today’s cyber ecosystem.
Cyber threats
Identity and access management must be re-aligned with today’s digital and cyber eco-system. With the digitization of everything, the classical perimeter of an organization is disappearing, leading to an increased and complex exposure to potential cyber threats. The range of the perimeter now includes the authentication and authorization to and from the corporate organization or the multiple types of users (e.g., employees, customers, business partners, third parties and suppliers) through multiple channels.
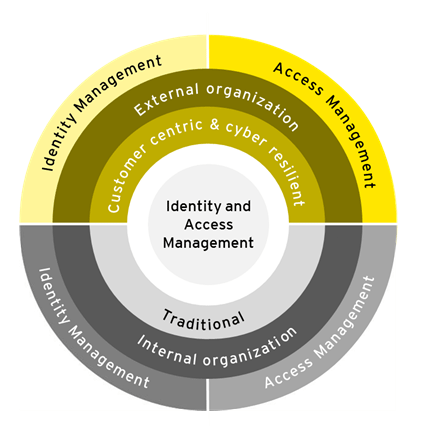
Customer-centric and resilient to cyber identity fraud
Traditionally, organizations have managed their identities and accesses primarily by focusing on the internal employees accessing corporate-wide internal applications. For many organizations, this remains an actual challenge, which requires continuous funding and available skills to maintain a sustainable state.It is therefore not surprising that identity and access management continues to be a key priority on the agenda of information security.
With the new reality of a digital and cyber ecosystem, organizations have no other choice but to extend the scope of identity and access management with the additional two aspects 1) customer-centric (especially for the external types of users who are accessing their trusted organizations) and 2) resilient to cyber identity fraud.
1. Customer-centric
Customer behavior is changing in many ways. The following two examples highlight the reasons why a customer-centric identity and access management is key to building and retaining customer trust in the organization they are working with:
a) End user acceptance and usability of usernames and passwords
In the digital ecosystem, customers have to manage multiple interconnected identities. This makes it very challenging to use the traditional management of usernames and passwords. Customers are getting tired of and increasingly frustrated with the tedious and inconvenient processes involved in managing those identities. The Millennial Generation (also known as Gen Y) might have been used to it, but the subsequent Generation Z will certainly not accept it.Can we image how Gen Z would feel about accepting the use of indefinite usernames and passwords to enable their access to a web service? Will Gen Z accept having to prove who they are instead of being recognized automatically (authentication based on who they are, not what they re-member)?
b) Increased customer awareness of security reliability
Society has become more aware of the risks related to information security. Customers are feeling less secure about the reliability of usernames and passwords to protect their personal data.
Even good habits and best practices of password management (e.g., different and strong passwords for each used service) are no longer secure and effective enough to protect from identity fraud and theft. Analysis of root cause for identity fraud and theft incidents often includes a flawed authentication method. Therefore, providing customer-centric identity and access management will become a key factor in ensuring customer satisfaction and trust.
2. Resilient to cyber identity fraud
Indeed, breaches have been occurring for a long time, but their impacts have never been so severe. Incidents which are directly or indirectly related to weak management of identities and accesses are becoming a persistent business operational risk (e.g., damage to reputation, intellectual property, ability to serve customers, financial impact).
Regulations around the world are imposing rules, enforcing mandatory public disclosure of any breach (and even attempted breaches) that compromised personal or financial information and notification of affected consumers within a pre-defined timeline. Non-compliance will be subject to increased fines.
The recent Ashley Madison hack could not have been a better wake-up call. It impacts the society and can have consequences far worse than any financial impact. Customers will no longer accept and trust companies who cannot demonstrate their ability to protect personal data and privacy. Innovative solutions for authentication and authorization methods are emerging to disrupt current practice, but their success will depend on whether they arrive on the market with a pre-installed system for protecting data privacy.
