
Some of the world's leading websites—including those owned or operated by Bank of America, VMware, the US Department of Veteran's Affairs, and business consultancy Accenture—are vulnerable to simple attacks that bypass the transport layer security encryption designed to thwart eavesdroppers and spoofers.
The attacks are a variation on the so-called POODLE exploits disclosed two months ago against secure sockets layer (SSL), an encryption protocol similar to transport layer security (TLS). Short for "Padding Oracle On Downgraded Legacy Encryption," POODLE allowed attackers monitoring Wi-Fi hotspots and other unsecured Internet connections to decrypt HTTPS traffic encrypted by the ancient SSL version 3. Browser makers quickly responded by limiting or eliminating use of SSLv3, a move that appears to have averted widespread exploitation of the bug.
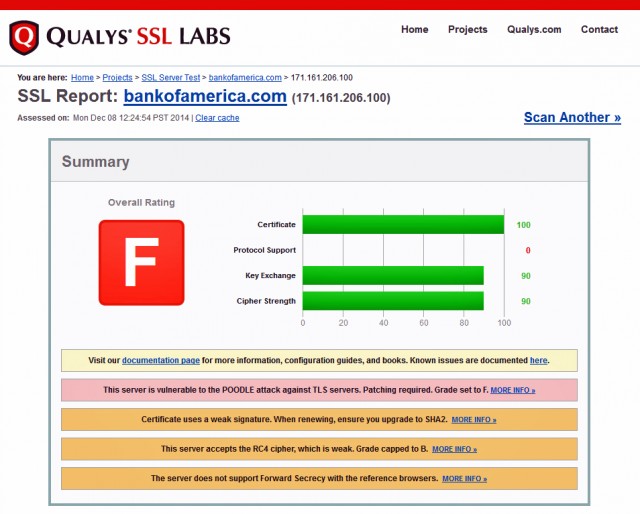
On Monday, word emerged that there's a variation on the POODLE attack that works against widely used implementations of TLS. At the time this post was being prepared, SSL Server Test, a free service provided by security firm Qualys, showed that some of the Internet's top websites—again, a list including Bank of America, VMware, the US Department of Veteran's Affairs, and Accenture—are susceptible. The vulnerability was serious enough to earn all sites found to be affected a failing grade by the Qualys service.
Update: An Accenture representative said that accenture.com, the site receiving a failing grade from Qualys, doesn't serve content, but rather redirects all traffic through its content delivery network www.accenture.com which Qualys shows as not being vulnerable to POODLE-style attacks.
Stealing cookies, one crumb at a time
As concerning as POODLE was to security professionals, it required attackers to follow several steps that could often prove difficult in real-world environments. Attackers had to spoof packets sent between websites and end users to force them to use SSLv3. It also required attackers to slightly modify transactions thousands of times until they could successfully guess the contents of encrypted payloads, one character at a time. By using the padding oracle to deduce the contents of the payloads, attackers could obtain authentication cookies or security tokens used to gain access to user accounts or other restricted sections of a vulnerable website. The newly disclosed attack against TLS is similar, except that it's slightly less demanding to carry out.
"The impact of this problem is similar to that of POODLE, with the attack being slightly easier to execute—no need to downgrade modern clients down to SSL 3 first, TLS 1.2 will do just fine," Ivan Ristic, Qualys's director of application security research, wrote in a blog post titled POODLE bites TLS. "The main target are browsers, because the attacker must inject malicious JavaScript to initiate the attack. A successful attack will use about 256 requests to uncover one cookie character, or only 4096 requests for a 16-character cookie. This makes the attack quite practical."
So far, load balancers and similar devices sold by two different manufacturers have been identified as vulnerable. The makers are F5 and A10. Although recent versions of TLS calls for the encryption padding to be closely checked for so-called Oracle attacks, the companies' implementations skip this step, making them vulnerable to POODLE-style exploits. F5 has issued an advisory detailing precisely which products are vulnerable and showing how they can be patched. The status of a fix from A10 wasn't immediately known.
According to Ristic, about one in 10 websites are vulnerable to the new POODLE attack for TLS. That means 10 percent of sites are vulnerable to man-in-the-middle attacks that face a reasonable chance of success bypassing Web encryption. Users are invited to use the Qualys service to identify other high-profile sites that are vulnerable. Administrators should waste no time ensuring their sites aren't affected.
reader comments
35