Technology trends
A possible way to address this challenge is to deploy innovative authentication and authorization methods. Research has been conducted to predict the key developments and roadmap of cur-rent and future identity and access management technologies. At the end of the day, consumer perception of confidence and trust will play a key role in the success of each technology. The following list is an overview of the new methods:
Context-based
Authentication and authorization are driven by a risk context, taking into account criteria such as geographical location, physical device, time and duration of a user’s request to access a service. The measures of authentication and level of authorization dynamically change according to the actual contextual information and risk level.
Biometrics
Authentication and authorization are based on digitalized biometrics from a human being such as fingerprint, facial or voice recognition – methods that have actually been in place for many years. The latest bio-metric technologies include other physical human elements such as heartbeat frequency, vein, palm, iris, DNA, handwriting and even tattoos.
Behavioral
Authentication and authorization are based on personalized gestures such as hand-eye coordination, keystroke dynamics or cursor movements. Algorithms and patterns of interaction might be combined to set the behavioral criteria. Which technology will ultimately succeed is difficult to predict. A combination of different technologies might become the future best practice. The new technologies will have to prove their advantages before passwords become obsolete in the near future and assert themselves against emerging and future trends in password security (Password 2.0). However, what certainly can be predicted is that the cultural, geographical and industrial differences are going to play a key role. Offering choices of authentication methods for different locations and user populations might lead to a greater appeal and acceptance.
Cultural and geographical tendency
A global organization will have to consider the cultural differences in the region they operate in and its online customer base. We have seen countries which have emerged and directly embraced new technologies. Others, however, have adapted their technology, but face challenges due to a lack of user acceptance.
Industry tendency
The question is “how” rather than “which” specific industry will be impacted. The following examples from three industries highlight the differences relating to the “how”: the banking industry, which has been dealing with identity and access management for a while, the automobile industry and the smart home industry. The last two are becoming increasingly relevant to our private lives.
Banking
The strongly regulated financial industry has improved its capabilities of managing its identities and accesses over the last couple of years. Nonetheless, a digital banking business model requires massive adaption to its identity and access management methods to support upcoming digital banking services. Mobile and peer-to-peer payments, crowd funding as well as trading and lending functions need to be customer-centric and resilient to cyber identity fraud.
Automobile
Connected cars have to offer simple and secured authentication and authorization methods. For example, access to the car could be provided based on biometric data such as fingerprints. Car owners might need to think about authentication and authorization in the future, but car producers definitely must start to integrate secure and easy to use security functions.
Smart home
Last but not least, society will have to start thinking about authentication and authorization of their digitized home rooms, devices and furniture.
Three actions to be taken to-day
The industries and organizations need to start extending the scope of their current identity and access management model and elevating it to the digital era by:
Assessing the current state and evaluating its current digital transformation journey to include adapted identity and access management methods.
Assessing their ability to detect identity fraud and threats and readiness to respond to potential incidents.
Reviewing the current technology, operating model and governance to effectively and efficiently include integral identity and access management beyond the purpose of regulatory and security compliance.
Conclusion:
The new authentication and authorization technologies have tremendous potential. It is a business and a customer need. A business need for a robust resilience against identity fraud and cyber threats.
A customer need for a more convenient and trusted method of authentication and authorization. With the speed at which the digitalization process is taking place, it will not be long until we find out which emerging technology will assert itself.
However, the challenge remains to intro-duce these new technologies with a water-tight protection of data privacy.
This article has been first published on Linkedin
 *Maurice works as a Senior Manager at EY (former Ernst & Young AG) in EMEIA Financial Services Advisory, IT Risk and Assurance & IT Advisory. He is a FINTECH advisor specialized in Cyber, IT and Information Security, IT Risk and IT Service Management.
*Maurice works as a Senior Manager at EY (former Ernst & Young AG) in EMEIA Financial Services Advisory, IT Risk and Assurance & IT Advisory. He is a FINTECH advisor specialized in Cyber, IT and Information Security, IT Risk and IT Service Management.







No Comments so far
Jump into a conversationNo Comments Yet!
You can be the one to start a conversation.